# JWT Workato claim
Identity providers streamline the process of maintaining verified access to multiple applications. The end user only needs to authenticate with the identity provider. Subsequently, the end user can access multiple applications and services without needing to remember additional sets of credentials. For example, the identity provider will issue JSON Web Tokens (JWT) that allow the end user to make authenticated requests with Workato API platform.
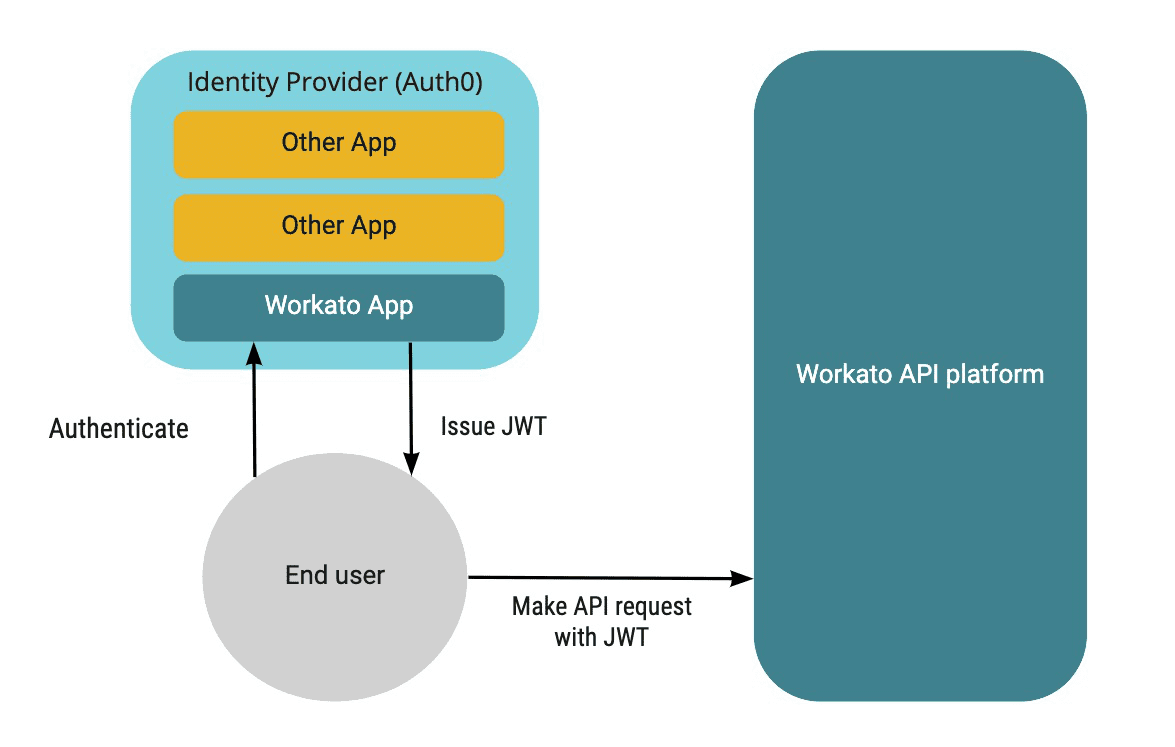 Identity provider issues JWT to the end user, who uses it to obtain verified access to Workato API platform
Identity provider issues JWT to the end user, who uses it to obtain verified access to Workato API platform
When Workato receives an incoming request, the JWT is checked to see if it contains a valid API key. This is done to determine that the request is coming from a valid access profile. If no valid token is found, the API request will return a 401 Unauthorized error.
Workato will inspect the following JWT claims in sequential order. Workato identifies the first claim that is not empty and compares the claim value with an internal list of known access profiles. If the token is not verified, the API request will return a 401 Unauthorized error. Otherwise, if a valid API key is found, the API request will be successful.
# Default claims for access profile key
| Priority | Part | JWT claims | Description |
|---|---|---|---|
| 1st | payload | https://www.workato.com/sub | This is a namespace claim. As it uses unique names, this claim is unlikely to be restricted by the identity providers. |
| 2nd | payload | workato_sub | Workato will inspect this claim if the above claims are empty. |
| 3rd | payload | sub | This represents the subject of the JWT. Some identity providers reserve this JWT claim and thus Workato API key cannot be used here. Workato will inspect this claim if the above claims are empty. |
| 4th | header | kid | This is a header claim. Workato will inspect this claim if the above claims are empty. |
If these claims are used for other purposes in your use case, you may use a custom claim to hold the access profile key.
# Advanced settings
# Reserved claims to enforce
This multiselect input allows you to choose which of the reserved claims you want to enforce. API platform will ensure that every chosen claims here are present in the JWT. For example, select exp to ensure that only tokens with limited validity are used to access your APIs.
# Allowed issuers for iss claim
If iss is select in Reserved claims to enforce, this additional input will be provided. Here, you can provide a list of iss values that will be allowed. Leave this field blank to accept all iss values.
# Custom claim for access profile key
If all four of the default access profile claims are occupied for other purposes, you may use a custom claim to hold the access profile key in the JWT. This custom claim must be specified in the access profile configuration.
Last updated: 5/21/2025, 5:22:32 AM