# How to connect to Microsoft Entra ID
Connecting to Microsoft Entra ID (formerly Azure Active Directory) on Workato is a multistep process involving configuration steps in Microsoft Entra ID and Workato.
MICROSOFT MFA ENFORCEMENT
Microsoft is rolling out mandatory multi-factor authentication (MFA) (opens new window) gradually to different applications and accounts in phases. This enforcement will continue throughout 2025 and beyond.
We strongly recommend enabling MFA now for all Microsoft accounts used with Workato to avoid service disruptions from short-notice enforcement changes.
Complete the following steps to maintain uninterrupted service:
Enable MFA for your Microsoft organization following Microsoft's MFA setup guide (opens new window).
Reconnect your Microsoft connection in Workato.
Complete the OAuth flow with MFA when prompted.
Test your recipes to ensure they work with the updated connection.
# Create the Workato app in Microsoft Entra ID
You must complete the following steps to create the Workato app in Microsoft Entra ID:
- Register your application
- Grant your application permissions
- Generate a client secret for your application
# Register your application
Register your Workato application with Microsoft Entra ID.
Sign in to Microsoft Entra ID (opens new window).
Select App registrations.
On the resulting page, click + New registration.
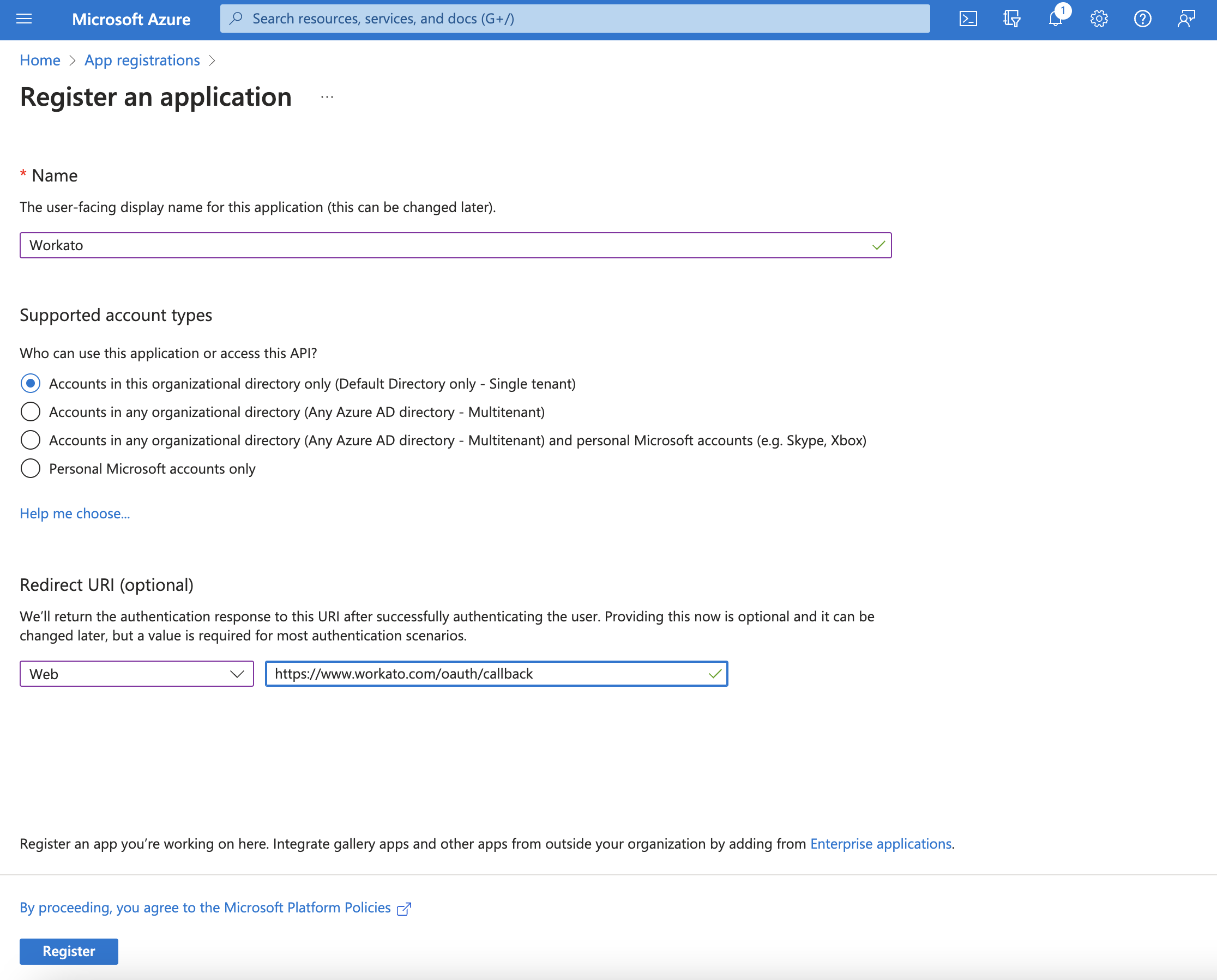
Name your application. This is the user-facing display name for this application. Microsoft allows you to change this name later.
 Name your application
Name your application
In Supported account types, select the first option, Accounts in this organizational directory only.
In the Redirect URI field, set the platform type to Web and provide the following redirect URI: https://www.workato.com/oauth/callback.
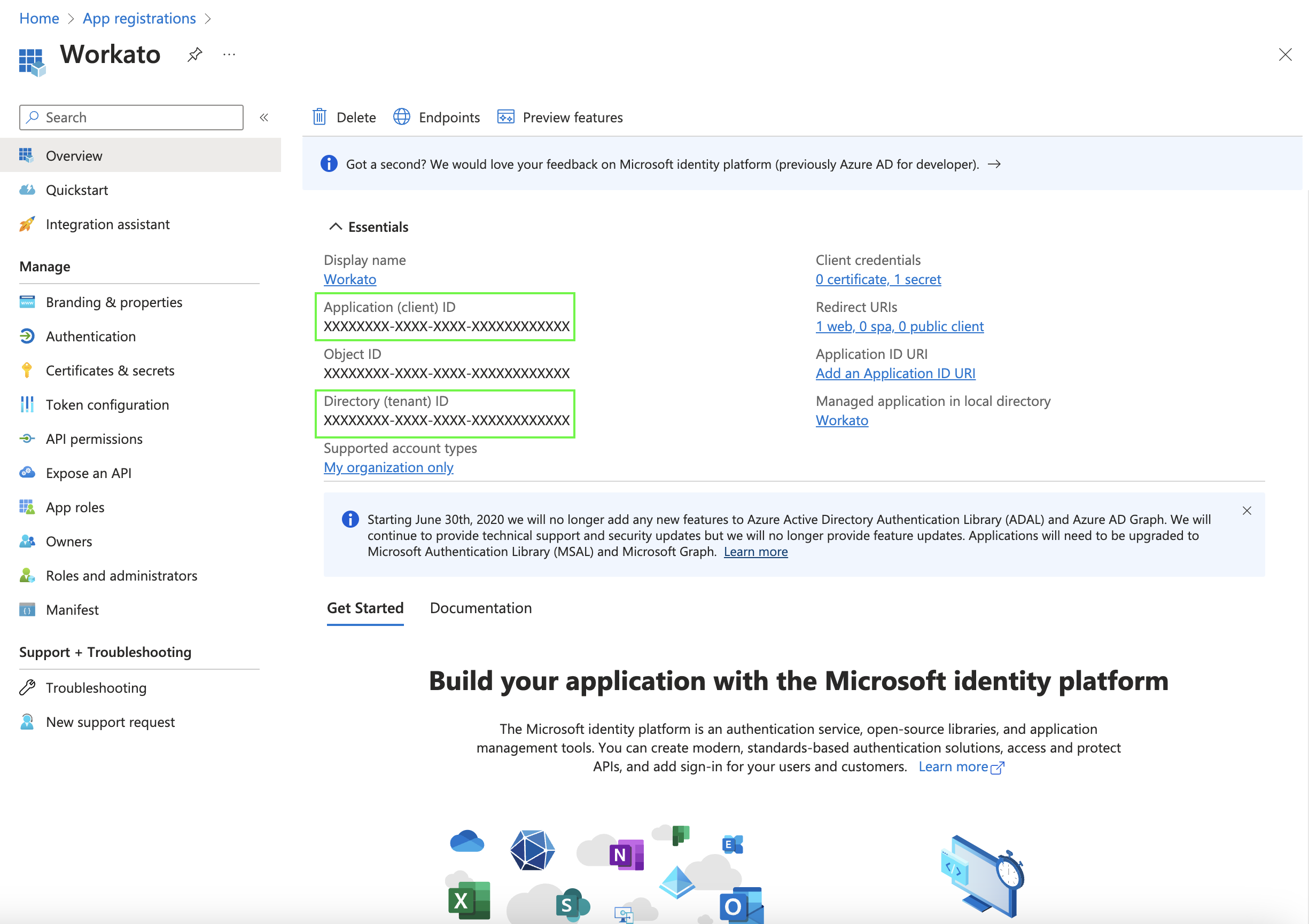
The next page displays the details of the newly-created application. Pay attention to the Application (client) ID and the Directory (tenant) ID. You will need these values later to authenticate in Workato.
 Take note of the Application (client) ID and Directory (tenant) ID
Take note of the Application (client) ID and Directory (tenant) ID
# Assign permissions to your application
Now it's time to assign permissions to our Workato application.
These instructions demonstrate how to grant the minimum permissions necessary to establish a connection with Workato. The permissions you need are variable and based on your use case. See the Microsoft Entra ID permissions section for additional permissions you may need to assign to your Workato application in order for it to perform optimally.
Select API permissions from the left navigation sidebar.
Click + Add a permission.
Click Microsoft Graph to open the permissions interface.
 Open the permissions interface
Open the permissions interface
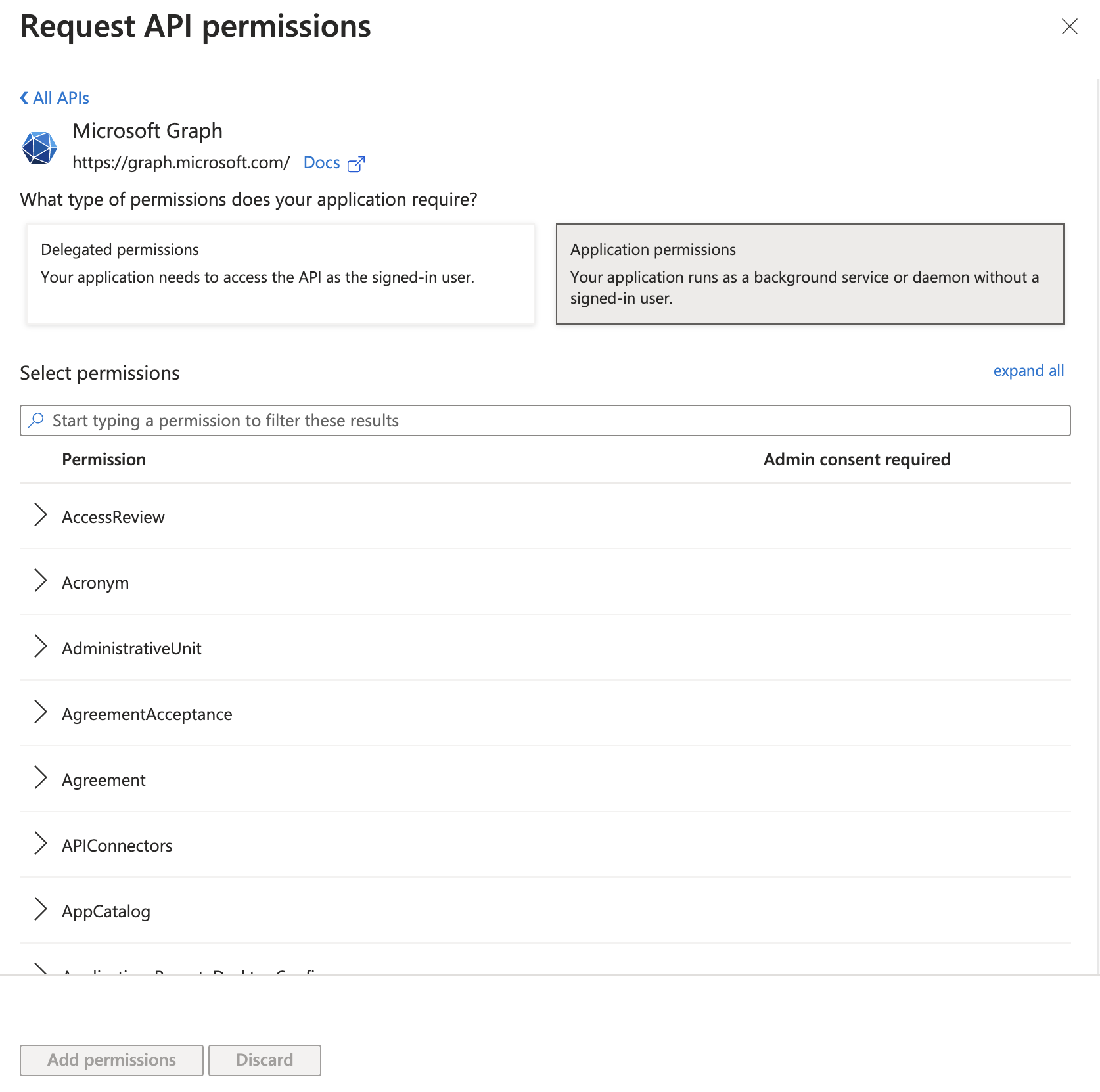
Select Application permissions.
 Select application permissions
Select application permissions
Scroll to User. Add the User.Read.All and User.ReadWrite.All permissions, along with any other necessary permissions.
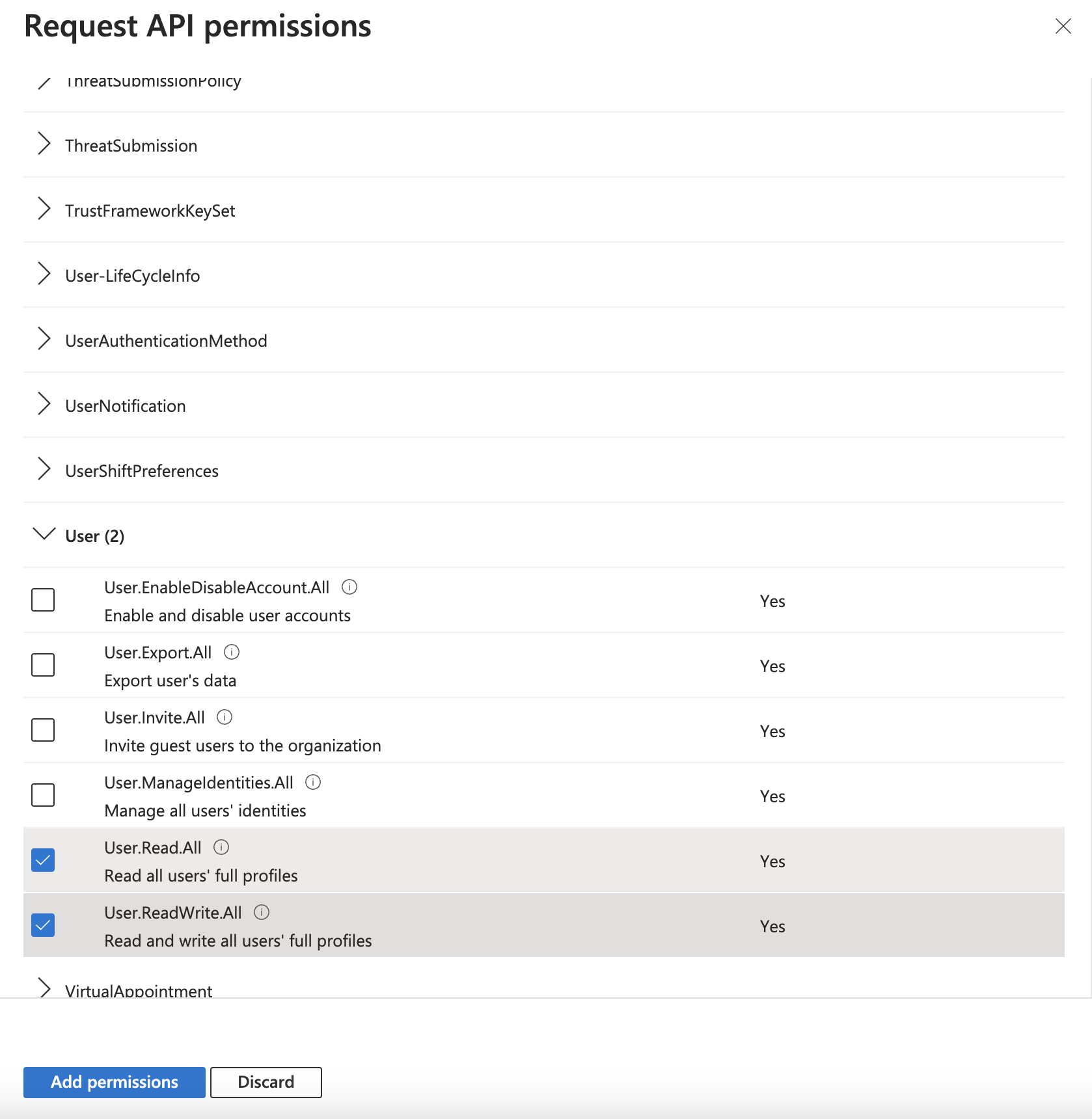 Select the necessary permissions
Select the necessary permissions
Click Add permissions.
You will see these permissions added to Microsoft Graph. However, you will need admin approval to grant them to your application officially.
If you are logged in with an administrator account, click Grant admin consent for Default Directory.
Once admin consent is granted, Microsoft updates the Status column to Granted.
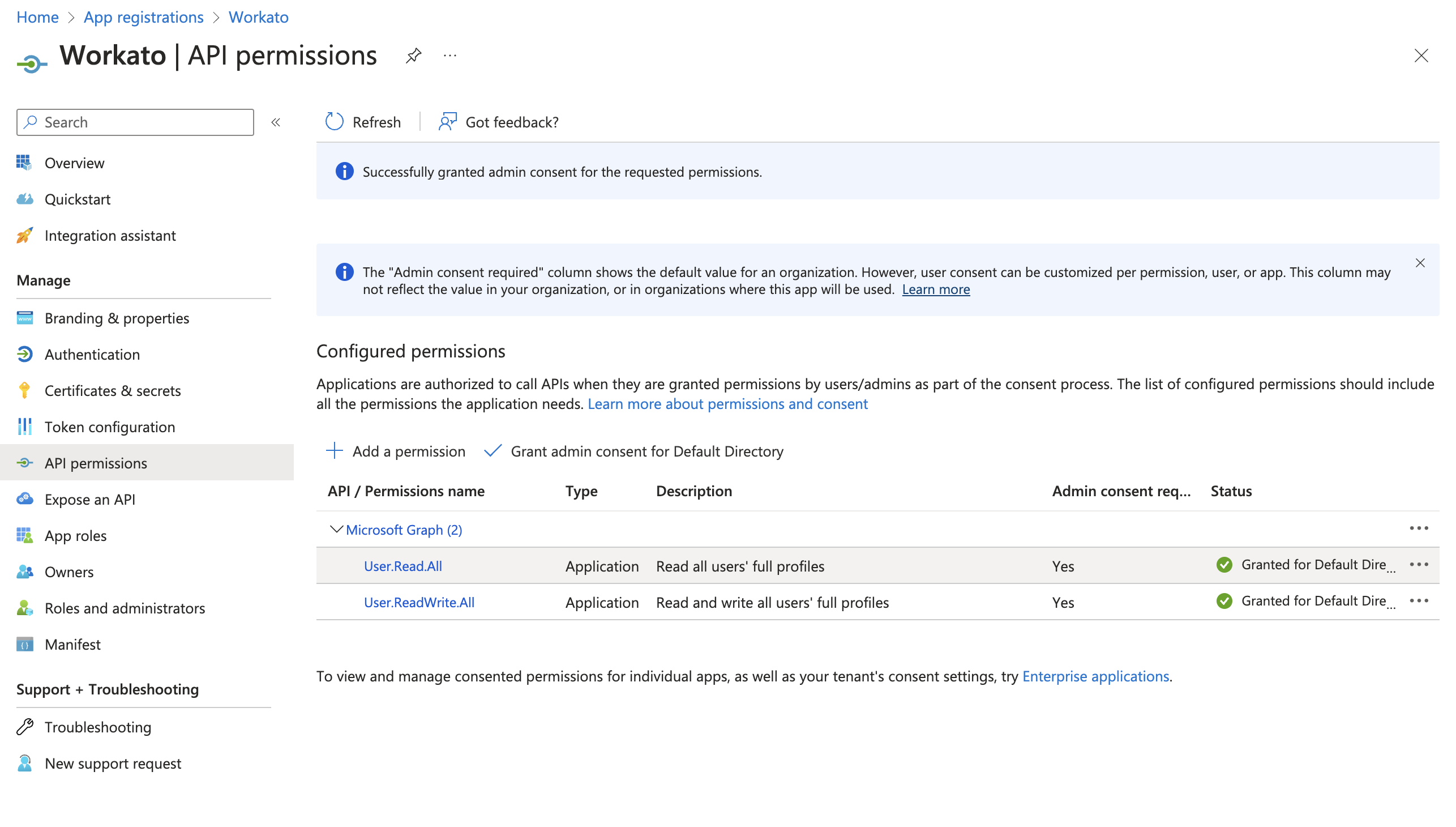 Once admin consent is granted, Microsoft updates the Status column
Once admin consent is granted, Microsoft updates the Status column
# Generate a client secret for your application
Select Certificates & secrets from the left navigation sidebar.
Click + New client secret.
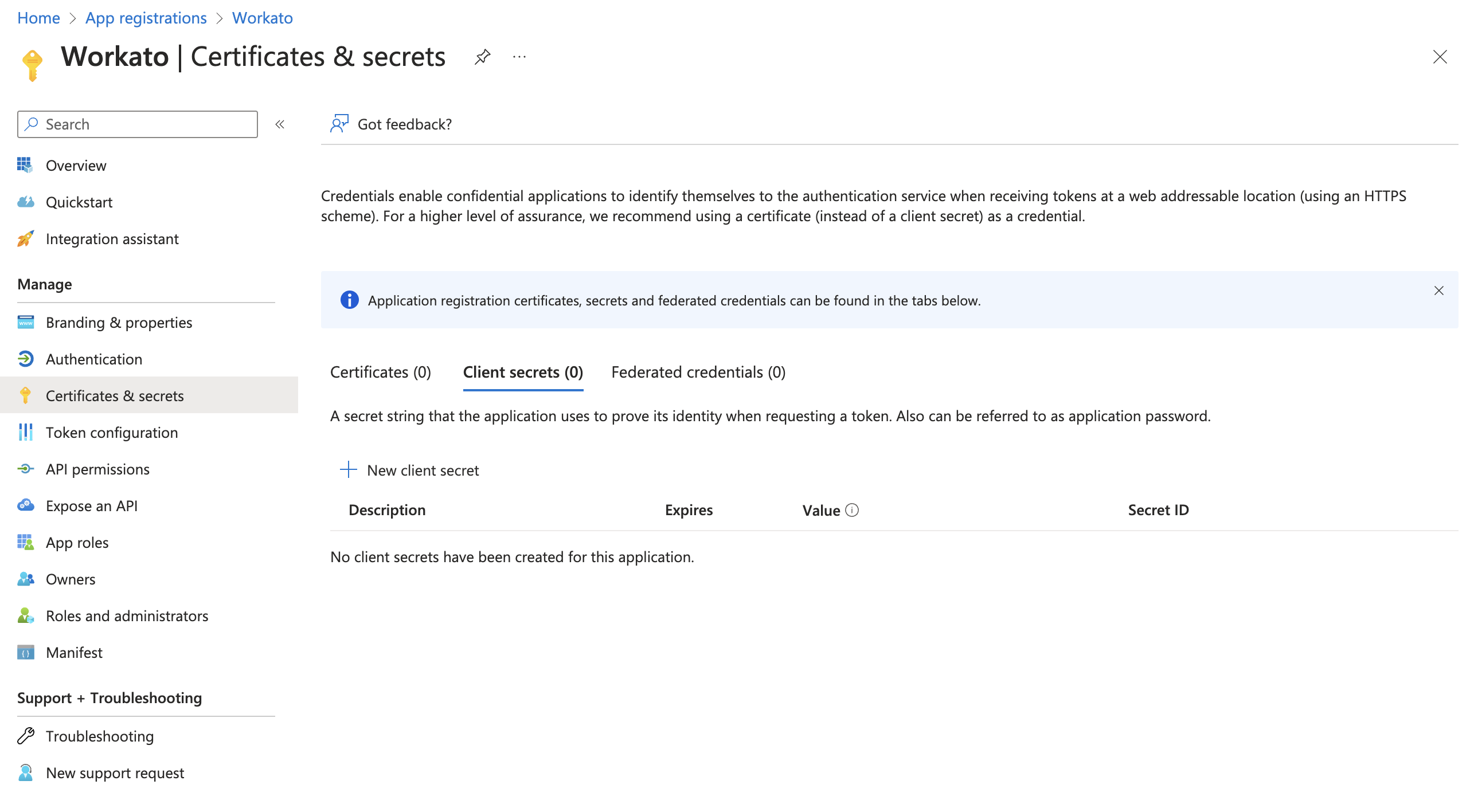 Create a new client secret
Create a new client secret
In the interface that appears, provide a description of the secret and determine when the secret will expire.
Copy and save the Value in a safe place. This is the only time Microsoft Entra ID displays this value.
# Connect to Microsoft Entra ID in Workato
Configure the following fields in Workato.
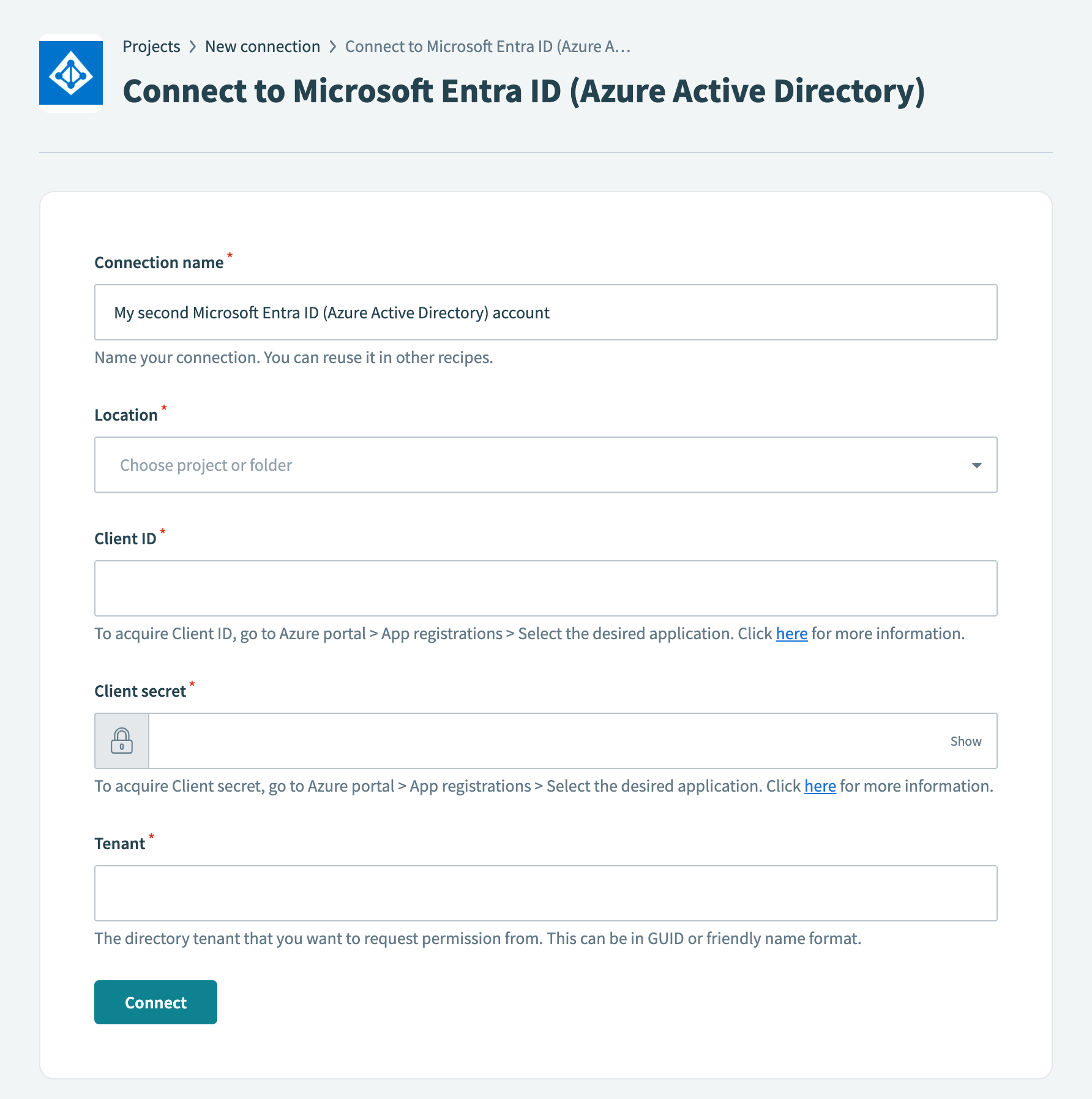 Connect to Microsoft Entra ID in Workato
Connect to Microsoft Entra ID in Workato
- Connection name
- Name your connection.
- Location
- Choose a location (folder) for your connection.
- Client ID
- Provide your Client ID, which Azure refers to as the Application (client) ID. Obtain this value by navigating to Azure portal > App registrations. Select your application and copy the Application (client) ID.
- Client secret
- Provide your client secret, which Azure refers to as the secret Value. This was obtained in Step 1.3.
- Tenant
- Provide the directory tenant from which you plan to request permission. Azure refers to this as the Directory (tenant) ID. Obtain this value by navigating to Azure portal > App registrations. Select your application and copy the Directory (tenant) ID.
Click Connect.
# Permissions
There are two types of permissions Delegated permissions and Application permissions that you can assign to your application. To perform optimally, Microsoft Entra ID requires the following Microsoft Graph permissions.
Application permissions
Directory.Read.AllDirectory.ReadWrite.AllGroup.ReadWrite.AllGroup.CreateGroup.Read.AllGroupMember.Read.AllGroupMember.ReadWrite.AllUser.ManageIdentities.AllUser.Read.AllUser.ReadWrite.All
Delegated permissions
Directory.Read.AllDirectory.ReadWrite.AllDirectory.AcessAsUser.AllGroup.ReadWrite.AllGroupMember.ReadAllGroup.Read.AllGroup.Read.AllGroupMember.ReadWrite.AllUser.ReadUser.ReadBasic.AllUser.Read.AllUser.ReadWrite.All
FURTHER READING
Last updated: 9/29/2025, 7:36:35 PM