# Okta
Okta (opens new window) is a cloud service that organizes workforce and customer identities.
It provides cloud software that helps companies to manage secure user authentication for modern applications and helps developers to build identity controls into applications, web services, and devices.
# API version
The Okta connector uses the Core Okta API v1 (opens new window).
# How to connect to Okta
Workato supports the following connection types for Okta:
- Authorization code grant authentication (OAuth 2.0)
- Client credentials-based authentication (OAuth 2.0)
- API key-based authentication
Workato recommends using either Authorization code grant authentication (OAuth 2.0) or Client credentials-based authentication (OAuth 2.0) for improved security in your connection. These methods also let you define granular permissions that control which resources Workato can access in Okta.
VIRTUAL PRIVATE WORKATO (VPW) CUSTOMERS
This feature requires configuration steps that are specific to your Virtual Private Workato (VPW) instance. If you are a VPW customer, refer to your VPW private documentation for the configuration details for your instances.
# Authorization code grant authentication
Complete the following steps to set up your connection using authorization code grant authentication:
Log in to your Workato account and go to the project where you plan to add your Okta connection.
Click Create > Connection and select Okta as your connection.
Select the Authorization code grant option from the Authentication type drop-down menu and enter the following information:
| Connection field | Description |
|---|---|
| Connection name | Give this connection a unique name that identifies which Okta instance it is connected to. |
| Okta domain | Enter your Okta domain name (for example, mycompany.okta.com or mytest.oktapreview.com). |
| Client ID | Provide the client ID generated in Okta by completing the following steps. |
| Client secret | Provide the client secret generated in Okta by completing the following steps. |
| Advanced settings | Select the necessary OAuth 2.0 scopes to request from Okta in this connection. These must match the scopes defined in the Okta API Scopes section of your Okta app integration. |
# Generate a client ID and secret for authorization code grant authentication
Complete the following steps to generate a client ID and secret for authorization code grant authentication:
Sign in to your Okta organization as a user with administrator privileges.
Go to the Okta Admin Console and select Applications > Applications.
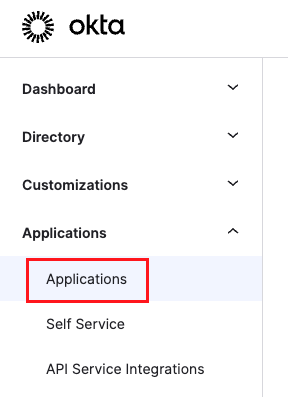 Navigate to Applications > Applications
Navigate to Applications > Applications
Select Create App Integration.
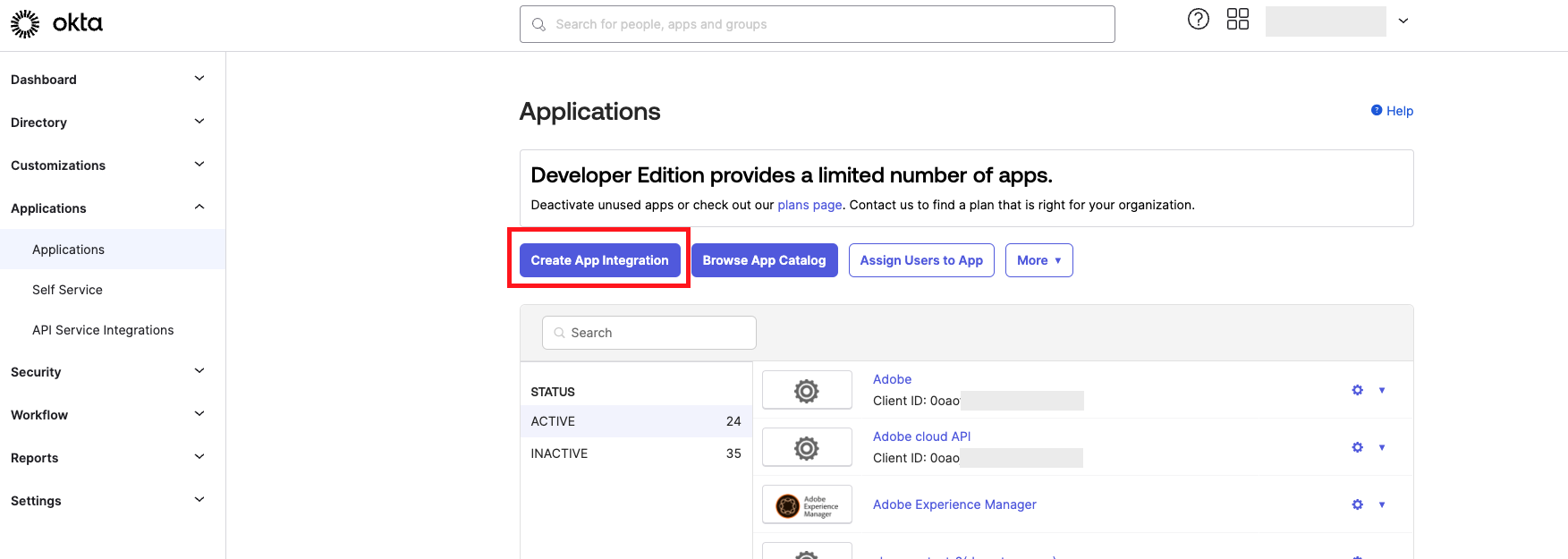 Select Create App Integration
Select Create App Integration
Go to the Create a new app integration page, locate the Sign-in method section, and select OIDC - OpenID Connect.
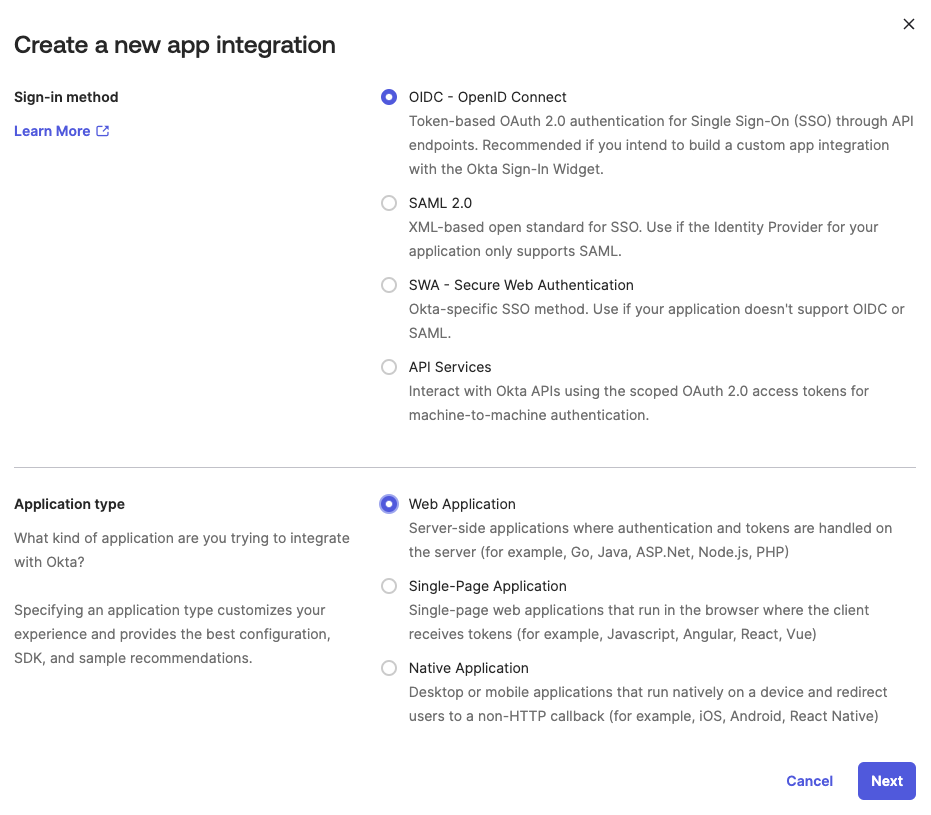 Create a new app integration
Create a new app integration
Select Web Application in the Application type section.
Enter a unique App integration name on the New Web App Integration page.
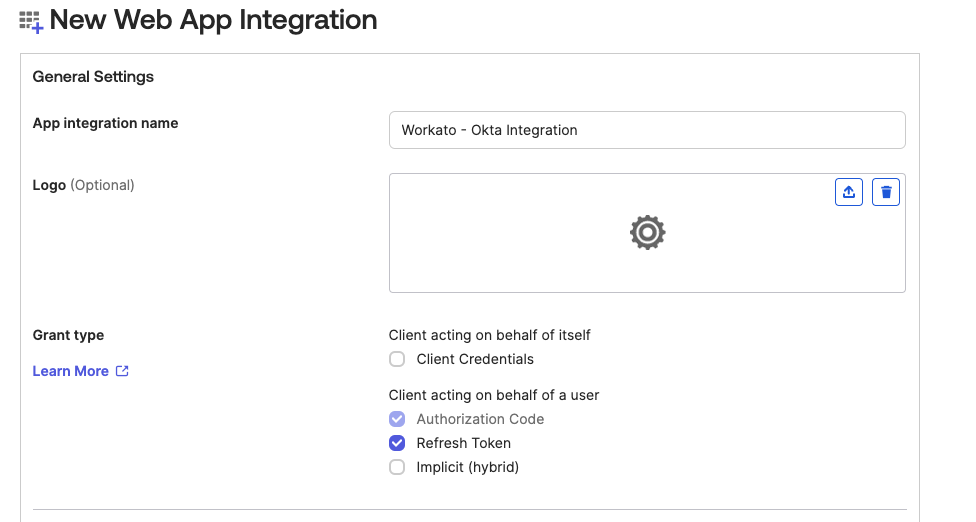 New Web App Integration page
New Web App Integration page
Ensure the Proof of possession field is deselected.
Select the following checkboxes in the Client acting on behalf of a user field of the Grant type section:
- Authorization Code
- Refresh Token
Enter the Workato callback URI in the Sign-in redirect URIs section according to your data center:
- US Data Center:
https://www.workato.com/oauth/callback - EU Data Center:
https://app.eu.workato.com/oauth/callback - JP Data Center:
https://app.jp.workato.com/oauth/callback - SG Data Center:
https://app.sg.workato.com/oauth/callback - AU Data Center:
https://app.au.workato.com/oauth/callback - IL Data Center:
https://app.il.workato.com/oauth/callback - Developer sandbox:
https://app.trial.workato.com/oauth/callback
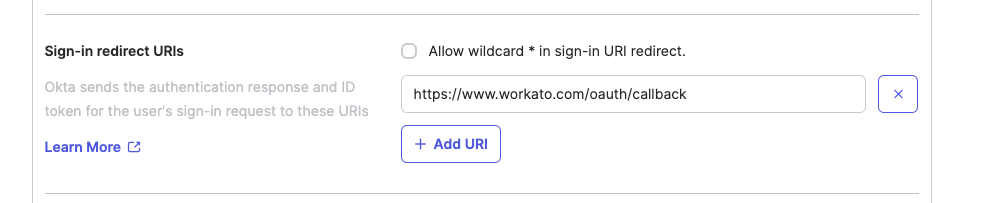 Sign-in redirect URIs
Sign-in redirect URIs
Select an Assignment option according to your preference and then select Save. Okta creates the app integration.
Copy the Client ID and Client Secret in the new app integration's General tab so you can enter these credentials in Workato's Okta connection settings.
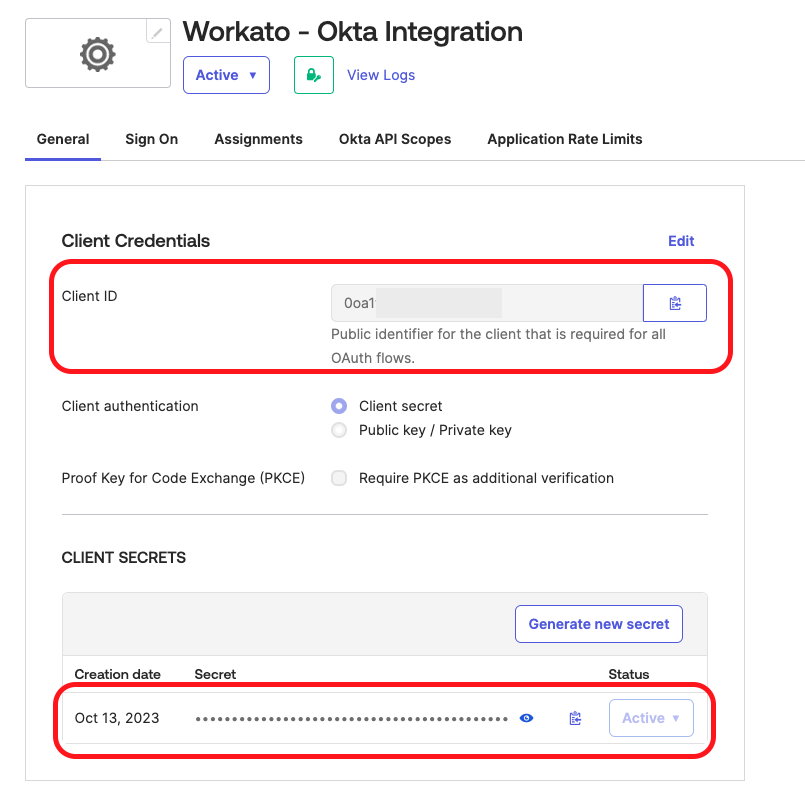 Copy the Client ID and Client Secret
Copy the Client ID and Client Secret
Go to General Settings and ensure the Proof of possession field is deselected.
Go to the Okta API Scopes tab and assign the necessary scopes to the integration. The connection requires the following scopes at a minimum:
okta.logs.readokta.schemas.read
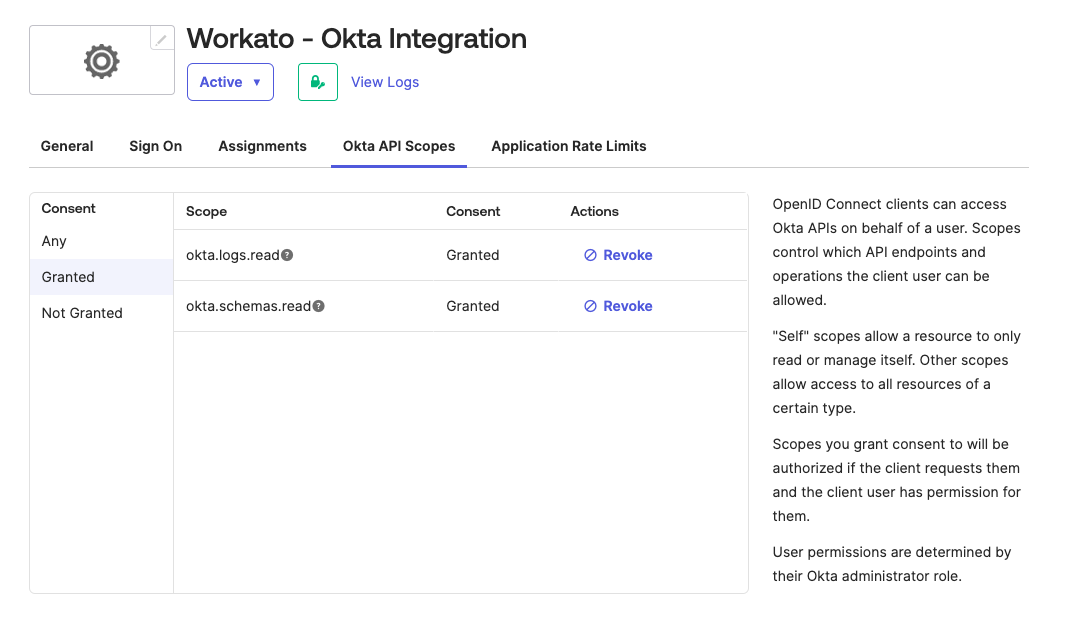 Assign Okta API scopes
Assign Okta API scopes
# Client credentials-based authentication
Complete the following steps to set up your connection using client credentials authentication:
Log in to your Workato account and go to the project where you plan to add your Okta connection.
Click Create > Connection > select Okta as your connection.
Select the Client credentials option from the Authentication type drop-down menu and enter the following information:
| Connection field | Description |
|---|---|
| Connection name | Give this connection a unique name that identifies which Okta instance it is connected to. |
| Okta domain | Enter your Okta domain name (for example, mycompany.okta.com or mytest.oktapreview.com). |
| Client ID | Provide the client ID generated in Okta by completing the following steps. |
| Private Key | Provide the private key generated in PEM format in Okta by completing the following steps. |
| Advanced settings | Select the necessary OAuth 2.0 scopes to request from Okta in this connection. These must match the scopes defined in the Okta API Scopes section of your Okta app integration. |
# Generating a client ID and secret for client credentials-based authentication
Complete the following steps to generate a client ID and secret for client credentials-based authentication:
Sign in to your Okta organization as a user with administrator privileges.
Go to the Okta Admin Console and select Applications > Applications.
 Select Applications > Applications
Select Applications > Applications
Select Create App Integration.
 Select Create App Integration
Select Create App Integration
Select API Services in the Sign-in method section of the Create a new app integration page.
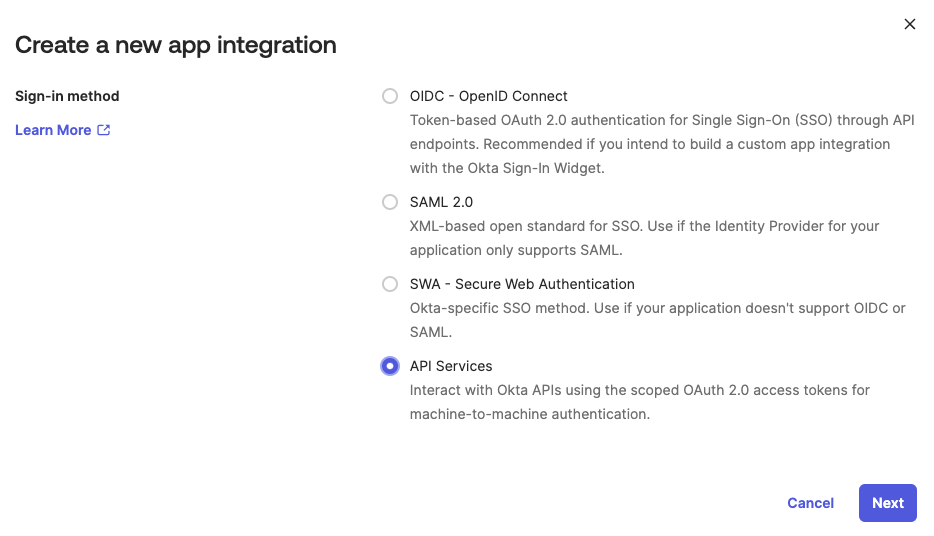 Select API Services
Select API Services
Enter a unique App integration name on the New API Services App Integration page and then select Save.
 App integration name
App integration name
Copy the Client ID in the new app integration's General tab.
 Copy Client ID
Copy Client ID
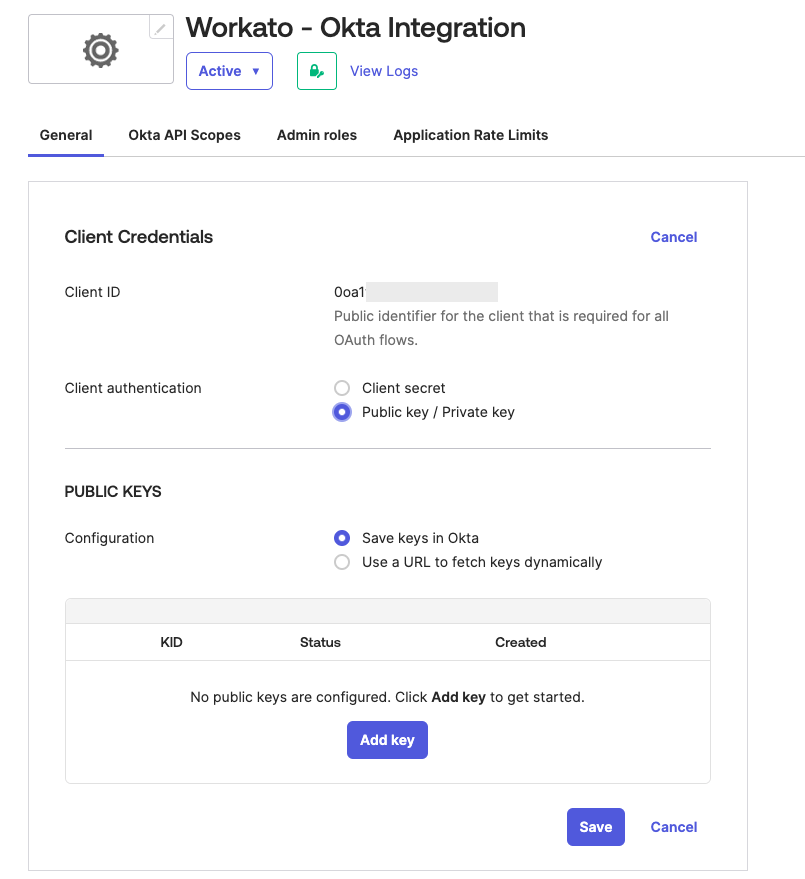
Select Edit and then select Public key / Private key in the Client authentication field.
Select Add key in the PUBLIC KEYS section.
Select Generate new key in the Add a public key section to generate a new key pair.
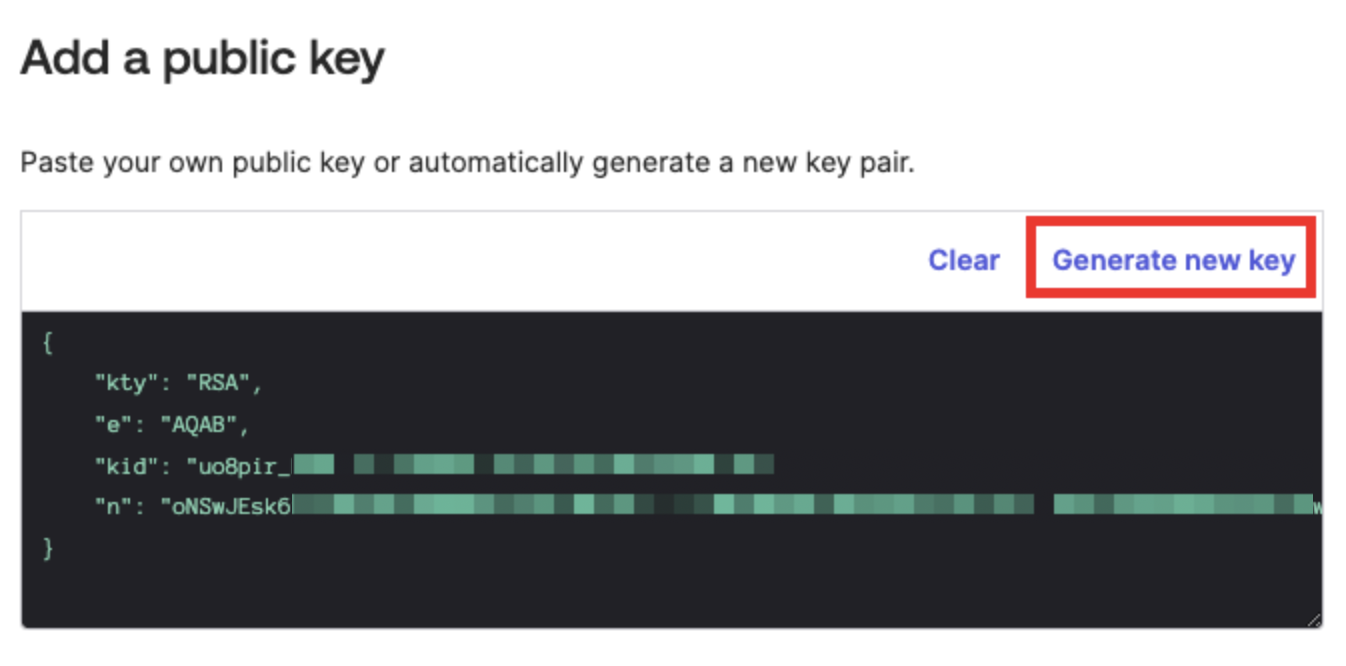 Add a public key
Add a public key
Select PEM in the Private key section, then copy the private key. Enter this key in Workato's Okta connection settings. You can't retrieve the private key again after leaving the page.
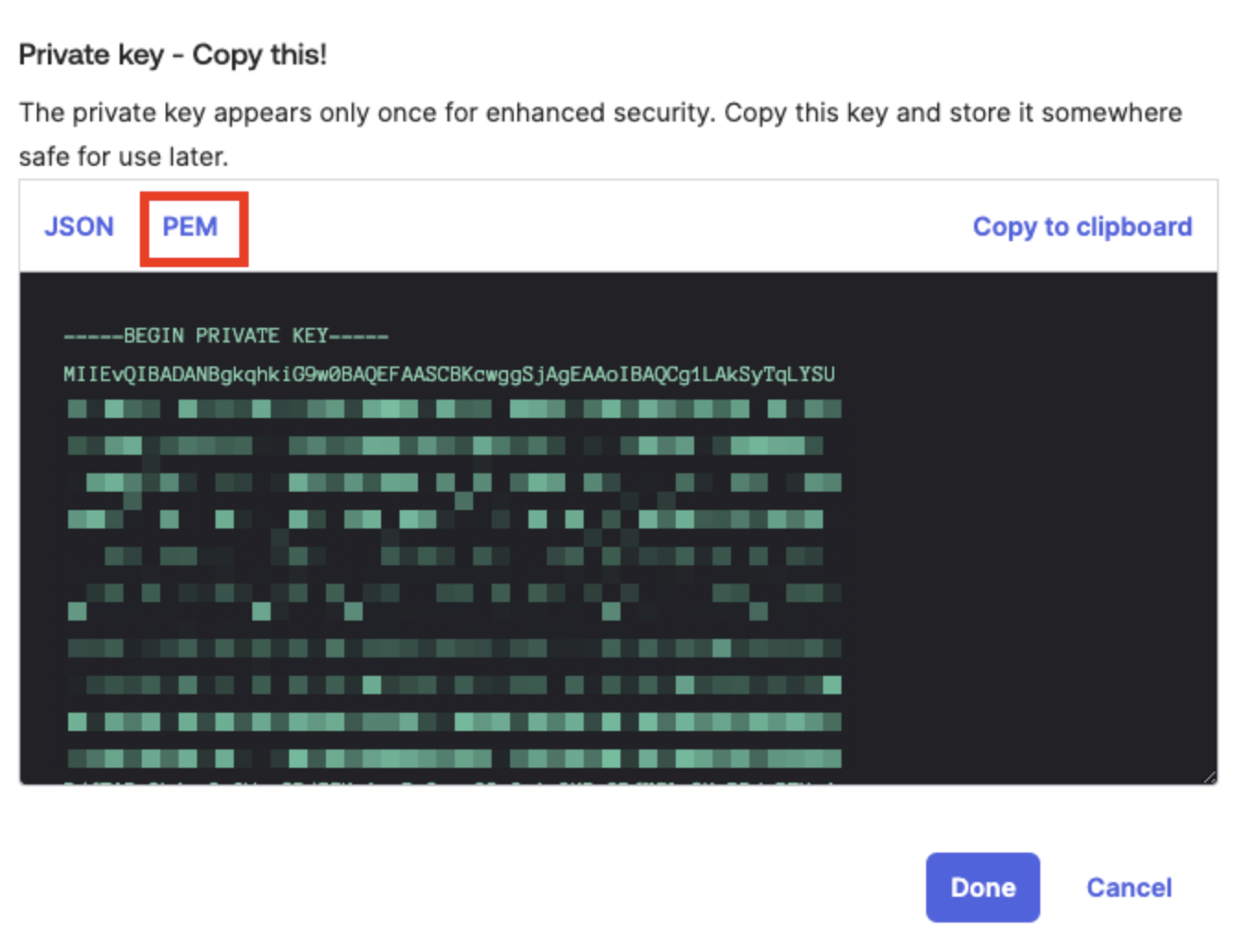 Copy the private key
Copy the private key
Select Done.
Select Save in the new app integration's General tab to store and activate the key. You must save the key before you can use it to connect to Workato.
Click Save if you see the message Existing client secrets will no longer be used.
The key status changes to Active.
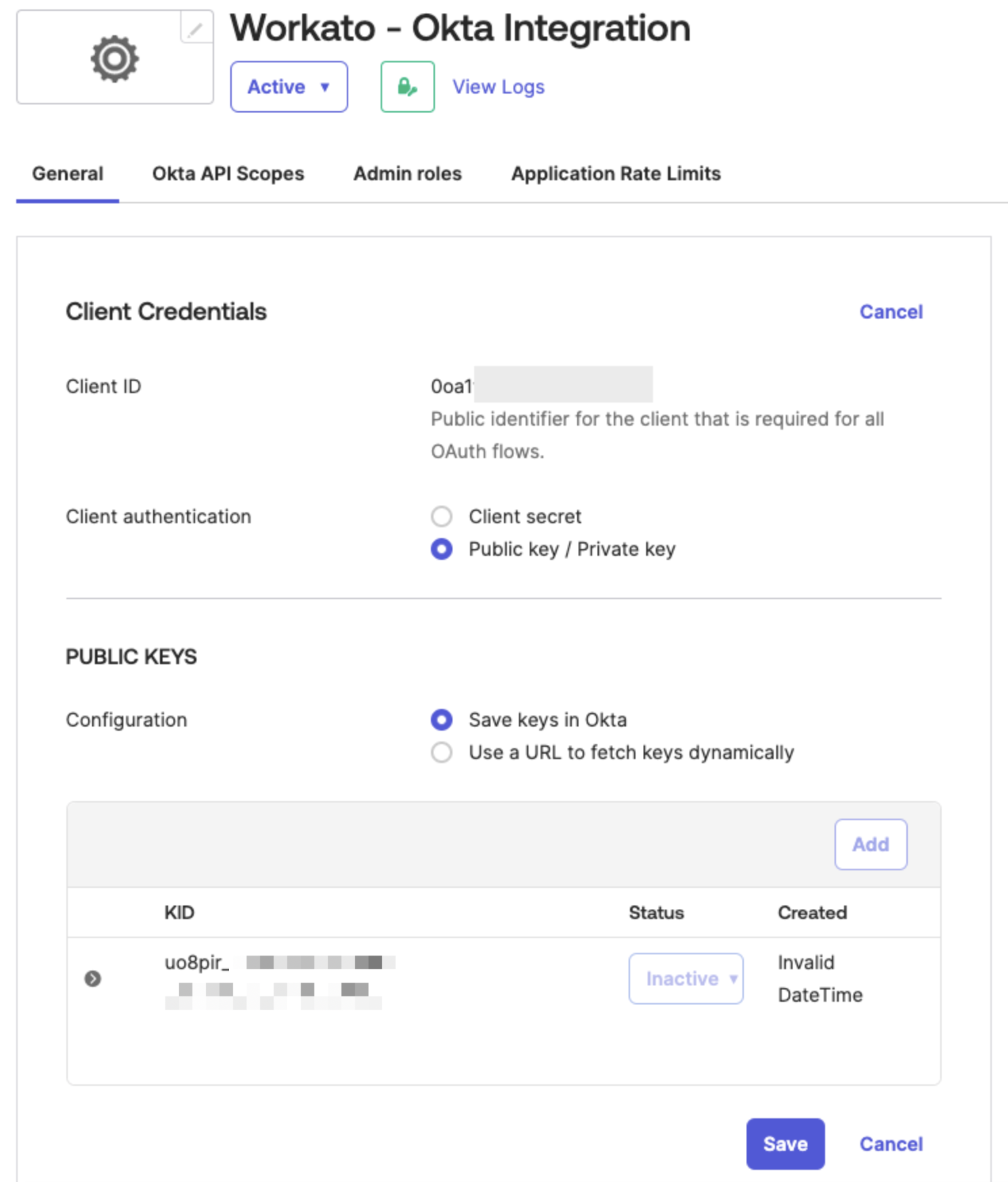 Activate the key
Activate the key
Go to the Okta API Scopes tab and assign the necessary scopes to the integration. The connection requires the following scopes at a minimum:
okta.logs.readokta.schemas.read
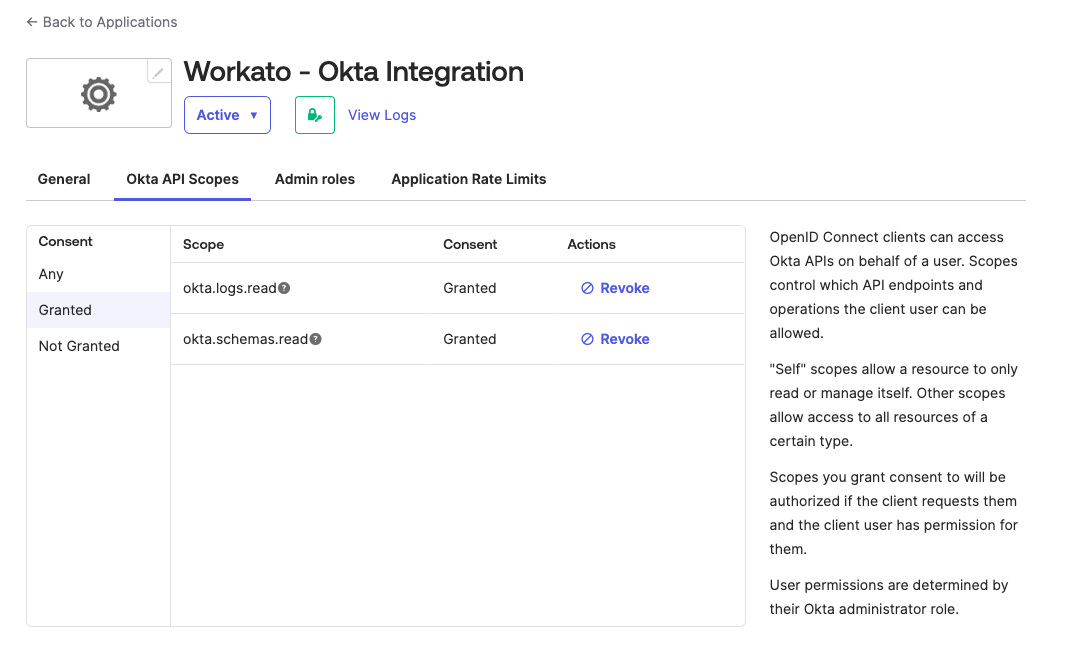 Assign Okta API scopes
Assign Okta API scopes
# API key-based authentication
The Okta connector uses an API key to authenticate with Okta.
API keys inherit the permissions of the administrator who created them and aren't scoped. We recommend that you use a scoped OAuth 2.0 access token for improved security.
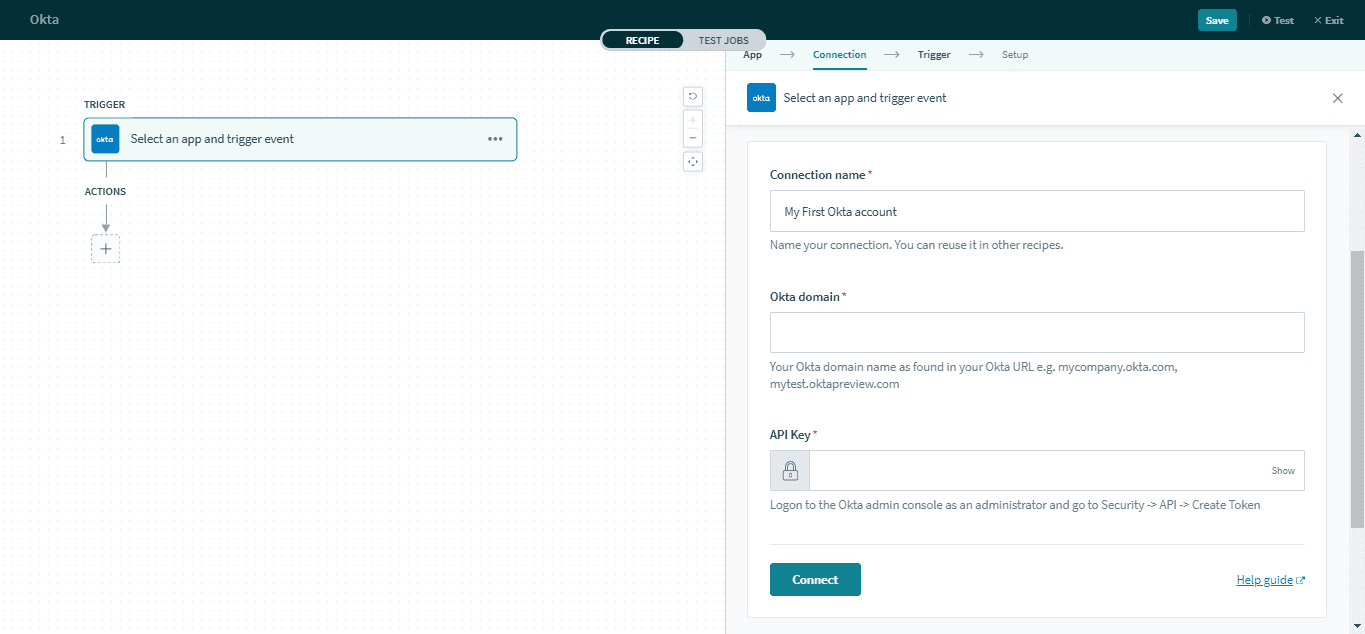 Okta connection setup
Okta connection setup
| Connection field | Description |
|---|---|
| Connection name | Give this connection a unique name that identifies which Okta instance it is connected to. |
| Okta domain | Enter your Okta domain name (for example, mycompany.okta.com or mytest.oktapreview.com). |
| API Key | Enter the API key generated from your Okta instance. Go to Security > API > Create token to generate a key. The key inherits the permissions of the administrator who created it. |
Creating API tokens requires administrator privileges. Ensure that you're logged in as an administrator before you proceed. Refer to Okta's documentation (opens new window) for more information.
# Roles and permissions required to connect
Workato requires that the user and API key used to connect to Workato have Organization Administrator or Super Administrator permissions.
# Troubleshooting connection issues with OAuth 2.0 connections
# Issue: 400 Bad Request error
If you encounter a 400 Bad Request error when setting up an OAuth 2.0 connection to Okta, it may be due to the newly introduced Demonstrating Proof-of-Possession (DPoP) for OAuth 2.0, which is now enabled by default for new applications. To ensure successful connection, disable DPoP for your Okta applications.
Log in to your Okta Admin Console.
Navigate to Applications and select your application.
Go to the General > General Settings > APPLICATION.
Ensure the Proof of possession field is deselected.
For more details, refer to the following resources:
- Okta Release Notes on DPoP (opens new window)
- Configure OAuth 2.0 Demonstrating Proof-of-Possession (opens new window)
# Triggers and actions
The following documentation contains triggers supported on Workato:
The following documentation contains user lifecycle actions supported on Workato:
- Create user
- Activate user
- Update user
- Add user to group
- Remove user from group
- Deactivate user
- Delete user
The following documentation contains resource discovery actions supported on Workato:
Last updated: 3/5/2026, 12:08:37 AM