# Set up CyberArk Conjur for project-level secrets management
Existing external secrets references that are scoped to the workspace level will stop working when you switch to project-specific secrets management.
FEATURE AVAILABILITY
Secrets management is available to customers on specific pricing plans. Refer to your pricing plan and contract to learn more.
# Conjur host configuration for Workato
Integration between Workato and Conjur is based on the host/workload API key authentication.
For Workato to retrieve a secret from your Conjur instance, an API authentication request is first sent to your Conjur server based on the parameters specified when configuring the CyberArk Conjur connector. If the credentials are valid, Conjur responds with a short-lived access token. Workato then uses this access token to retrieve the actual secret value stored in Conjur if the host has the necessary execute and read permissions.
Policies on Conjur are written as .yml files. Visit the CyberArk Conjur documentation for policy best practices (opens new window). The following steps describe how to develop a policy file.
For more information on policy syntax operators, refer to the CyberArk Conjur documentation (opens new window).
Declare a group at the root policy:
- !policy
id: workato-app
body:
- !group workato-secret-users
Declare variables and assign the group [read, execute] permissions.
This example creates the sql-password-prod and sql-host-prod variables which store the password for a SQL database as well as the host name:
- &variables
- !variable
id: sql-password-prod
kind: password
- !variable
id: sql-host-prod
kind: password
- !permit
role: !group /workato-app/workato-secret-users # group declared earlier
privileges: [read, execute]
resources: *variables
Declare the host, a layer, and assign membership of the host into the layer:
- !host workato-us-prod-1
- !layer workato-us-prod
- !grant
role: !layer workato-us-prod
members:
- !host workato-us-prod-1
Grant membership of the layer into the group:
- !grant
role: !group workato-app/workato-secret-users
member: !layer workato-app/ workato-us-prod
Create a new secret on Conjur:
- !variable
id: ddog-api-key
kind: password
Grant execute and read permissions to group on selected variables:
- !permit
role: !group /workato-app/workato-secret-users # layer declared earlier
privileges: [read, execute]
resources: !variable ddog-api-key
Expand for an example of a full policy
- !policy
id: workato-app-dev
body:
- !group workato-secrets-dev
- &variables
- !variable
id: sql-password-prod
kind: password
- !variable
id: sql-host-prod
kind: password
- !permit
role: !group /workato-app-dev/workato-secrets-dev # group declared earlier
privileges: [read, execute]
resources: *variables
- !host workato-us-dev-1
- !layer workato-us-dev
- !grant
role: !layer workato-us-dev
members:
- !host workato-us-dev-1
- !grant
role: !group workato-secrets-dev
member: !layer workato-us-dev
To which the expected response would be:
{
"created_roles": {
"workato:host:workato-app-dev/workato-us-dev-1": {
"id": "workato:host:workato-app-dev/workato-us-dev-1",
"api_key": "1q3ye3gxxxx"
}
},
"version": 1
}
# Select project-level scope for secrets management
Sign in to your Workato workspace.
Navigate to Workspace admin > Settings > Security > External secrets manager.
In Scope, select the option Set up secrets management for each project individually.
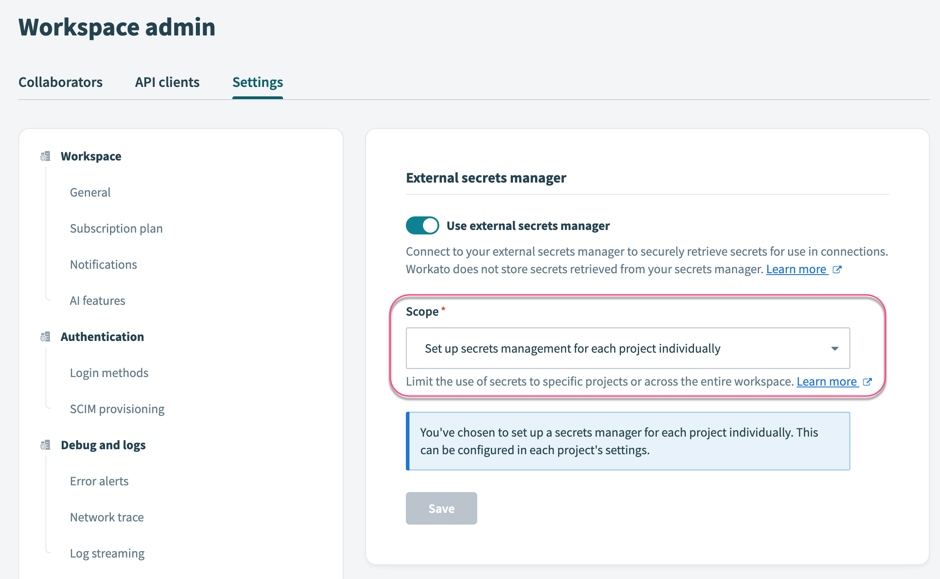 Set up secrets management for each project individually
Set up secrets management for each project individually
Select Save.
# Select the project
In Workato, navigate to your projects.
Select the project that you plan to configure with secrets management.
In the project, navigate to Workspace admin > Settings > External secrets manager.
In the Which secrets manager do you want to use? field, select CyberArk Conjur.
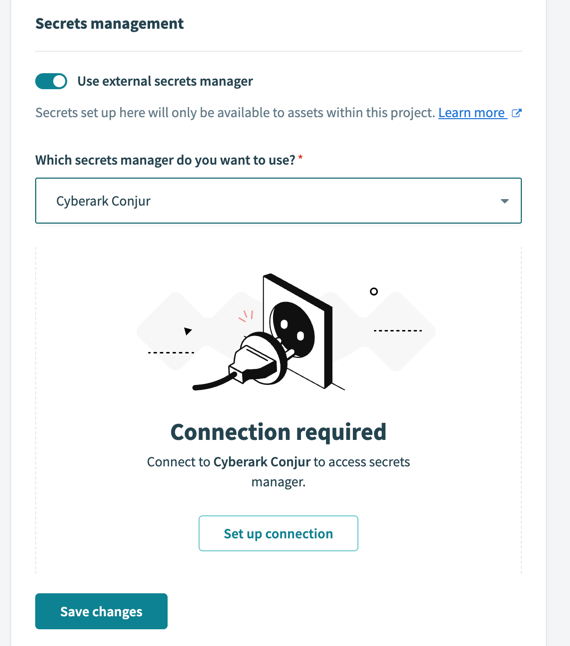
Click Set up connection
# Configure the connection in Workato
Configure the following fields in Workato:
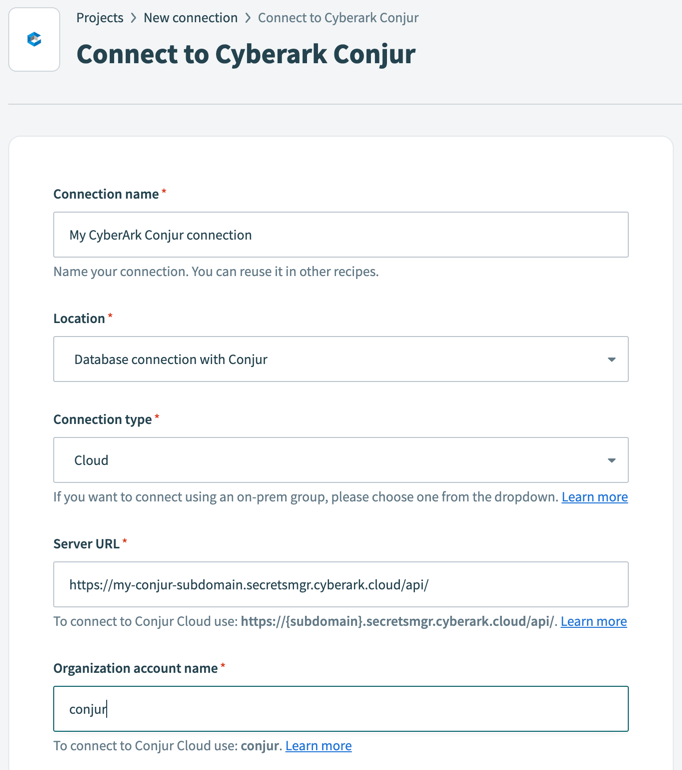 Configure CyberArk Conjur connection
Configure CyberArk Conjur connection
Connection name
Name your CyberArk Conjur connection.
Connection type
Workato supports both cloud and on-prem connection types. If you plan to use an on-prem group, select one from the drop-down.
Server URL
To connect to Conjur Cloud, the server URL must follow this format:
https://<subdomain>.secretsmgr.cyberark.cloud/api/Organization account name
To connect to Conjur Cloud, input
conjur.Login ID
For host authentication, the ID must be prefixed with
host/, for example:host/workato-app/workato-user-1.API key
Conjur generates an API key for every user when the user resource is created. Learn more about generating an API key in CyberArk Conjur's documentation (opens new window).
Last updated: 10/14/2025, 4:38:57 PM