# Create an HTTP connection
You must set up your connection to the app you plan to use before you can configure HTTP triggers and actions.
The steps required to create an HTTP connection in Workato vary based on the authentication type you plan to use. The HTTP connector supports the following authentication types:
- None
- Basic
- Header auth
- Query params
- Custom
- OAuth2 (authorization code grant)
- OAuth2 (client credentials grant)
- AWS access key auth
- AWS IAM role auth
- Azure OAuth 2 (authorization code grant)
- Azure OAuth 2 (client credentials grant)
# None authentication type
The None authentication type enables you to create a connection without providing authentication details. Use this authentication type when you plan to receive a webhook trigger from an app. Workato generates a URL to direct your webhooks to, and retrieves information from the webhook payload.
Complete the following steps to set up an HTTP connection with the None authentication type:
Provide a Connection name that identifies your HTTP instance.
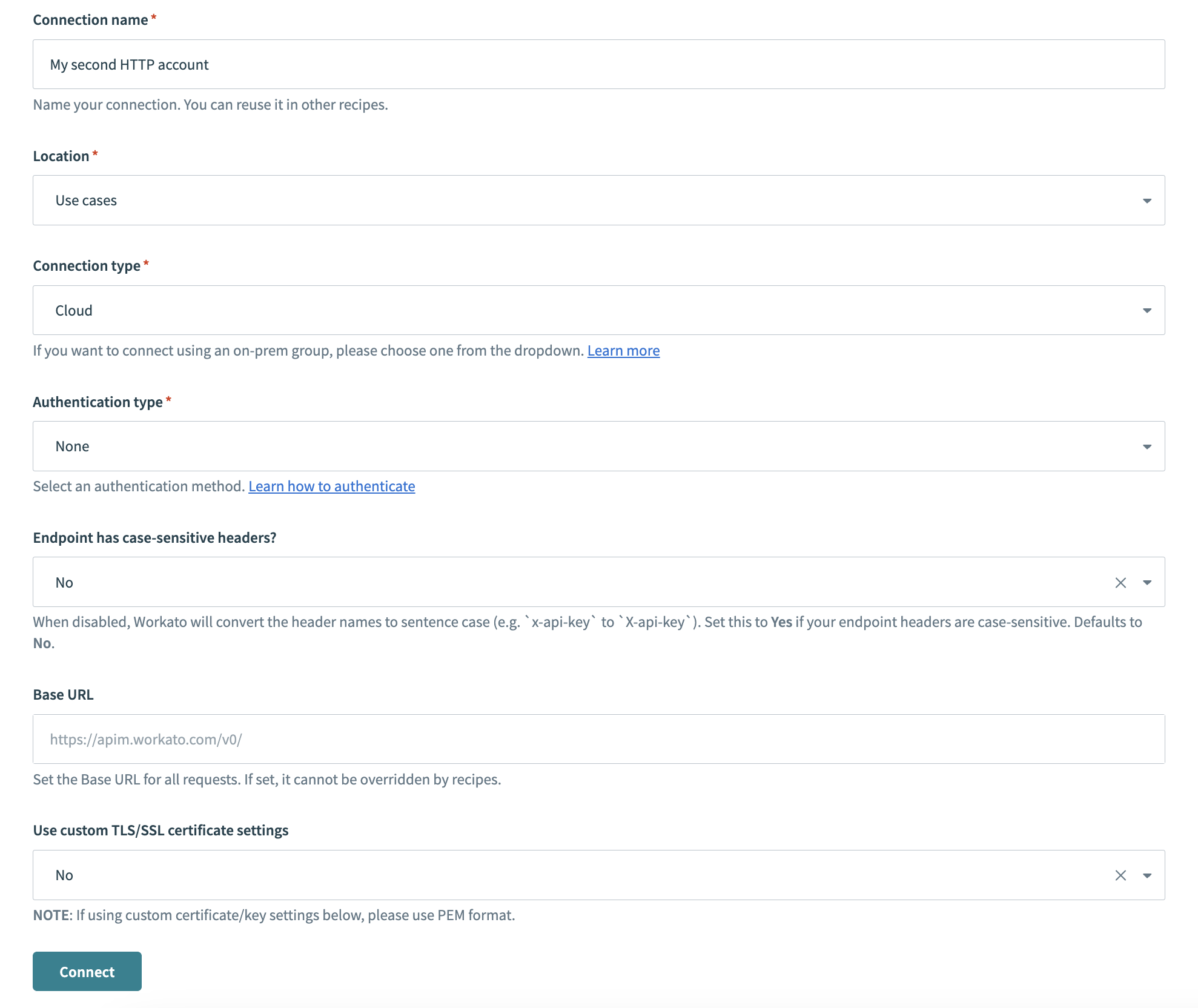 HTTP connector authentication type: None
HTTP connector authentication type: None
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Connection type drop-down menu to select the connection type you plan to use.
Use the Authentication type drop-down menu to select None.
Use the Endpoint has case-sensitive headers? drop-down to set the case sensitivity for your connection.
Provide your base URL in the Base URL field. Recipes can't override this setting.
Use the Use custom TLS/SSL certificate settings drop-down menu to determine your certificate settings.
Click Connect.
# Basic authentication type
The Basic authentication type requires your username and password. As an alternative to your username and password, you can use an API key or API token retrieved from your account settings. This is a common authentication flow encoded with Base64 in transit over SSL.
Provide a Connection name that identifies your HTTP instance.
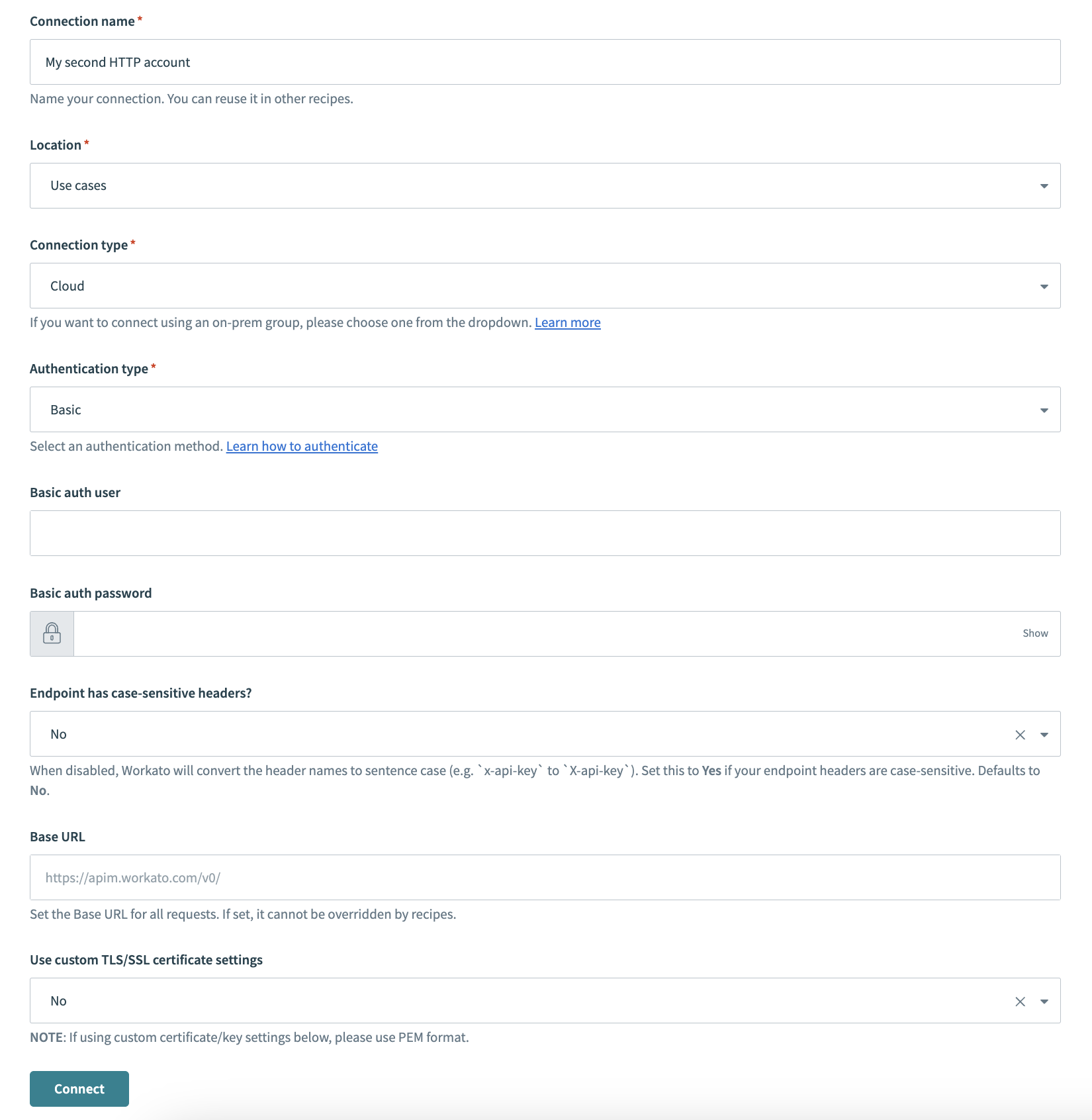 HTTP connector authentication type: Basic
HTTP connector authentication type: Basic
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Connection type drop-down menu to select the connection type you plan to use.
Use the Authentication type drop-down menu to select Basic.
Provide your user authentication name in the Basic auth user field.
Provide your user authentication password in the Basic auth password field.
Use the Endpoint has case-sensitive headers? drop-down menu to set the case sensitivity for your connection.
Provide your base URL in the Base URL field. Recipes can't override this setting.
Use the Use custom TLS/SSL certificate settings drop-down menu to determine your certificate settings.
Click Connect.
# Header auth authentication type
The Header auth authentication type enables you to customize the headers sent in a request. This is useful if your app requires additional headers beyond the standard username and password or API key. You can also use this authentication type if you have a generated token.
Complete the following steps to create an HTTP connection with the Header auth authentication type:
Provide a Connection name that identifies your HTTP instance.
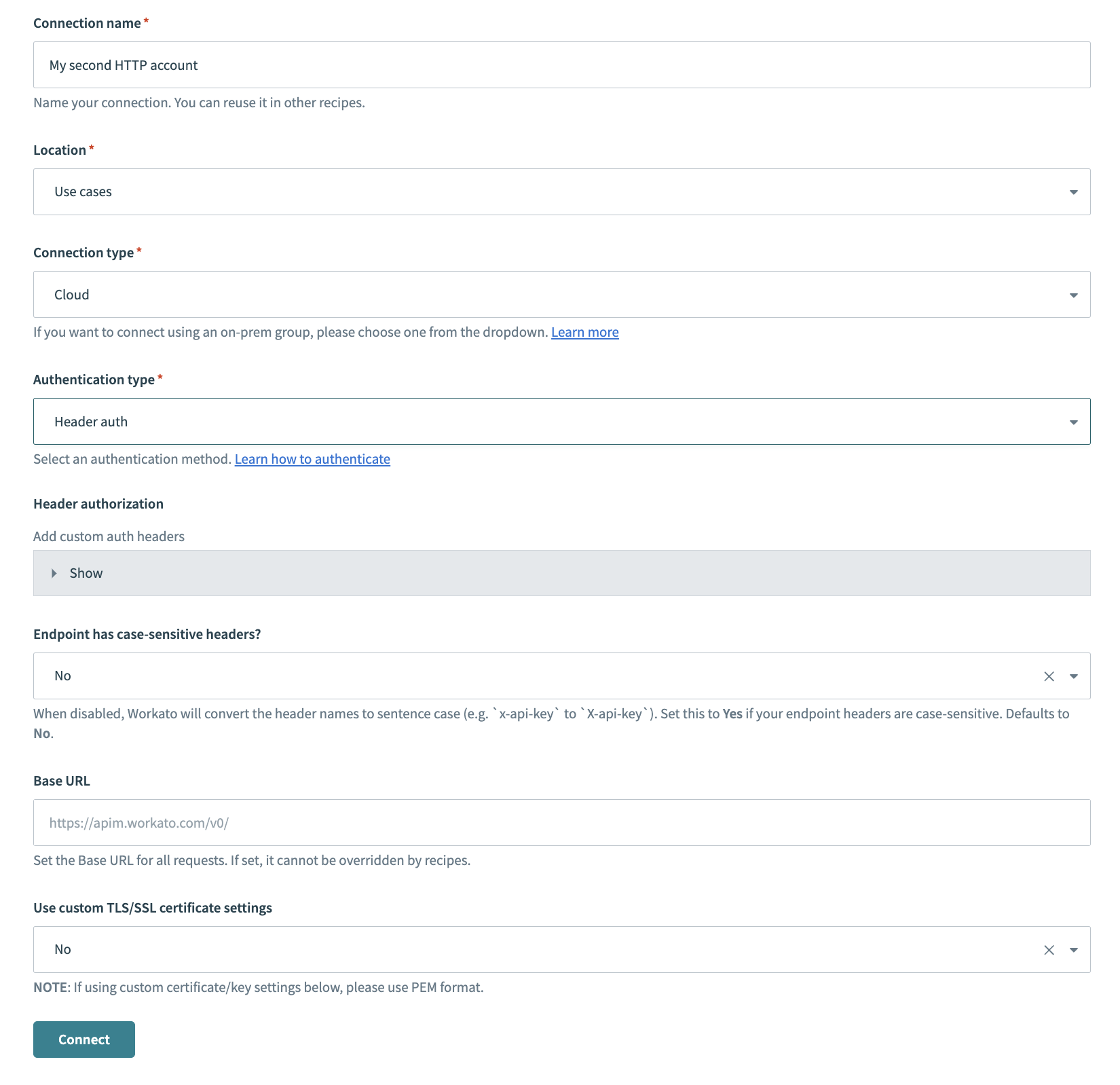 HTTP connector authentication type: Header authorization
HTTP connector authentication type: Header authorization
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Connection type drop-down menu to select the connection type you plan to use.
Use the Authentication type drop-down menu to select Header auth.
Optional. Expand Header authorization to add custom auth headers.
Use the Endpoint has case-sensitive headers? drop-down menu to set the case sensitivity for your connection.
Provide your base URL in the Base URL field. Recipes can't override this setting.
Use the Use custom TLS/SSL certificate settings drop-down menu to determine your certificate settings.
Click Connect.
# Query params authentication type
Use the Query params authentication type when you plan to use applications that require a validated API key as a parameter.
Provide a Connection name that identifies your HTTP instance.
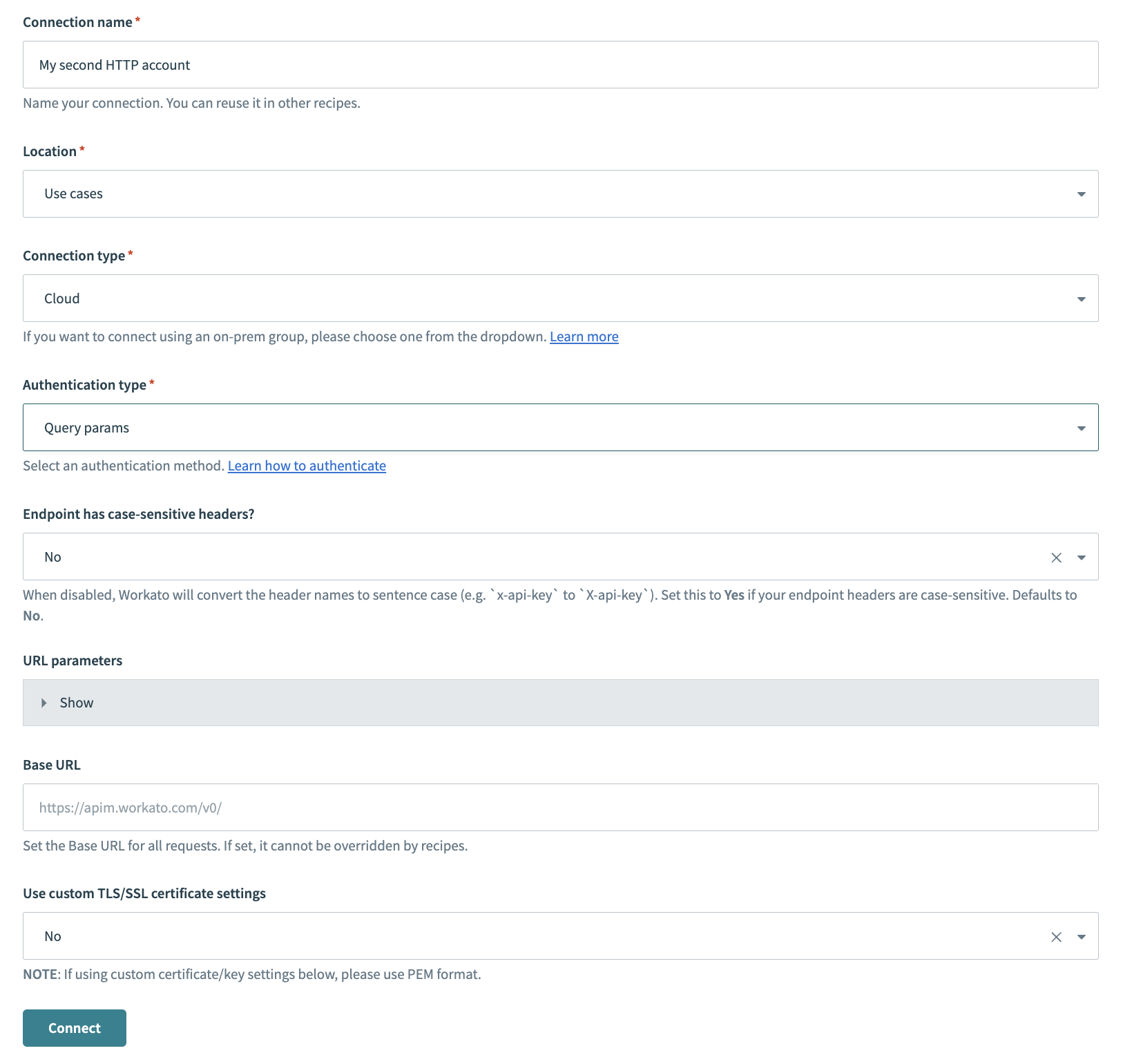 HTTP connector authentication type: Query params
HTTP connector authentication type: Query params
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Connection type drop-down menu to select the connection type you plan to use.
Use the Authentication type drop-down menu to select Query params.
Use the Endpoint has case-sensitive headers? drop-down menu to set the case sensitivity for your connection.
Optional. Expand Url parameters to add URL parameters.
Provide your base URL in the Base URL field. Recipes can't override this setting.
Use the Use custom TLS/SSL certificate settings drop-down menu to determine your certificate settings.
Click Connect.
# Custom authentication type
The Custom authentication type enables you to use a tailored combination of input fields to satisfy custom authentication requirements.
Provide a Connection name that identifies your HTTP instance.
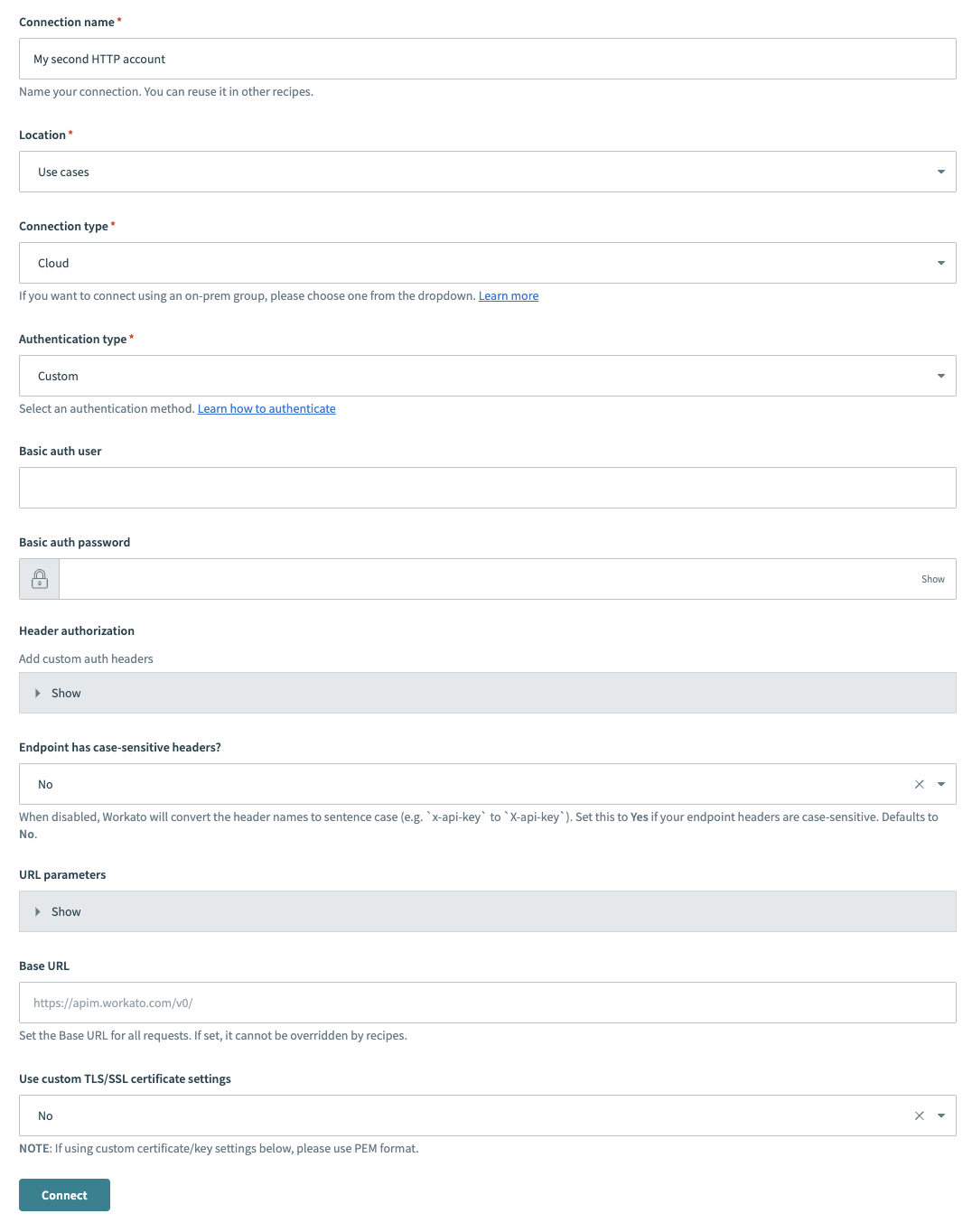 HTTP connector authentication type: Custom
HTTP connector authentication type: Custom
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Connection type drop-down menu to select the connection type you plan to use.
Use the Authentication type drop-down menu to select Custom.
Optional. Provide your user authentication name in the Basic auth user field.
Optional. Provide your user authentication password in the Basic auth password field.
Expand Header authorization to add custom auth headers.
Use the Endpoint has case-sensitive headers? drop-down menu to set the case sensitivity for your connection.
Expand Url parameters to add URL parameters.
Provide your base URL in the Base URL field. Recipes can't override this setting.
Use the Use custom TLS/SSL certificate settings drop-down menu to determine your certificate settings.
Click Connect.
# On-prem NTLM authentication type
Use the NT LAN Manager (NTLM) authentication type if you have a configured Workato on-prem agent and the application you plan to use requires NTLM authentication.
Complete the following steps to set up your HTTP connection with NTLM authentication:
Provide a Connection name that identifies your HTTP instance.
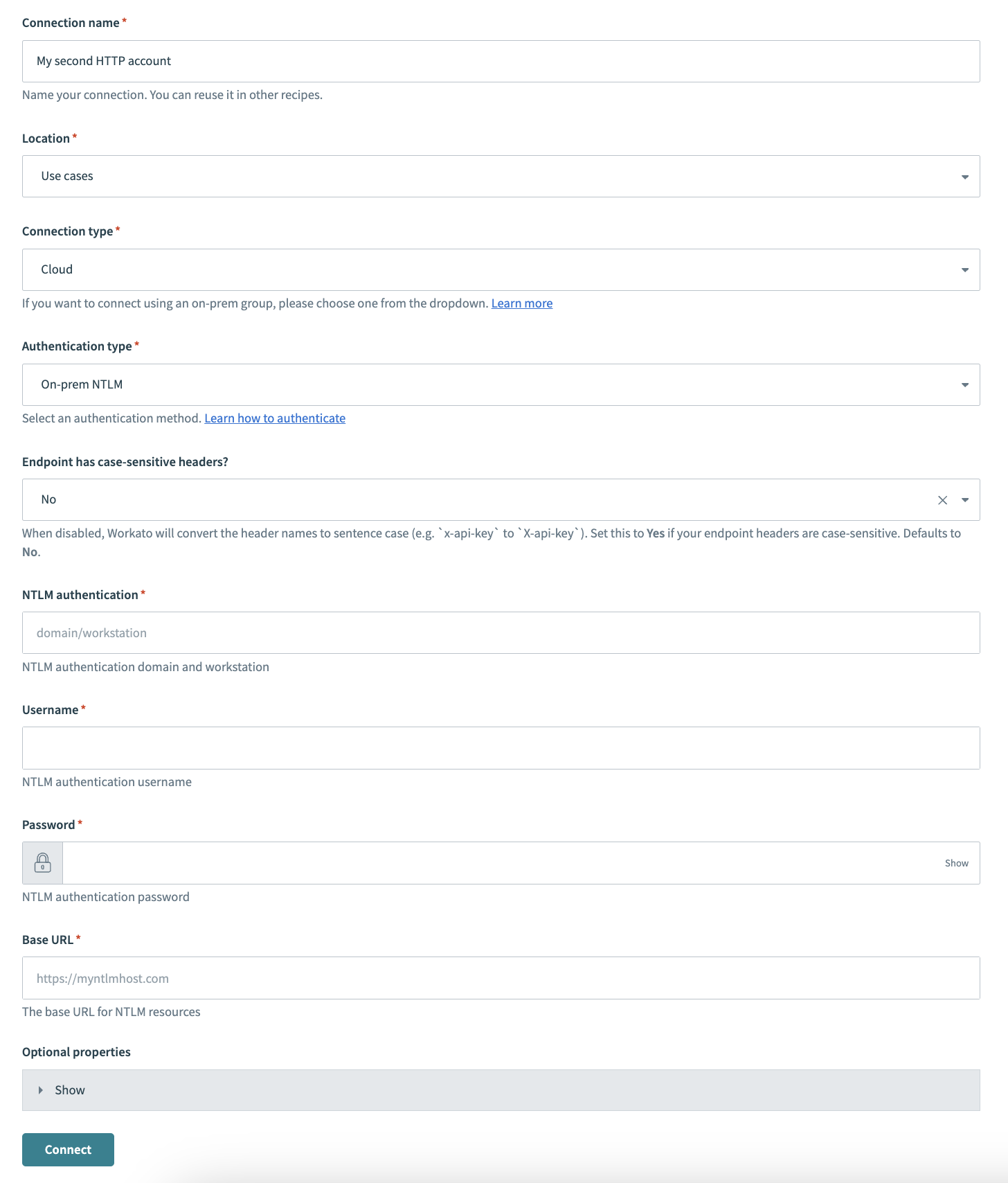 HTTP connector authentication type: On-prem NTLM
HTTP connector authentication type: On-prem NTLM
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Connection type drop-down menu to select the connection type you plan to use.
Use the Authentication type drop-down menu to select On-prem NTLM.
Use the Endpoint has case-sensitive headers? drop-down menu to set the case sensitivity for your connection.
Provide your NTLM authentication domain or workstation name in the NTLM authentication field.
Provide your NTLM authentication username in the Username field.
Provide your NTLM authentication password in the Password field.
Optional. Expand Optional properties to configure additional profile properties.
Click Connect.
The following profile properties are supported:
| Property name | Description |
|---|---|
| NTLM authentication | NTLM authentication domain and workstation name. |
| Username | Username for NTLM authentication. |
| Password | Password for NTLM authentication. |
| Base URL | The base URL for NTLM resources. |
| Connections per route | Optional. Sets the number of connections per route/host (must be a positive number, default 5). |
| Maximum connections | Optional. Sets the maximum number of connections (must be a positive number, default 10). |
| Timeout | Optional The timeout in milliseconds used when requesting a connection (must be a positive number, default 10000). |
| Connection request timeout | Optional The timeout in milliseconds until a connection is established (must be a positive number, default 10000). |
| Socket timeout | Optional The socket timeout in milliseconds, which is the timeout for waiting for data or, put differently, a maximum period inactivity between two consecutive data packets (must be a positive number, default 10000). |
| Verify host | Optional. Specifies whether to enable verification of the host name for SSL/TLS connections (default true). |
| Trust all | Optional. Specifies whether trust all certificates for SSL/TLS connections (default false). |
Refer to the following list for supported HTTP methods for NTLM connections:
GETPOSTPUTPATCHDELETEHEAD
Refer to the connection profiles documentation if your on-prem group connections use config.yml.
# OAuth 2.0 authorization code grant authentication type
The OAuth 2.0 authorization code grant authentication type enables you to provide third parties with access to your apps without disclosing your username and password. Confidential and public clients use this authentication type to exchange an authorization code for an access token. Workato redirects you to your app to enter your login credentials when you use this authentication type. This enables Workato to act on your behalf when making API requests.
Complete the following steps to set up your HTTP connection with OAuth 2.0 authorization code grant authentication:
Provide a Connection name that identifies your HTTP instance.
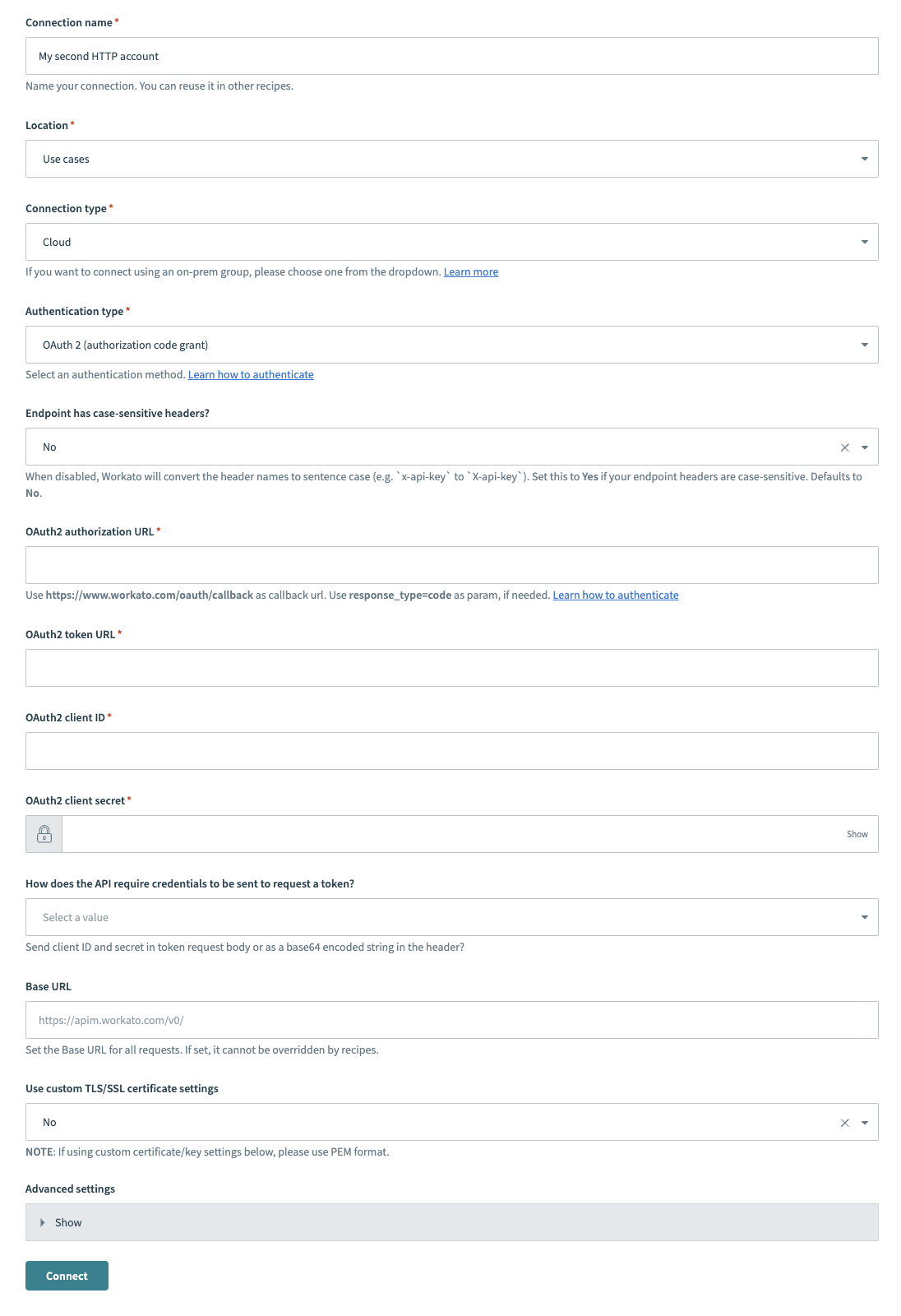 HTTP (OAuth2 authorization code grant) connector's connection fields
HTTP (OAuth2 authorization code grant) connector's connection fields
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Connection type drop-down menu to select the connection type you plan to use.
Use the Authentication type drop-down menu to select OAuth 2 (authorization code grant).
Use the Endpoint has case-sensitive headers? drop-down menu to set the case sensitivity for your connection.
Provide your authorization URL in the OAuth2 authorization URL field.
Provide your token in the OAuth2 token URL field. This auth token is used to verify that Workato has permission to access your app.
Provide your client ID in the OAuth2 client ID field. The client ID identifies you as the user who’s sending the API requests.
Use the How does the API require credentials to be sent to request a token? drop-down menu to determine whether to send the client ID and secret in the token request body or as a base64 encoded string in the header.
Provide your base URL in the Base URL field. Recipes can't override this setting.
Use the Use custom TLS/SSL certificate settings drop-down menu to determine your certificate settings.
Optional. Expand Advanced settings to configure OAuth2 scopes and token settings.
Click Connect.
# OAuth 2.0 client credentials grant authentication type
Use the OAuth 2.0 client credentials grant authentication type if you plan to enable the client to request an access token using only client credentials. This authentication type is usually used when the client is requesting access to the protected resources under its control or for machine-to-machine authentication where a specific user’s permission to access data is not required. The client credentials grant type can only be used by confidential clients.
Complete the following steps to set up your HTTP connection with OAuth2 client credentials grant authentication:
Provide a Connection name that identifies your HTTP instance.
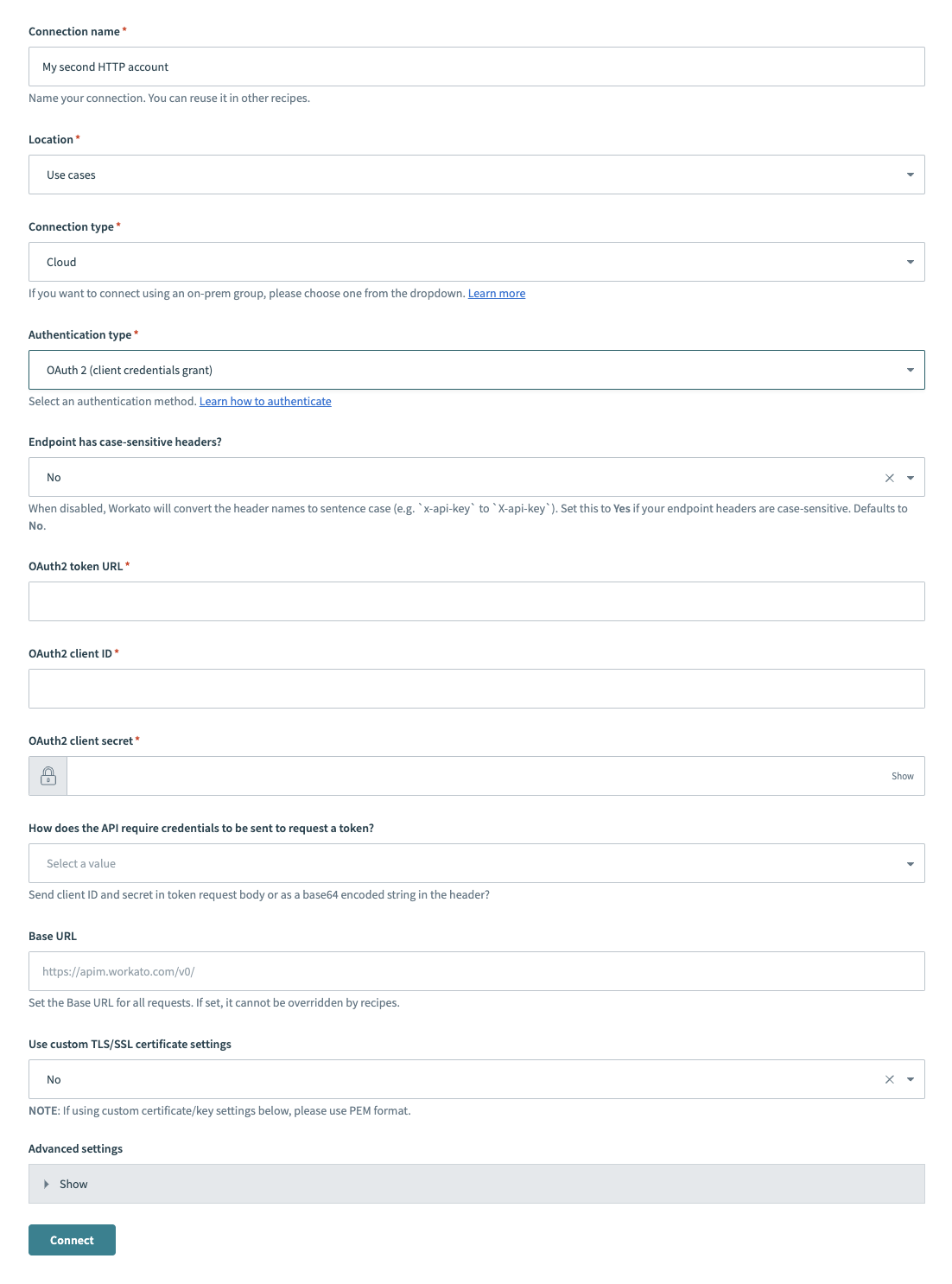 HTTP (OAuth2 client credentials grant) connector's connection fields
HTTP (OAuth2 client credentials grant) connector's connection fields
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Connection type drop-down menu to select the connection type you plan to use.
Use the Authentication type drop-down menu to select OAuth 2 (client credentials grant).
Use the Endpoint has case-sensitive headers? drop-down menu to set the case sensitivity for your connection.
Provide your OAuth2 token URL in the OAuth2 token URL field.
Provide your client ID in the OAuth2 client ID field.
Provide your client secret in the OAuth2 client secret field.
Use the How does the API require credentials to be sent to request a token? drop-down menu to determine whether to send the client ID and secret in the token request body or as a base64 encoded string in the header.
Provide your base URL in the Base URL field. Recipes can't override this setting.
Use the Use custom TLS/SSL certificate settings drop-down menu to determine your certificate settings.
Optional. Expand Advanced settings to configure OAuth2 scopes.
Click Connect.
OAuth2 client credentials grant example
# Connect to Eventbrite with OAuth 2.0 client credentials grant
Go to the app's documentation page to obtain your authorization URL and the access token URL. You must append additional parameters to the URL as specified by the app. For example, Eventbrite requires the following format for a post request:
https://www.eventbrite.com/oauth/authorize?response_type=code&client_id=YOUR_CLIENT_KEY`
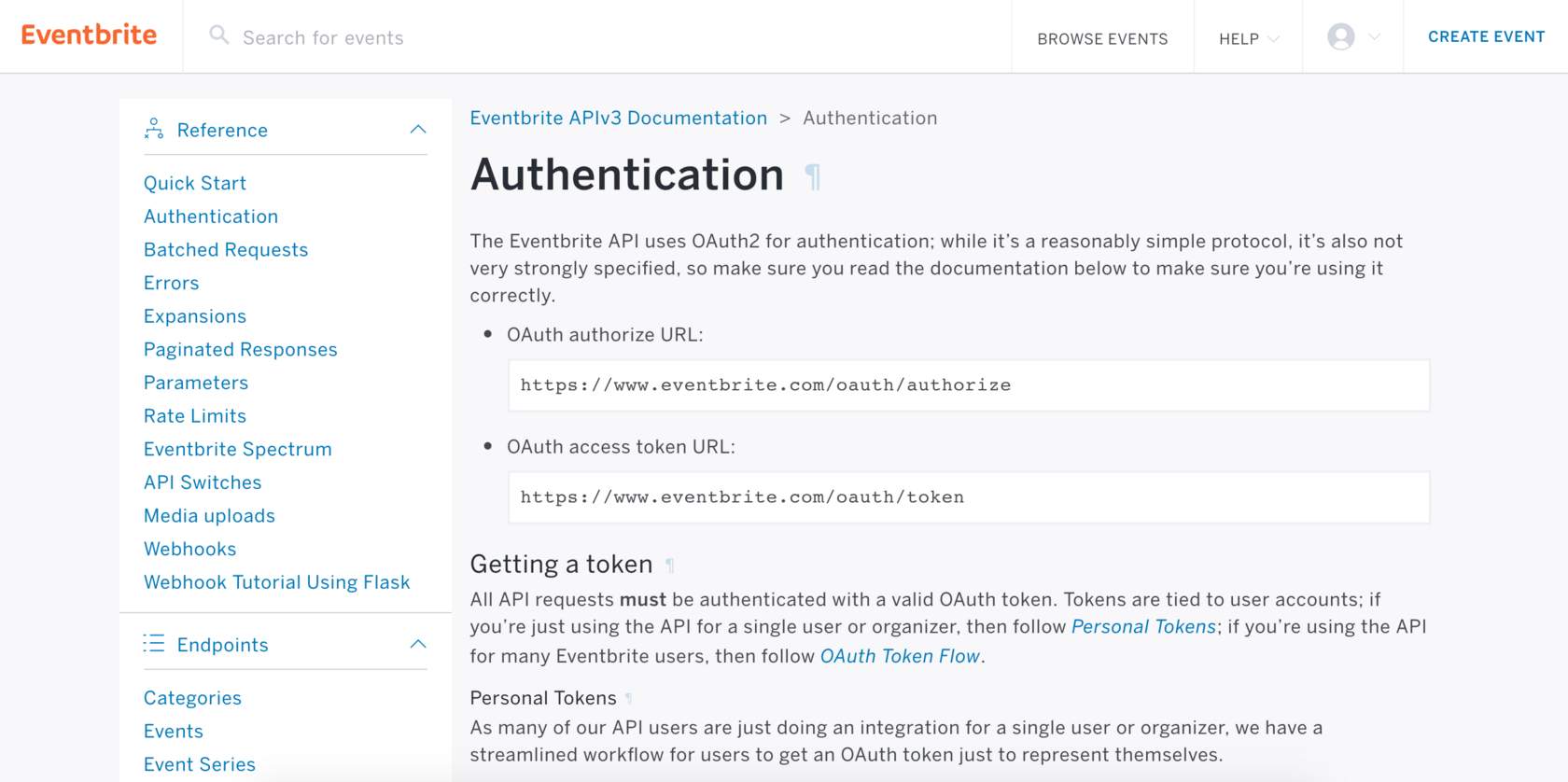 Eventbrite OAuth 2.0 authentication page
Eventbrite OAuth 2.0 authentication page
The following information is required to enable Workato to handle the client key:
Eventbrite authorization URL:
https://www.eventbrite.com/oauth/authorize?response_type=code
Eventbrite access token URL:
https://www.eventbrite.com/oauth/token
You must have a client ID and client secret to connect to your Eventbrite account successfully. You must register an app with Eventbrite to obtain these credentials.
Complete the following steps to obtain your credentials:
Log in to Eventbrite and navigate to Account Settings > App Management.
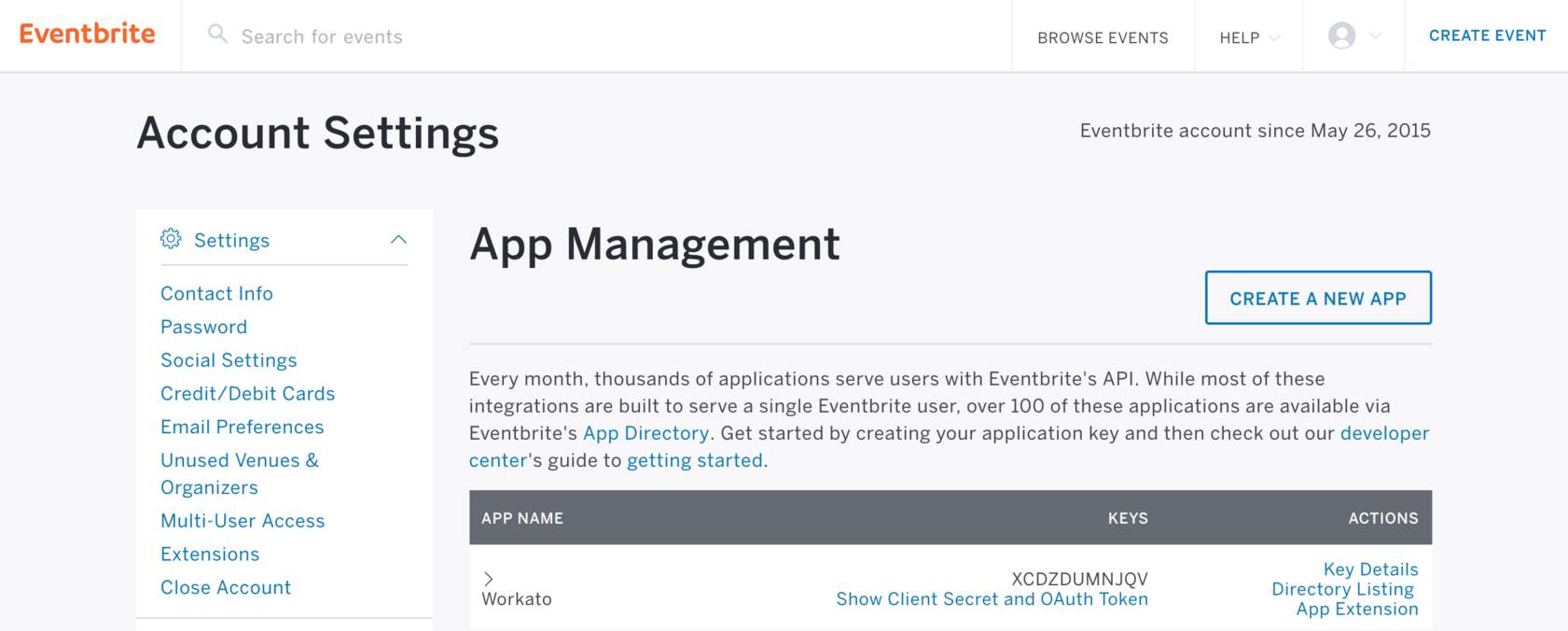 Eventbrite's app management screen
Eventbrite's app management screen
Locate your client ID (also called key) in the App Management page.
Expand the Show Client Secret and OAuth Token section to retrieve the client secret.
Navigate to the App Extension section to input the callback URL: https://www.workato.com/oauth/callback
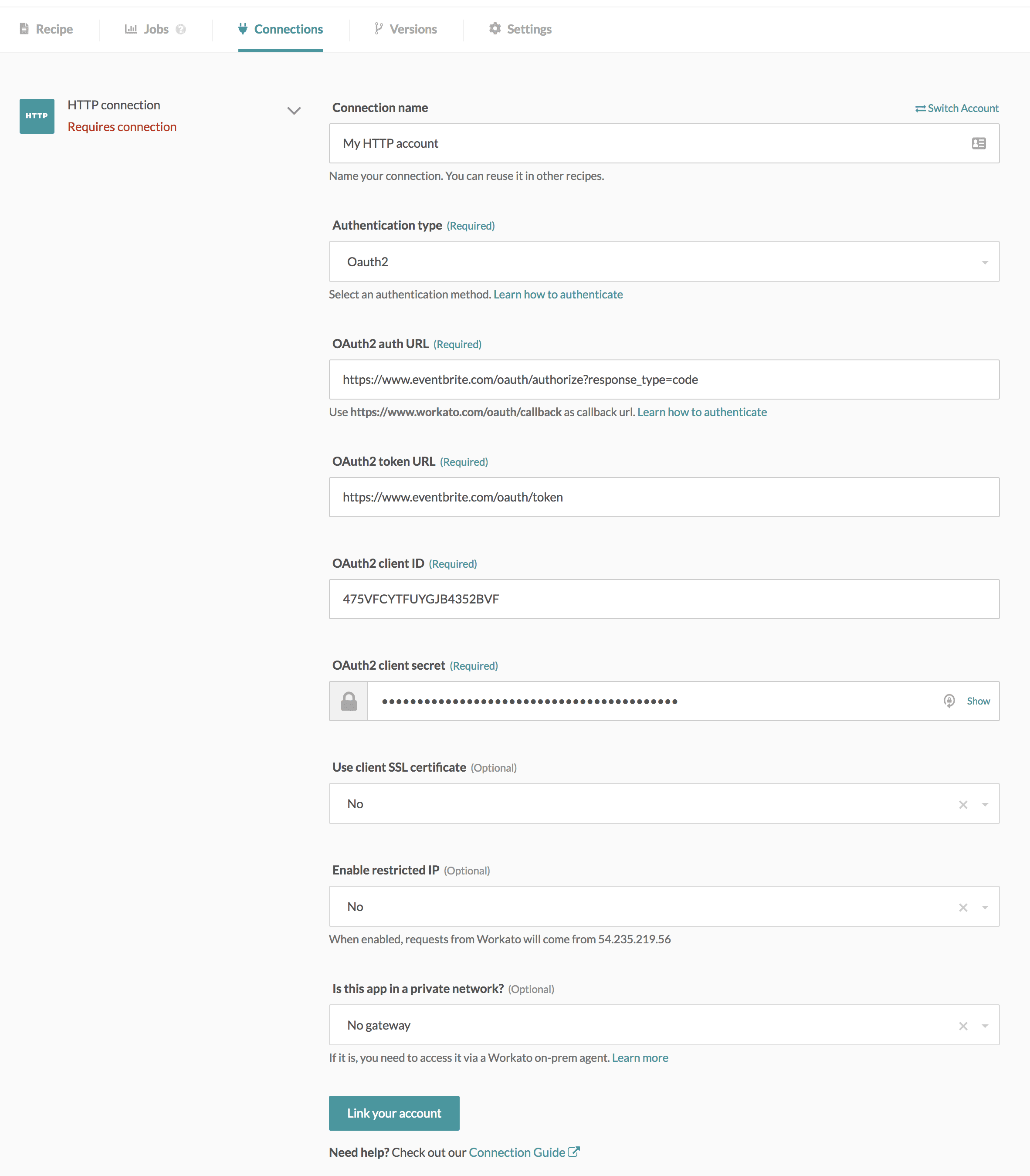 Completed Eventbrite connection
Completed Eventbrite connection
# AWS access key auth authentication type
AWS Access key authentication enables you use access keys you have created as either a root user or an IAM user in AWS. You can assign a maximum of two access keys per user (root user or IAM user). A disabled key can't be used, but it does count toward your limit of two access keys. When you delete an access key, it is permanently removed from the app but can be replaced with a new access key. Refer to the AWS documentation (opens new window) for more information.
AWS IAM AUTHENTICATION RECOMMENDED
We recommend that you use AWS IAM authentication instead of access key authentication.
Complete the following steps to set up your HTTP connection with AWS access key authentication:
Provide a Connection name that identifies your HTTP instance.
 HTTP (AWS Access key auth)
HTTP (AWS Access key auth)
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Connection type drop-down menu to select the connection type you plan to use.
Use the Authentication type drop-down menu to select AWS access key auth.
Provide your AWS service name in the AWS name field.
Provide your account region in the Region field. Region is typically provided in the account URL. For example, if your account URL is https://eu-west-1.console.s3.amazon.com, your region is eu-west-1.
Provide your AWS access key ID in the AWS access key ID field. Go to your AWS account and click My Security Credentials > Users to find the access key ID.
Provide your secret access key in the Secret access key field. Go to your AWS account and click My Security Credentials > Users to find your secret access key.
Use the Endpoint has case-sensitive headers? drop-down menu to set the case sensitivity for your connection.
Provide your base URL in the Base URL field. Recipes can't override this setting.
Click Connect.
# AWS IAM role auth authentication type
AWS IAM role authentication enables you to provide a dedicated role in your AWS instance for Workato to use. By provisioning a dedicated IAM profile, the owner of the AWS instance can grant Workato access to AWS resources without sharing AWS security credentials. It also helps to maintain permission boundaries, including controlled access to specific AWS services and actions that are permitted by a third-party application, such as Workato.
We recommend that you only grant required permissions, and avoid using AllAccess policies whenever possible.
AWS IAM AUTHENTICATION RECOMMENDED
We generally recommend that you use AWS IAM authentication instead of access key authentication.
Complete the following steps to set up your HTTP connection with AWS IAM role authentication:
Provide a Connection name that identifies your HTTP instance.
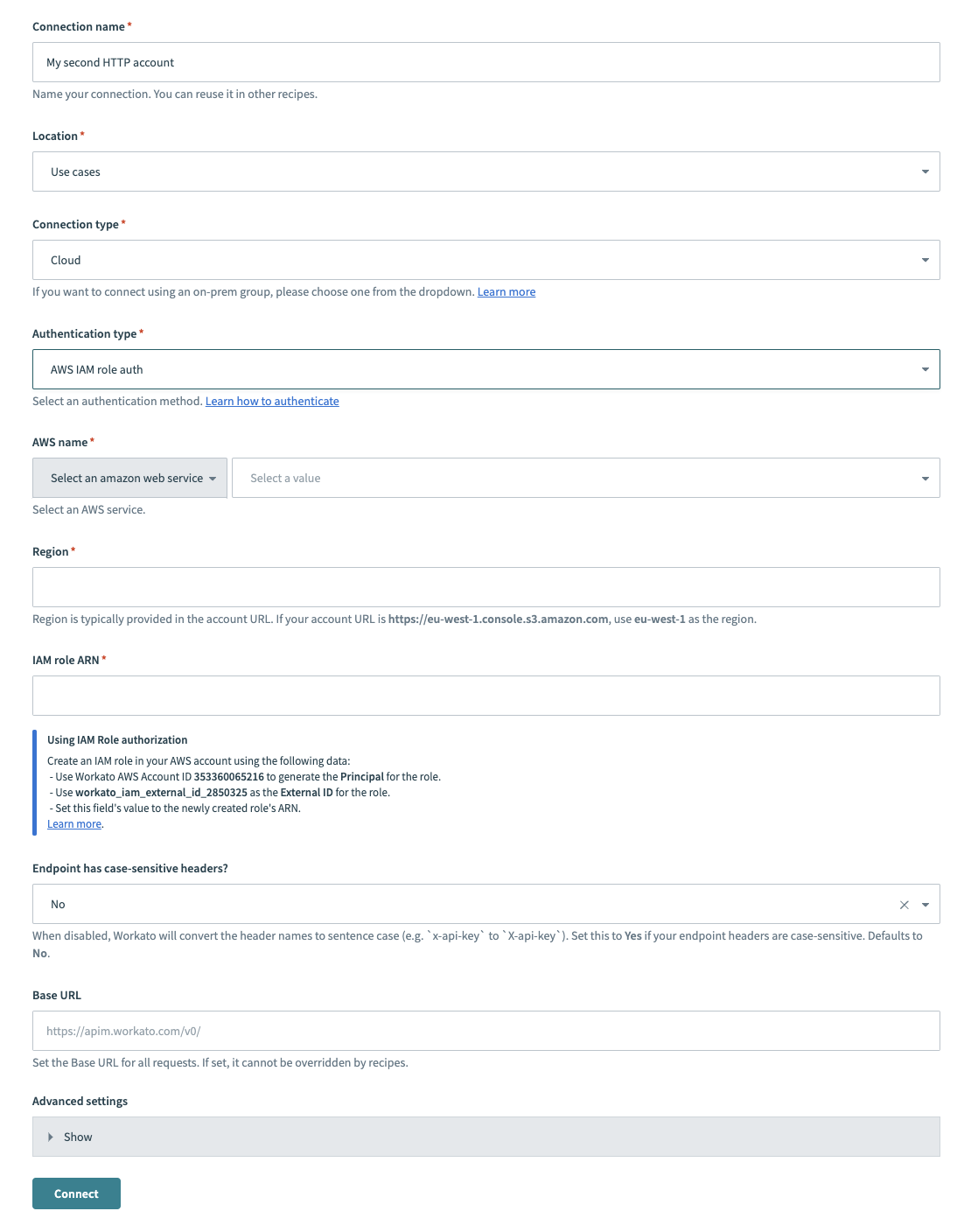 HTTP (AWS IAM role auth) connector's connection fields
HTTP (AWS IAM role auth) connector's connection fields
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Connection type drop-down menu to select the connection type you plan to use.
Use the Authentication type drop-down menu to select AWS IAM role auth.
Provide your AWS service name in the AWS name field.
Provide your account region in the Region field. For example, if your account URL is https://eu-west-1.console.s3.amazon.com, your region is eu-west-1.
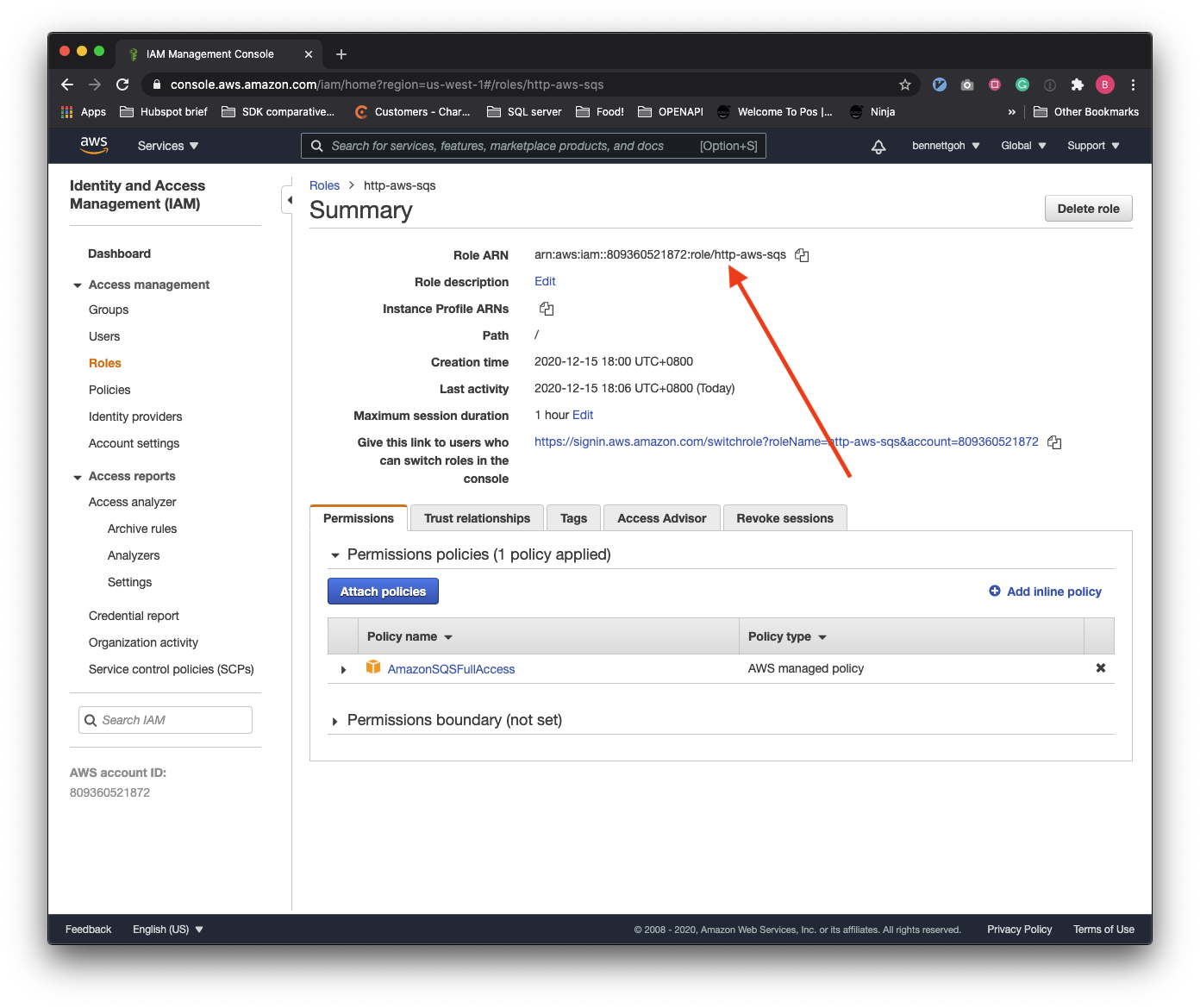
Provide your IAM role ARN in the IAM role ARN field. Refer to the How to retrieve IAM role ARN section for more information.
Use the Endpoint has case-sensitive headers? drop-down menu to set the case sensitivity for your connection.
Provide your base URL in the Base URL field. Recipes can't override this setting.
Click Connect.
# How to retrieve IAM role ARN
Use the following steps to retrieve the Role ARN required for the connection setup. Remember to use the Workato generated external ID found on the connection page.
Go to IAM and select Roles > Create role.
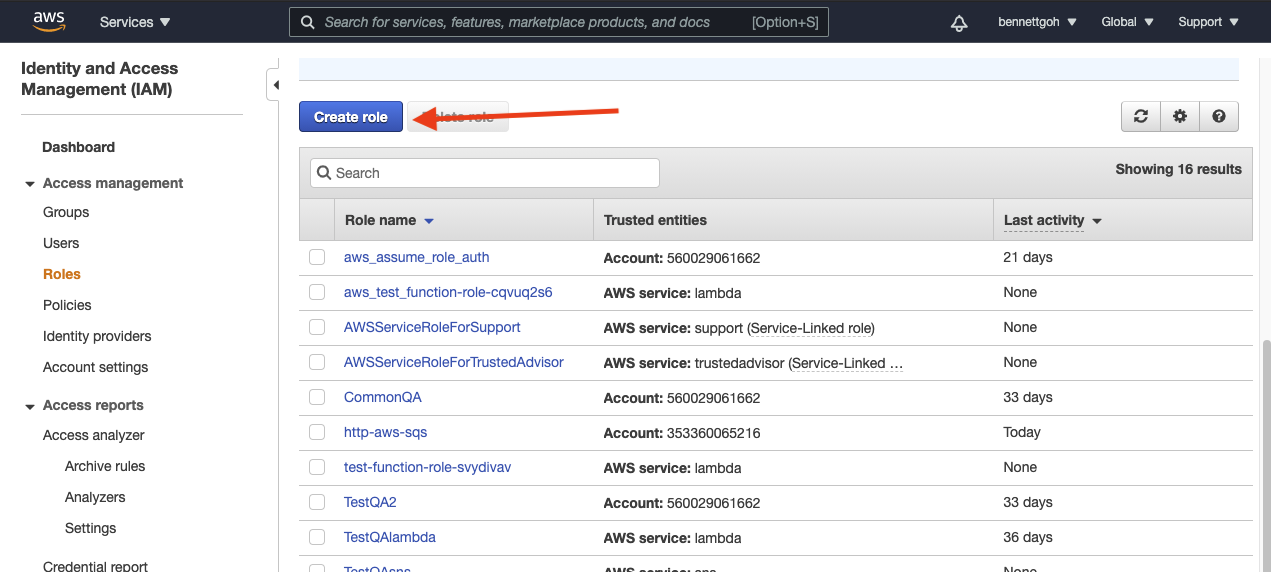
Select Another AWS account and input Workato's Account ID.
Select Require external ID and provide the Workato generated External ID.Every Workato user has a unique External id, for example, workato_iam_external_id_77630. You can find this value in the IAM role ARN section of the connection setup.
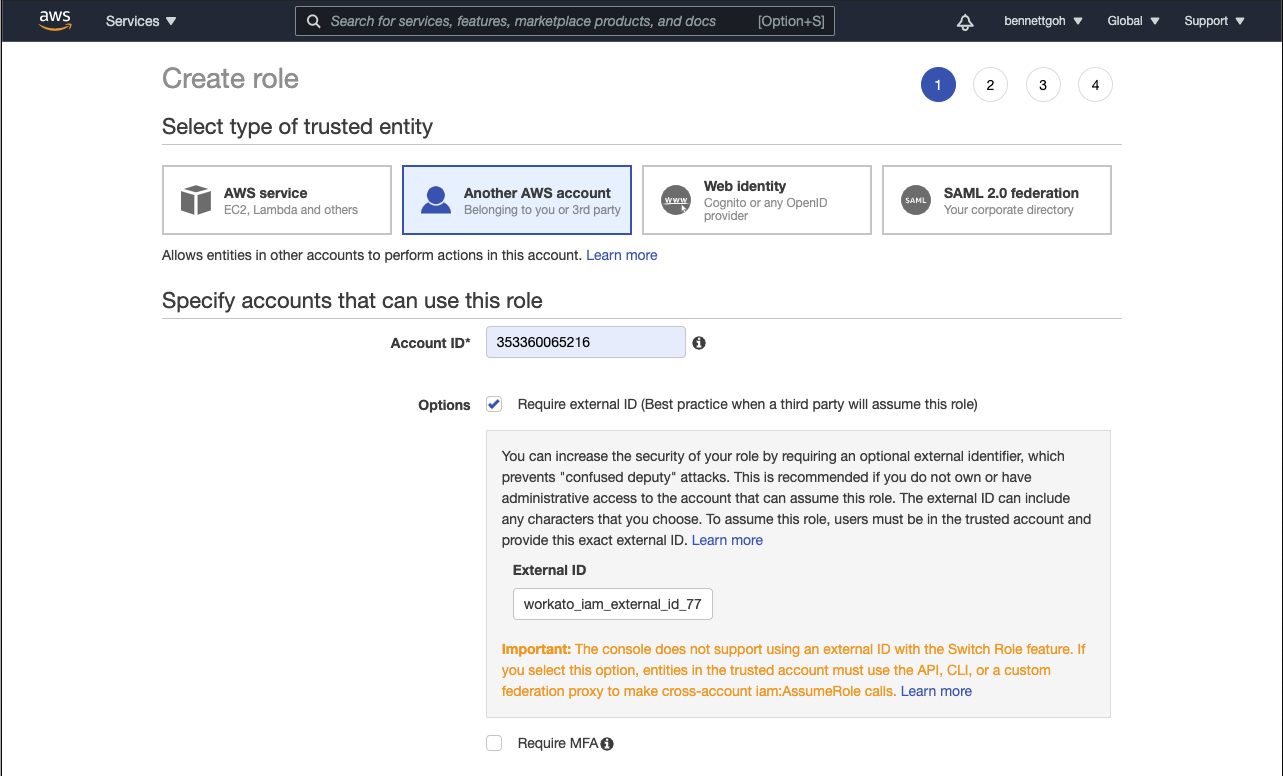
If you require more granular control over how your HTTP connector is used in Workato, you can configure the connection at the project level by changing the scope of the external ID, learn more
Attach permission policies to this role when prompted. This step enables you to provide fine-grained permission controls for Workato. The policies that you attach to this role should be as narrow as possible.
Select an appropriate tag for the IAM role if you are using object tagging.
Provide the IAM Role with an appropriate name and description. Workato recommends that you avoid using a non-guessable resource-id in the URN and that you don't include the external ID.
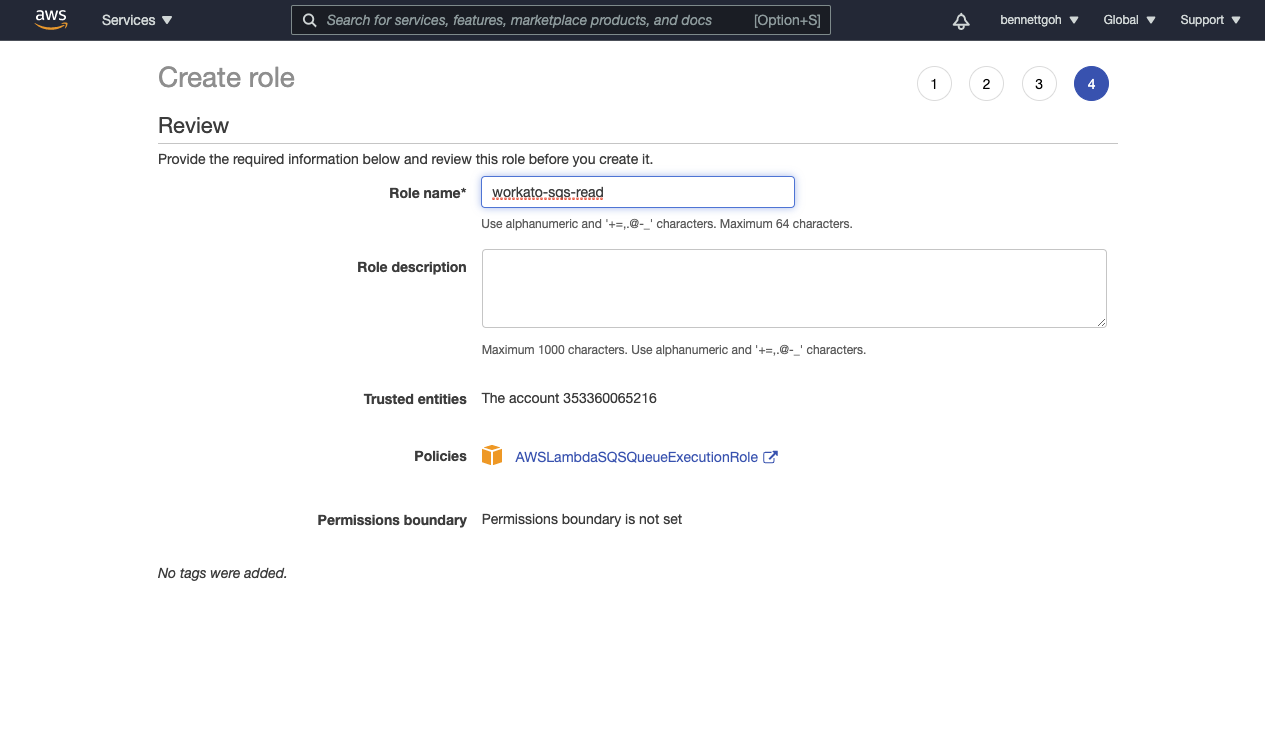
The IAM Role is created.
# Azure OAuth2 authorization code grant authentication type
The Azure OAuth2 authorization code grant authentication type enables you to provide third parties with access to your Azure apps without having to disclose your username and password. Confidential and public clients use this authentication type to exchange an authorization code for an access token.
Complete the following steps to set up your HTTP connection with Azure OAuth2 authorization code grant authentication:
Provide a Connection name that identifies your HTTP instance.
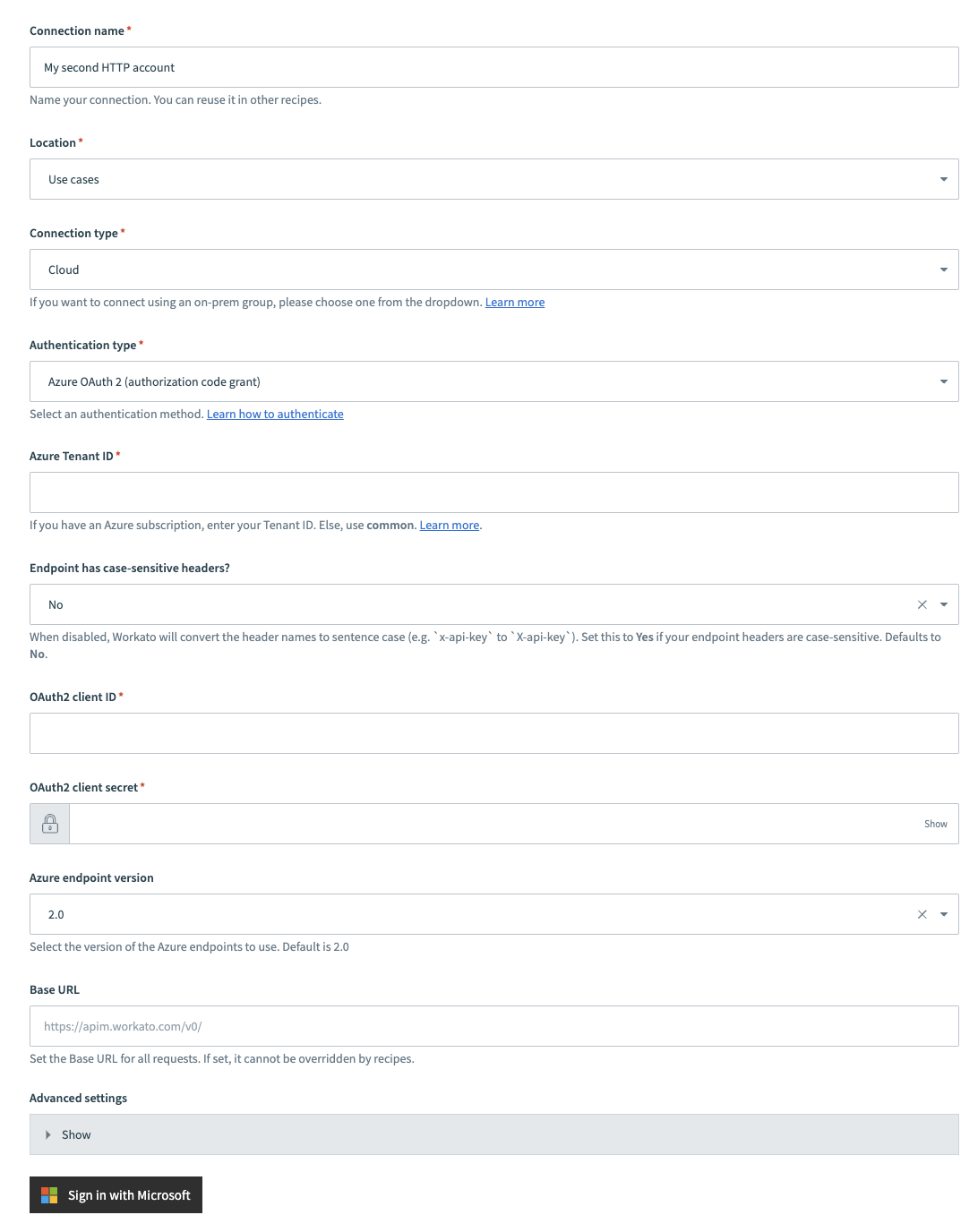 Azure OAuth2 code grant authentication
Azure OAuth2 code grant authentication
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Connection type drop-down menu to select the connection type you plan to use.
Use the Authentication type drop-down menu to select Azure OAuth 2 (authorization code grant).
Provide your tenant ID in the Azure Tenant ID field. If you have an Azure subscription, enter your Tenant ID. Otherwise, use common.
Use the Endpoint has case-sensitive headers? drop-down menu to set the case sensitivity for your connection.
Provide your client ID in the OAuth2 client ID field.
Provide your client secret in the OAuth2 client secret field.
Use the Azure endpoint version to select the version of the Azure endpoints to use. Default is 2.0.
Provide your base URL in the Base URL field. Recipes can't override this setting.
Optional. Expand Advanced settings to configure OAuth2 scopes.
Click Sign in with Microsoft.
# Azure OAuth2 client credentials grant authentication type
You can use the Azure OAuth 2.0 client credentials grant authentication type if you plan to enable the client to request an access token using only client credentials. This authentication type is usually used when the client is requesting access to the protected resources under its control or for machine-to-machine authentication where a specific user’s permission to access data is not required. The client credentials grant type can only be used by confidential clients.
Complete the following steps to set up your HTTP connection with Azure OAuth2 client credentials grant authentication:
Provide a Connection name that identifies your HTTP instance.
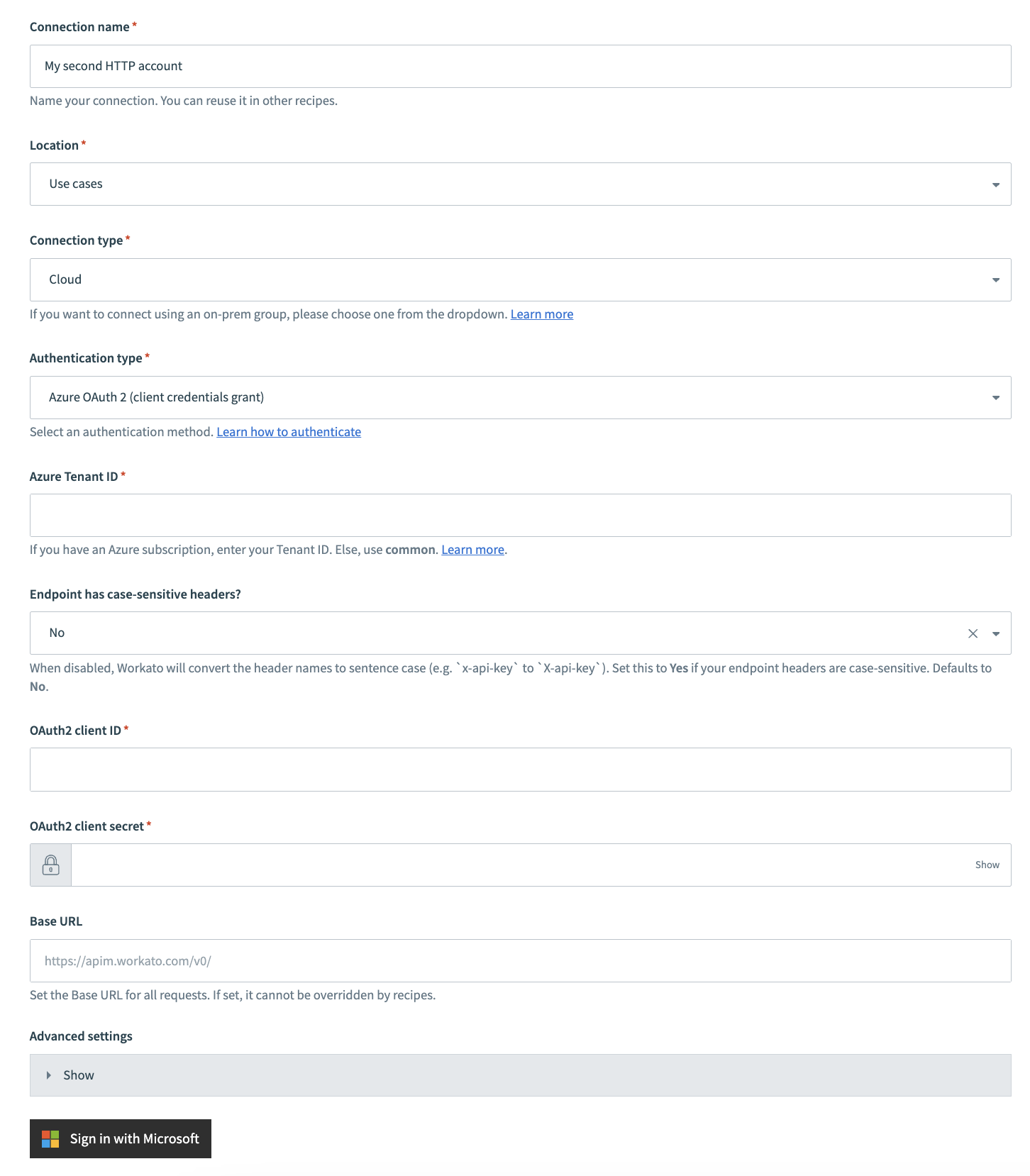 Azure OAuth2 client credentials authentication
Azure OAuth2 client credentials authentication
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Connection type drop-down menu to select the connection type you plan to use.
Use the Authentication type drop-down menu to select Azure OAuth 2 (client credentials grant).
Provide your tenant ID in the Azure Tenant ID field. If you have an Azure subscription, enter your Tenant ID. Otherwise, use common.
Use the Endpoint has case-sensitive headers? drop-down to set the case sensitivity for your connection.
Provide your client ID in the OAuth2 client ID field.
Provide your client secret in the OAuth2 client secret field.
Use the Azure endpoint version to select the version of the Azure endpoints to use. Default is 2.0.
Provide your base URL in the Base URL field. Recipes can't override this setting.
Optional. Expand Advanced settings to configure OAuth2 scopes.
Click Sign in with Microsoft.
# More resources
Last updated: 7/22/2025, 8:29:24 PM