# OpenID Connect
Identity providers streamline the process of maintaining verified access to multiple applications. The end user only needs to authenticate with the identity provider (IdP). Subsequently, the end user can access multiple applications and services without needing to remember additional sets of credentials. For example, the identity provider will issue JSON Web Tokens (JWT) that allow the end user to make authenticated requests with Workato API platform.
API platform integrates fully with your IdP using the OpenID Connect (opens new window) specification to manage cross-domain authentication.
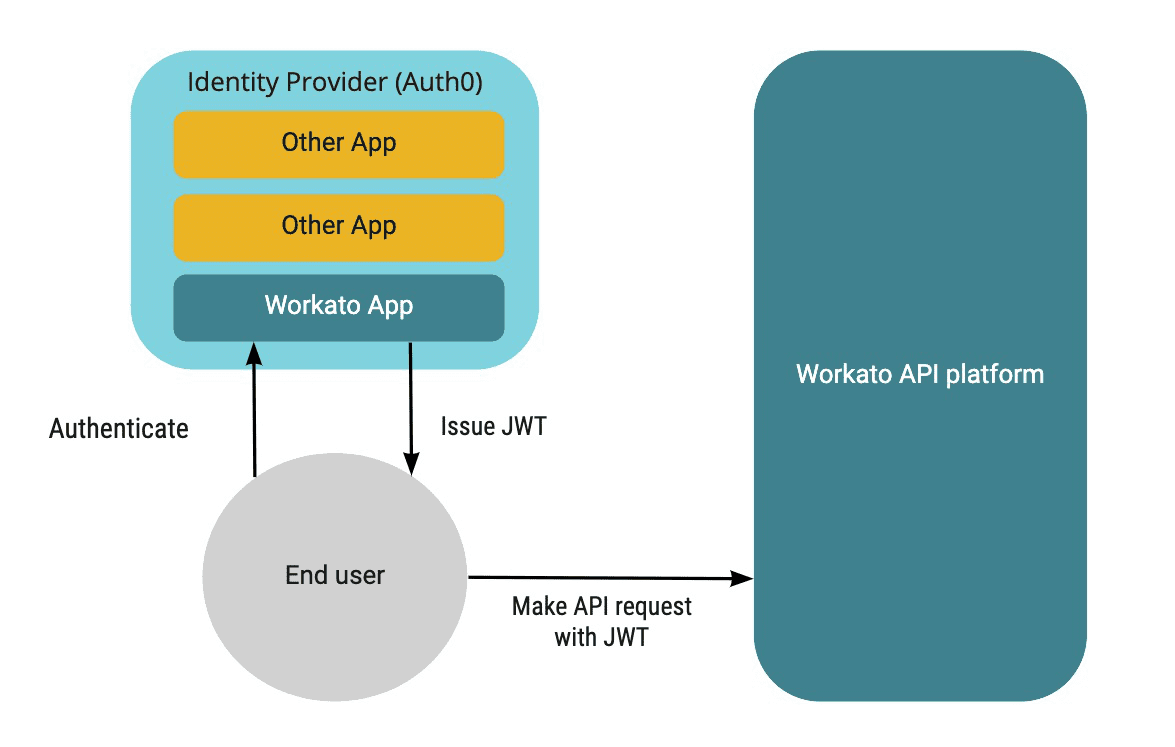 Identity provider issues a JWT to the end user, who uses it to obtain verified access to Workato API platform
Identity provider issues a JWT to the end user, who uses it to obtain verified access to Workato API platform
# Access profile key claim
When Workato receives an incoming request, the JWT is checked to see if it contains a valid token. This is done to determine that the request is coming from a valid access profile. If no valid token value is found, the API request will return a 401 Unauthorized error.
This token can be included in the JWT in a number of ways. Including the list of default claims described in Supported claims. In some cases, these claims may be required for other purposes. If so, you may provide a Custom claim for access profile key to pass this token.
# How to configure access profile
Workato claim works with most identity providers, including ADFS (opens new window), OneLogin (opens new window), and Okta (opens new window).
The following example shows how to configure an access profile with Okta.
# Configure Authorization server
Create an application in Okta and obtain the discovery URL:
Go to Security > API, then Add Authorization Server:
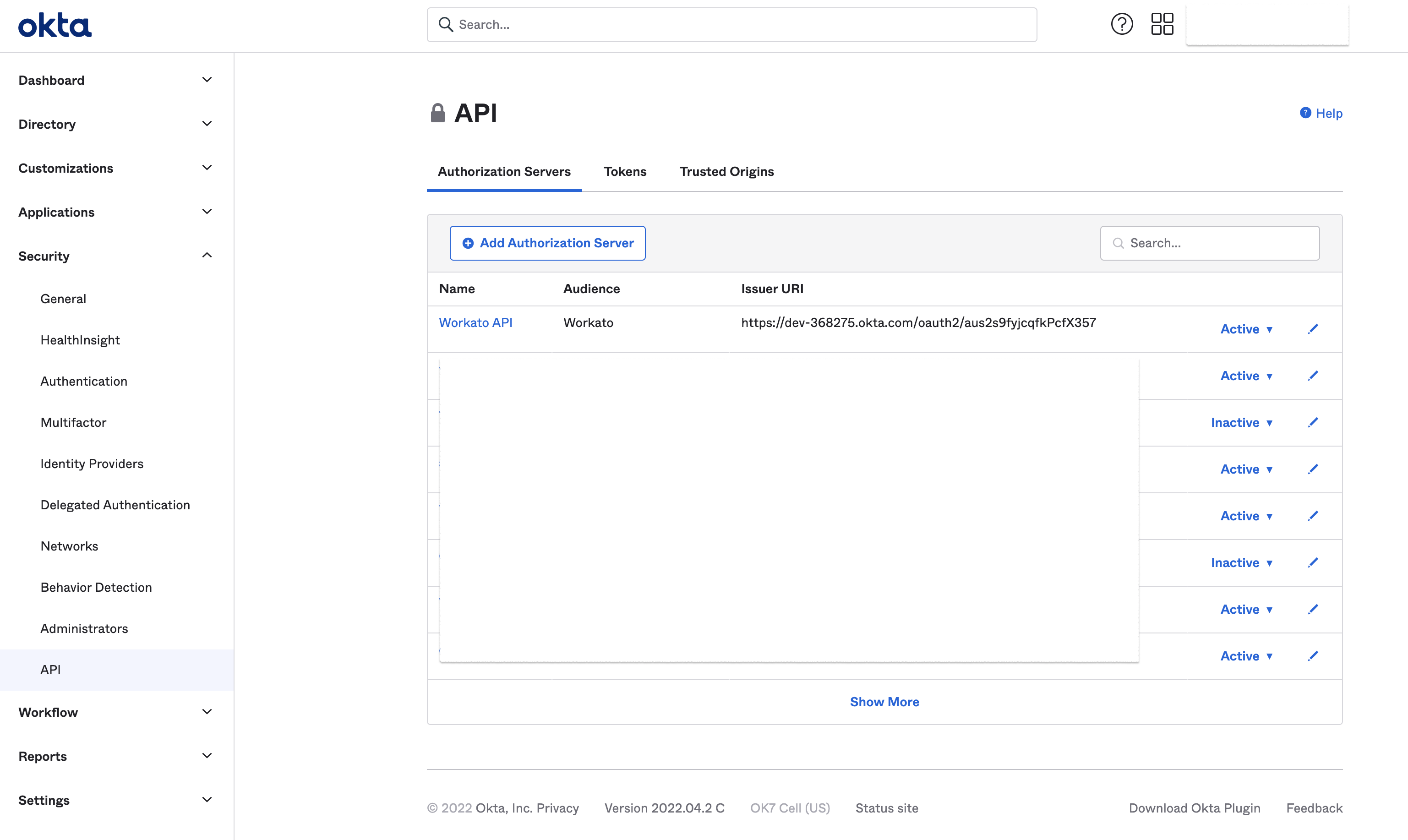 Create Okta API
Create Okta API
Define the name, audience, and provide a useful description.
When the authorization server is created, obtain the Discovery URL (opens new window).
You will need this in the next section. It should look like this https://acme.okta.com/oauth2/aushqgufq8Ir4qSrw357/.well-known/openid-configuration.
# Create Workato access profile
Configure an access profile in Workato and obtain the key.
Go to API platform > Clients. Learn more about API clients.
 Open Workato API platform
Open Workato API platform
Create a new access profile for a your client. Select OpenID Connect as the authentication method.
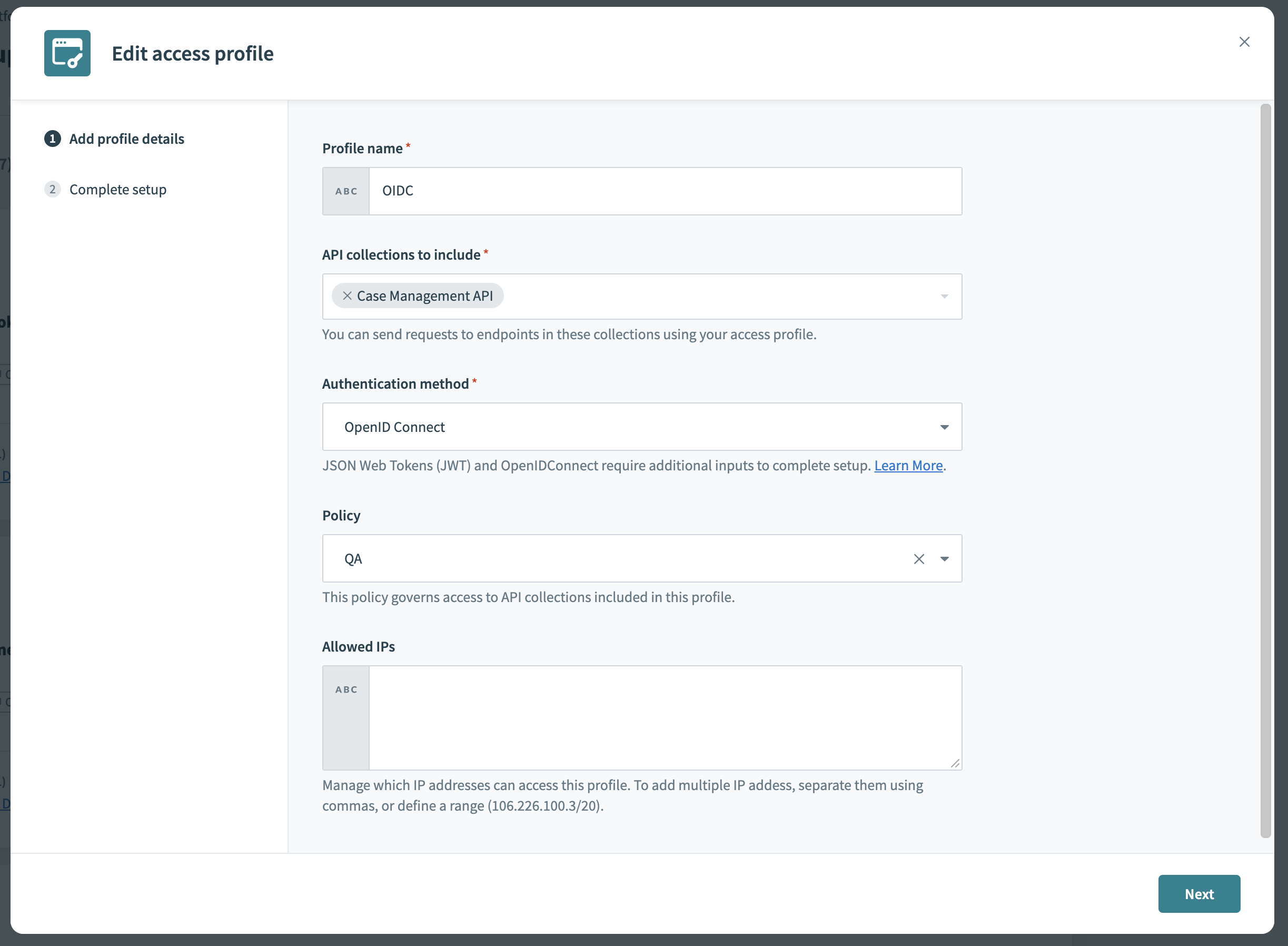 Choose OpenID Connect
Choose OpenID Connect
Paste the Discovery URL that you obtained in the previous section.
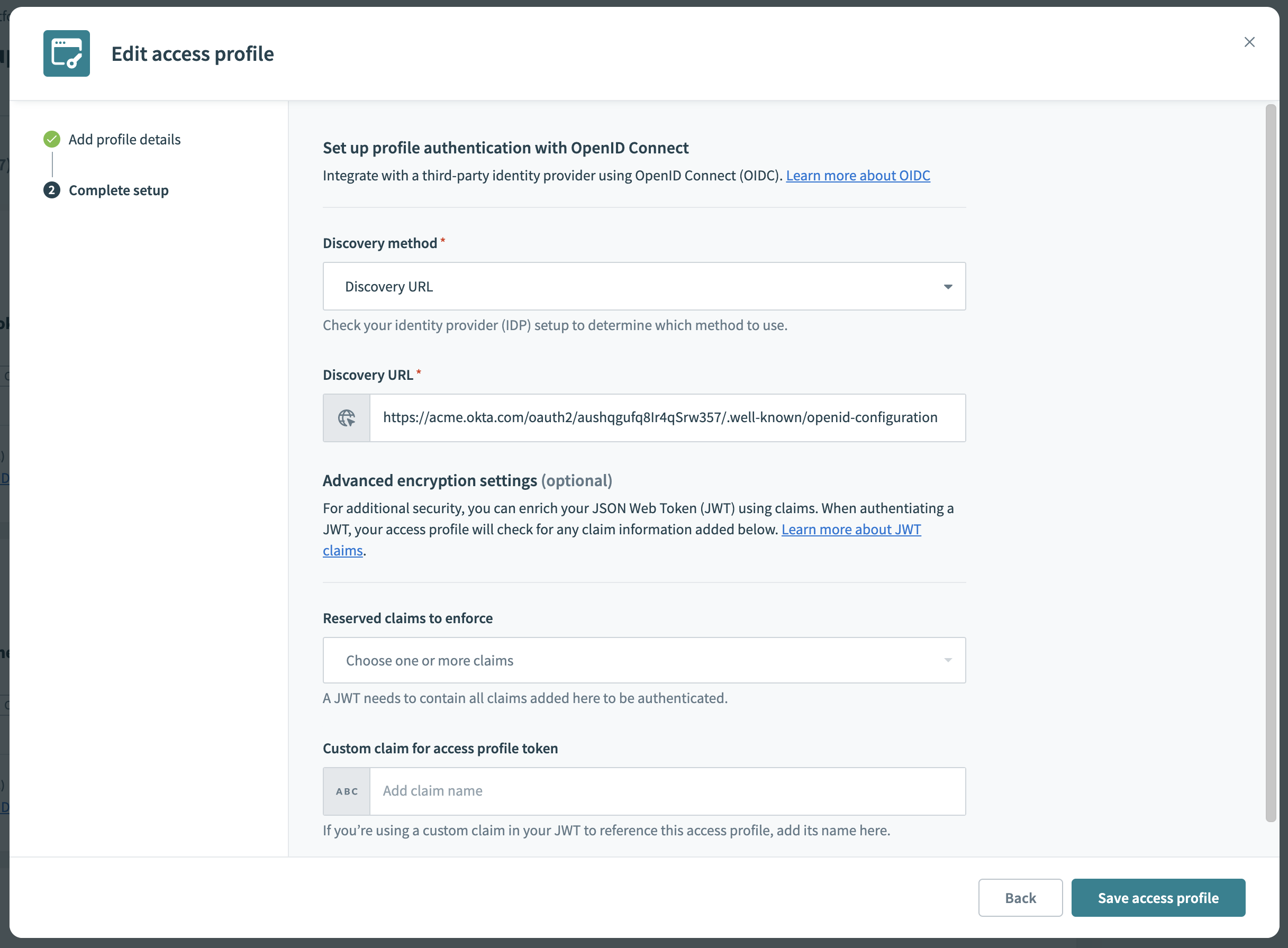 Provide Discovery URL
Provide Discovery URL
Optionally, apply advanced settings, then click Save access profile.
Locate and copy the key to the access profile you created:
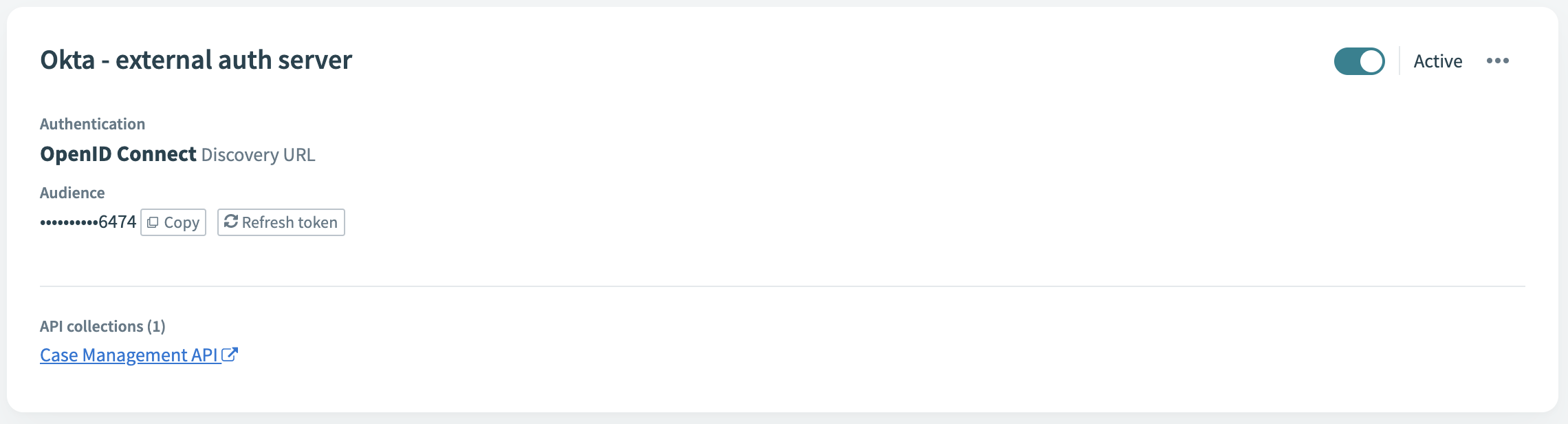 Copy
Copy
# Configure JWT claim
Configure the Okta authorization server to include the access profile key.
Go back to the Authorization server in Okta and find the Claims tab:
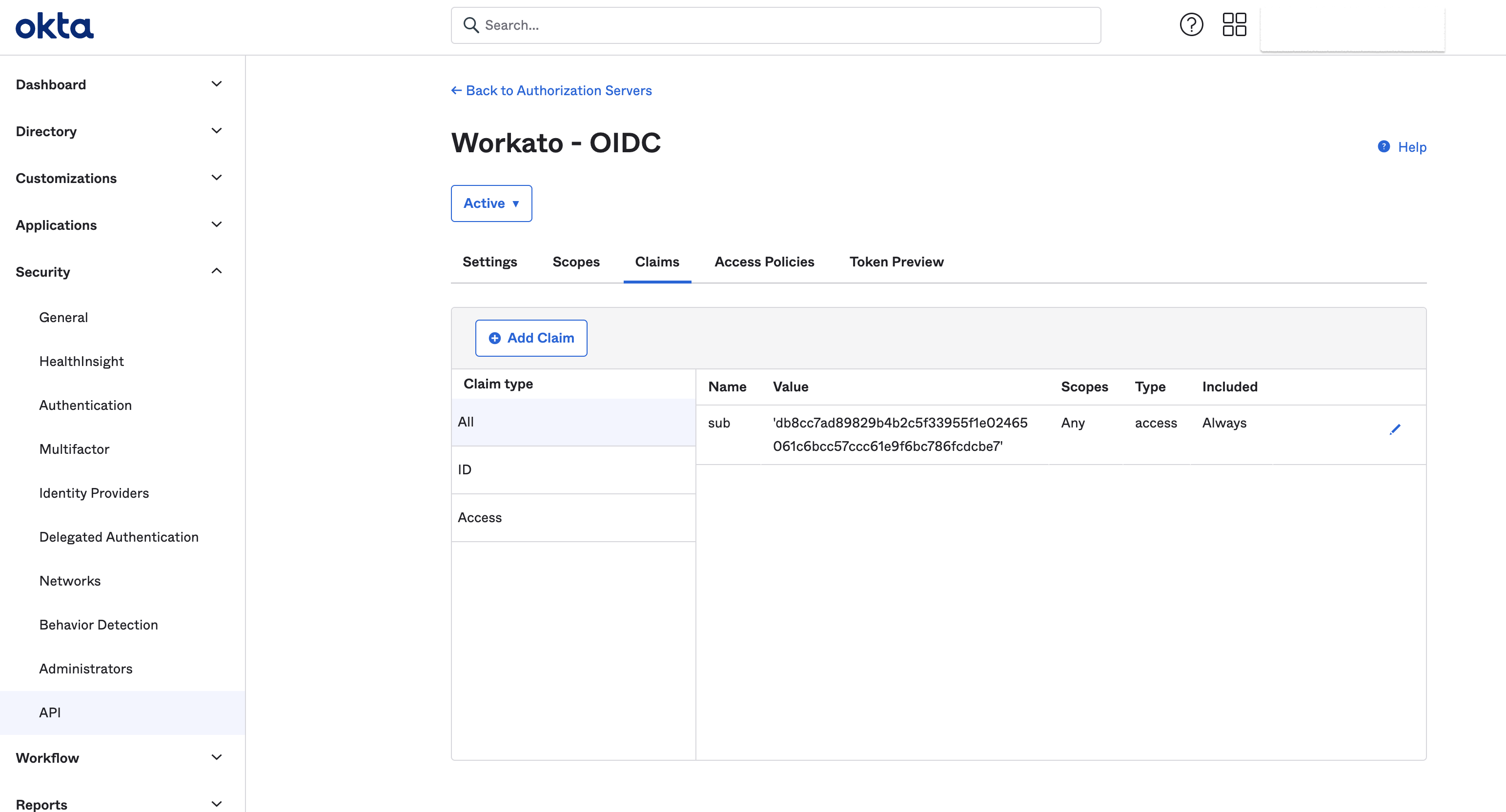 Configure custom claim value
Configure custom claim value
Edit the claim that you chose for passing the access profile key.
Paste the access profile key in the Value field. Ensure that it is wrapped in single quotes ':
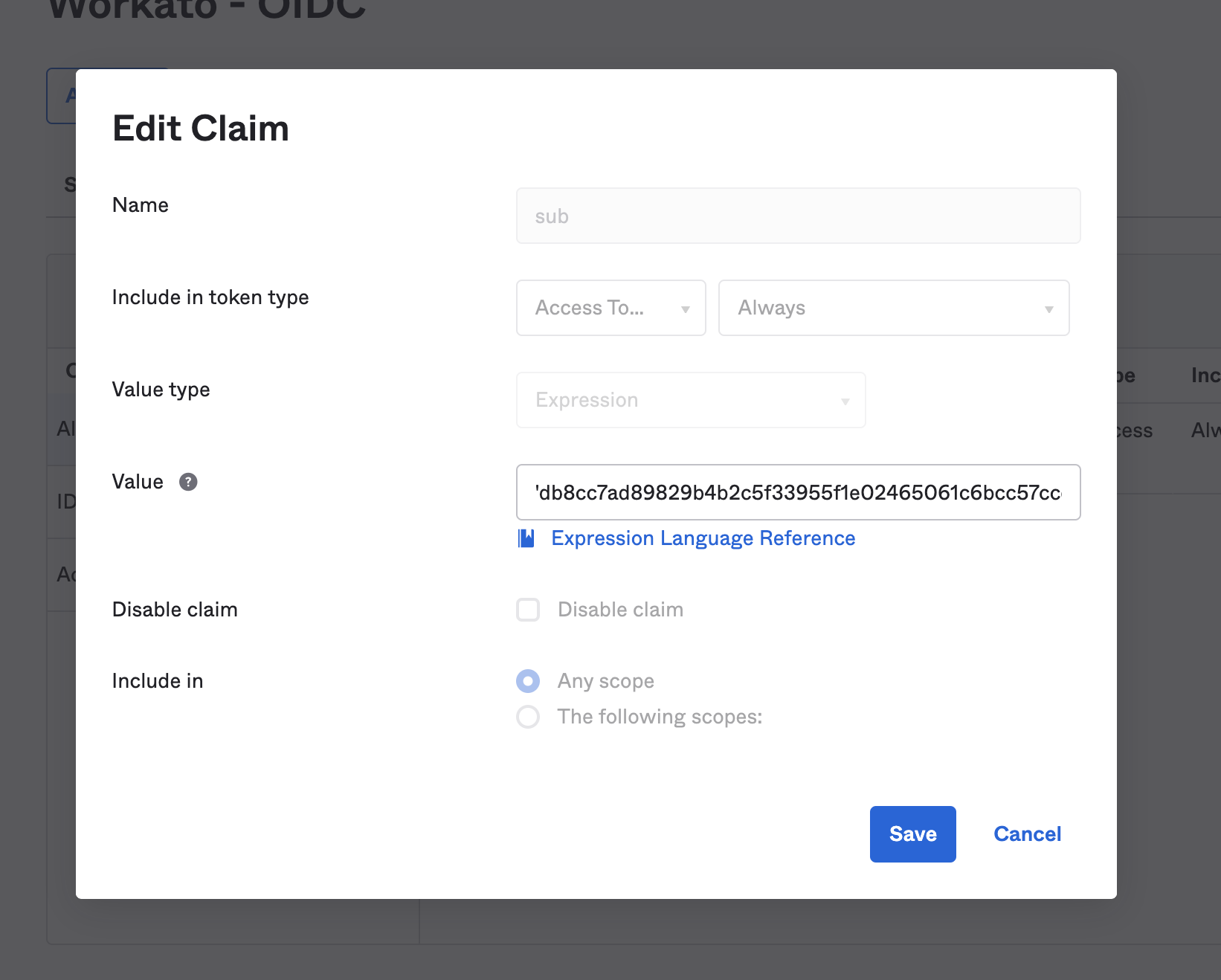 Paste access profile key
Paste access profile key
Setup is now complete. All tokens generated by this authorization server will now be accepted and validated by API platform.
# Signing key rotation
IdPs often rotate signing keys to ensure a better security posture. This will be automatically reflected in the contents of the discovery URL. Workato will internally update the signing key and associated key IDs to ensure there is no disruption to API traffic.
Last updated: 5/2/2024, 8:17:51 PM