# SAP Connection - Enabling SNC encryption
The SAP Cryptographic Library is the default security product delivered by SAP for performing encryption functions in SAP Systems. You can use it for providing Secure Network Communications (SNC) between various SAP server components or for using the Secure Sockets Layer (SSL) protocol with the SAP application Server. This guide describes how to enable SNC in your own SAP instance and how to configure your on-prem agent to use SNC for encrypted communication.
This process consists of the following steps:
# Prerequisites for configuring SNC
- SAP Cryptographic Library installed on your SAP system: This is included as part of the standard SAP NetWeaver AS installation. If the SAP Cryptographic Library is not available on your SAP system, you can install it by using a separate installation package. Refer to the SAP Note 1848999 (opens new window) for more details.
- SAP system profile parameters configured on the system to enable SNC. Refer to sample profile parameter settings (opens new window).
- SAP BASIS privilege or admin access to the SAP system.
- S-User ID with download rights.
- Download and extract SAP CommonCryptoLib on the OPA server. Refer to the Configure SNC on the Workato OPA server section of our documentation for more details on extraction.
- The SAPCAR utility: This is required to extract the contents from the cryptographic library. If this is not present on your system you must download this utility.
- SAP own certificate under the node
SNC SAPCryptolib. This is extracted from the transaction codeSTRUST. Refer to the Export the SAP SNC certificate section of our documentation for more details.
COMMONCRYPTOLIB AND SAPCAR
You can download the CommonCryptoLib and SAPCAR Utility from SAP Software Downloads (opens new window). To download these packages, the SAP S-USER ID must have valid software download authorizations assigned to it.
# Configure SNC on the Workato OPA server
# 1. Unpacking the SAP commoncryptolib using SAPCAR on your OPA's server
On the server running your OPA, you will need to unpack the SAP commoncryptolib.
This example demonstrates how to configure SNC on the Workato OPA server for MacOS and Windows operating systems. Commands are similar for Linux operating systems.
Make the SAPCAR utility executable.
MacOS:
chmod +x SAPCAR_1200-70007727.EXE
Windows:
This step can be ignored.
Rename SAPCAR file (optional).
MacOS:
mv SAPCAR_1200-70007727.EXE sapcar
Windows:
Right click on the file to rename.
Use SAPCAR utility to unpack SAPCRYPTOLIB.
MacOS:
./sapcar -xf SAPCRYPTOLIBP_8554-70002813.SAR
Expected output:
SAPCAR: processing archive SAPCRYPTOLIBP_8554-70002813.SAR (version 2.01)
SAPCAR: 4 file(s) extracted
Windows:
sapcar -xf SAPCRYPTOLIBP_8554-20011729.SAR
Expected output:
SAPCAR: processing archive SAPCRYPTOLIBP_8554-20011729.SAR (version 2.01)
SAPCAR: 8 file(s) extracted
Create a folder with the name sec in your OPA server. This file is used to hold files required for SNC connections. Move the files that were extracted in Step 3 to this folder.
LOCATION OF SEC FOLDER
Place the sec folder inside your OPA installation directory.
# 2. Set the SECUDIR and SNC_LIB variables
Set the SECUDIR and SNC_LIB environment variables. These variables tell the server where to look for the certificates required for an SNC encrypted login and which file is used as the SAP cryptographic library.
ENVIRONMENT VARIABLES
Start OPA from same terminal where you are setting these environment variables. Alternatively, ensure the echo command reflects the correct values in the terminal from where you intend to start the OPA. You can set these variables in the .bashrc file to save the values permanently.
Set the SECUDIR and SNC_LIB variables.
ENVIRONMENT VARIABLE SNC_LIB
The value of the environment variable SNC_LIB varies based on the operating system you use. For example:
- MacOS:
libsapcrypto.dylib - Windows:
sapcrypto.dll - Linux:
libsapcrypto.so
MacOS:
export SECUDIR=<directory path for sec folder>
export SNC_LIB=<OPA installation directory>/sec/libsapcrypto.dylib
Windows:
Right click This PC, select properties and go to Advanced system settings.
Under the Advanced tab, click Environment Variables.
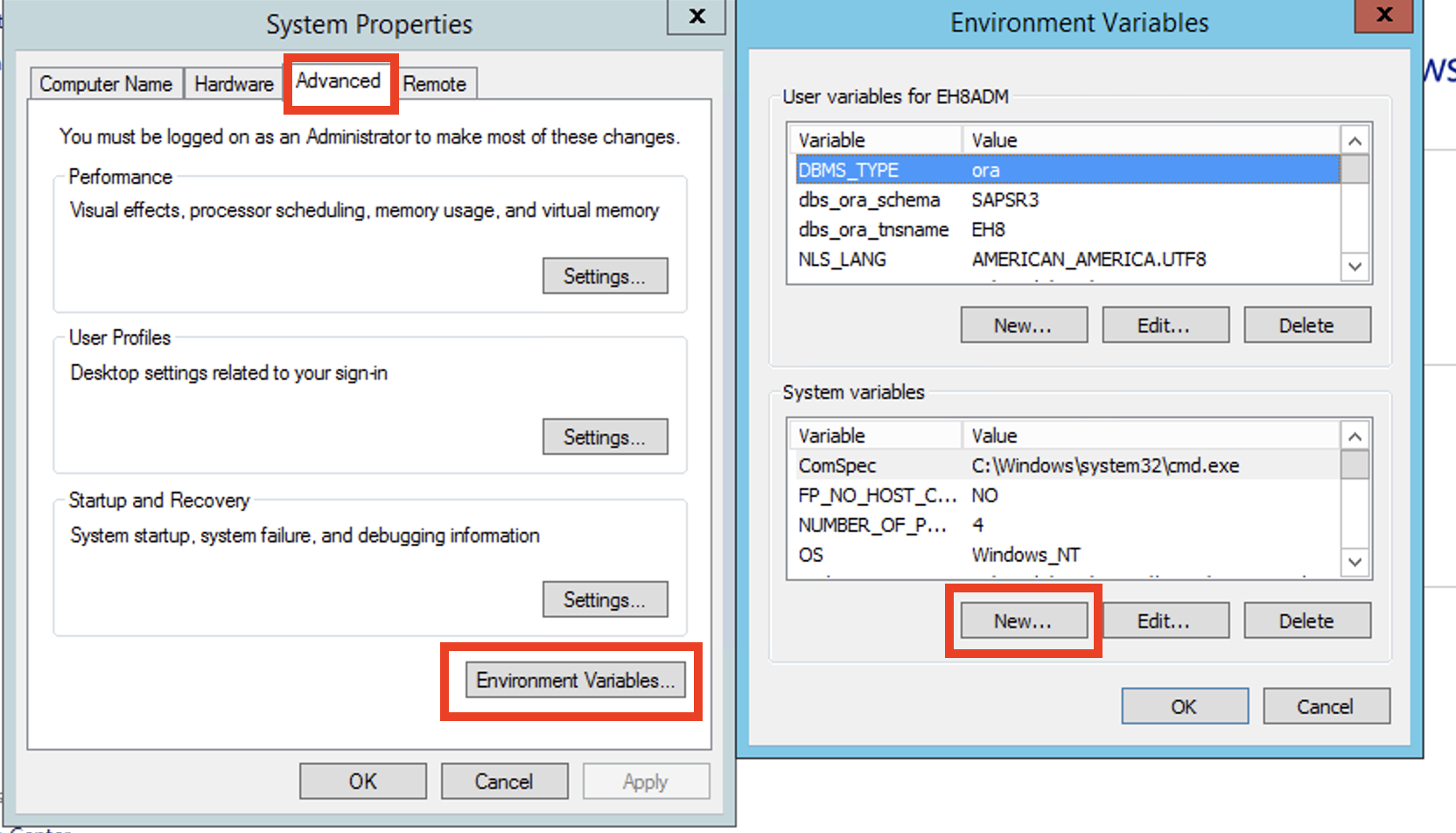
Add new System variables: SNC_LIB and SECUDIR.
Confirm if the environment variables are set correctly.
MacOS:
echo $SECUDIR
echo $SNC_LIB
Windows:
Ensure that SNC_LIB and SECUDIR are included in the list of System variables.
# 3. Generate client certificate
The steps in this section outline the process to create a client certificate which is imported into your SAP system. Your OPA uses the client certificate to verify its identity. SAP also requires a copy of the certificate to trust your OPA's attempt to connect and this is done using sapgenpse.
Create a self-signed certificate using sapgenpse. You are prompted to provide a PSE PIN and the distinguished name of your PSE. In this example, we have given it the canonical name workato.
PSE PIN AND DISTINGUISHED NAME
Avoid using special characters and spaces while setting the canonical name and PSE PIN.
MacOS:
./sapgenpse gen_pse -v -p <OPA installation directory>/sec/workato.pse
Windows:
sapgenpse gen_pse -v -p <OPA installation directory>\sec\workato.pse
Expected output:
Got absolute PSE path "<OPA installation directory>/sec/workato.pse".
Please enter PSE PIN/Passphrase: ************
Please reenter PSE PIN/Passphrase: ************
get_pse: Distinguished name of PSE owner: CN=workato
Supplied distinguished name: "CN=workato"
Creating PSE with format v2 (default)
succeeded.
certificate creation... ok
PSE update... ok
PKRoot... ok
Generating certificate request... ok.
Certificate Request:
Signed Part:
Subject: CN=workato
Key: rsaEncryption (2048 bits)
Public key fingerprint (MD5): 80:A7:CE:BC:19:A1:4E:E8:63:1F:77:F9:BC:8F:E8:4B
Attributes: None
Signature:
Signature algorithm: sha256WithRsaEncryption (1.2.840.113549.1.1.11)
Signature: <Not displayed>
PKCS#10 certificate request for "<OPA installation directory>/sec/workato.pse":
-----BEGIN CERTIFICATE REQUEST-----
MIICVzCCAT8CAQAwEjEQMA4GA1UEAxMHd29ya2F0bzCCASIwDQYJKoZIhvcNAQEB
BQADggEPADCCAQoCggEBAM1XnlnelNn28WjlPtDd+a2pkOXcOMGoyuO8VlkPHp/r
RxzgZO11ac3fYgmr2iuvWwTFh/cNy+9xoXLlS374m103dFJfICBkH0zus4h2DU33
S+imU57wGyw2YzkptqctA8vYEZFQVnNdjxRcHpsS6RkYeEb8AFs5NOu5ibJpX6gq
i2+CQkiSzFmTpcEgg5Inr42lZxWMflHbx233M9a9UNF5x+Mrj9VuVTV+r2GaYulq
8VrjlD9LXtV8ZPzEv/GAi/UILtsAdwaSdB2mawS8MA2R4BICVpk2CZraDOMQpYmw
YTvkrUV/0+nQ8GWZwMqQ8+fsJUPKjyGCam4J8aSkx4MCAwEAAaAAMA0GCSqGSIb3
DQEBCwUAA4IBAQCmXXO0MSgWexOTN/3AIRgljnRnz5/VsamVV01KOV460AC3Eh67
N14u6pjKbJUe29RNEpML8DbmDnsHQYm8WPT5GnTdt08m7M1csswSq4dagIkUgJB5
LFT/oofJ3V7m/idN9AOb+LI9kEsFh6Z2LBC2umP45qSyWI8QFCsF6a0FB7Xy1Pok
voOODcA8KTkhN24hkKtHkZNKoFIkniSATvcJmu10iVKuYmeQem5WnfOPmH4Gpf7p
WMlgnEqEvhmy+MdLWubl6mpiBQfPvj9u9jJ/W2BO7kCfVzfFs9WxEKCibh410ReT
SREwV95ePEjIZ4H//txpYgDbzc42Zei8odT0
-----END CERTIFICATE REQUEST-----
You should now see a workato.pse file in your sec folder.
Use this PSE file to create a client certificate workato.crt file in your sec folder.
MacOS:
./sapgenpse export_own_cert -v -p <OPA installation directory>/sec/workato.pse -o <OPA installation directory>/sec/workato.crt -x <PSE PIN>
Windows:
sapgenpse export_own_cert -v -p <OPA installation directory>\sec\workato.pse -o <OPA installation directory>\sec\workato.crt -x <PSE PIN>
Expected output:
Opening PSE "<OPA installation directory>/sec/workato.pse"...
No SSO credentials found for this PSE.
PSE (v2) open ok.
Retrieving my certificate... ok.
Writing to file (PEM-framed base64-encoded)... ok.
Assign the credentials of the current OS user to this PSE to add SSO credentials to the PSE.
OS USER
Your OS username can be different from your SAP username. This should be the name of your user in your server, for example, ec2-user, or root.
MacOS:
./sapgenpse seclogin -p <OPA installation directory>/sec/workato.pse -O [your_os_username]
Windows:
sapgenpse seclogin -p <OPA installation directory>\sec\workato.pse -O [your_os_username]
Expected output:
running seclogin with USER="<OS user>"
Please enter PSE PIN/Passphrase: ************
Added SSO-credentials for PSE "<OPA installation directory>/sec/workato.pse"
# 4. Import SAP system certificate to the PSE
To import SAP system certificate, we require the following file:
The EH8.crt certificate file retrieved in step 1 of the Export the SAP SNC certificate section which is the own certificate of your SAP system. This step allows the PSE to know that the SAP system is trusted.
MacOS:
./sapgenpse maintain_pk -p <OPA installation directory>/sec/workato.pse -a <OPA installation directory>/sec/EH8.crt
Windows:
sapgenpse maintain_pk -p <OPA installation directory>\sec\workato.pse -a <OPA installation directory>\sec\EH8.crt
Expected output:
Please enter PSE PIN/Passphrase: ****
maintain_pk for PSE "<OPA installation directory>/sec/workato.pse"
----------------------------------------------------------------------------
Subject : CN=EH8, OU=I0021153659, OU=SAP Web AS, O=SAP Trust Community, C=DE
PKList updated (1 entries total, 1 newly added)
In the sec folder, run the following command to check if the EH8.crt has been linked successfully. Use sapgenpse to check if the certificate from SAP has been linked successfully.
MacOS:
./sapgenpse maintain_pk -p <OPA installation directory>/sec/workato.pse -l -v
Windows:
sapgenpse maintain_pk -p <OPA installation directory>\sec\workato.pse -l -v
Expected output:
Opening PSE "/Users/sidhantmahajan/Downloads/SNC/sec/workato.pse"...
PSE (v2) open ok.
retrieving PKList
PKList:
Version: 1
Subject: CN=EH8, OU=I0021153659, OU=SAP Web AS, O=SAP Trust Community, C=DE
Issuer: CN=EH8, OU=I0021153659, OU=SAP Web AS, O=SAP Trust Community, C=DE
Serial Number: 0A:20:23:03:30:09:34:01
Validity not before: Thu Mar 30 15:04:01 2023 (230330093401Z)
Validity not after: Fri Jan 1 05:30:01 2038 (380101000001Z)
Public key: rsaEncryption (2048 bits)
Public key fingerprint (MD5): 34:BA:58:F3:8D:09:39:07:CF:AF:46:A6:3B:8E:05:C6
Public key fingerprint (SHA256): 1C:47:70:FA:7C:9D:7A:77:FE:94:3C:D6:65:F5:BE:0D:15:86:01:DA:16:52:43:B0:E6:2D:21:A2:B5:4F:CE:AB
Signature algorithm: sha256WithRsaEncryption (1.2.840.113549.1.1.11)
Certificate fingerprint (MD5): 6B:74:E9:9C:44:6B:68:CB:34:CF:FE:9F:5D:8C:AB:78
Certificate fingerprint (SHA1): E3:D7:DF:21:9C:76:19:AA:C3:1F:CA:3C:97:F1:94:68:50:7F:EA:3D
Certificate fingerprint (SHA256): 0D:F1:63:43:08:41:B1:B5:6F:F8:A4:95:C8:6D:BE:E3:DD:38:5F:70:03:B8:63:6F:D4:8E:00:25:3C:9A:A2:5D
In the sec folder, run the following commands to check if credentials are correct by checking the client certificate, key, and SSO mapping.
MacOS:
./sapgenpse seclogin -p <OPA installation directory>/sec/workato.pse -O [your_os_username] -l
./sapgenpse seclogin -p <OPA installation directory>/sec/workato.pse -l
Windows:
sapgenpse seclogin -p <OPA installation directory>\sec\workato.pse -O [your_os_username] -l
sapgenpse seclogin -p <OPA installation directory>\sec\workato.pse -l
Expected output:
running seclogin with USER="<OS user>"
0 (LPS:OFF): CN=workato
(LPS:OFF): <OPA installation directory>/sec/workato.pse
1 readable SSO-Credentials available
for PSE-file "<OPA installation directory>/sec/workato.pse"
# Configure SNC on SAP system
# 1. Export the SAP SNC certificate
Export the SAP Certificate from the SAP application server. This certificate is then imported to the OPA.
Login to SAP GUI and go to the transaction code STRUST.
Select the SNC SAPCryptolib node and double click the certificate in the Own Certificate section.
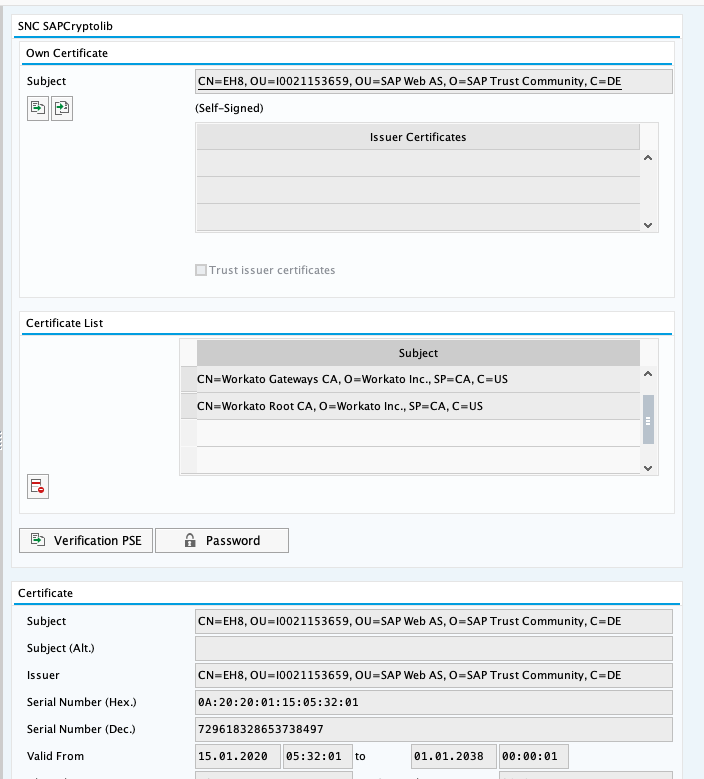
Click the certificate export icon. Then, select Base64 format. In our example, we named it EH8.crt which is inline with our system ID of the SAP system.
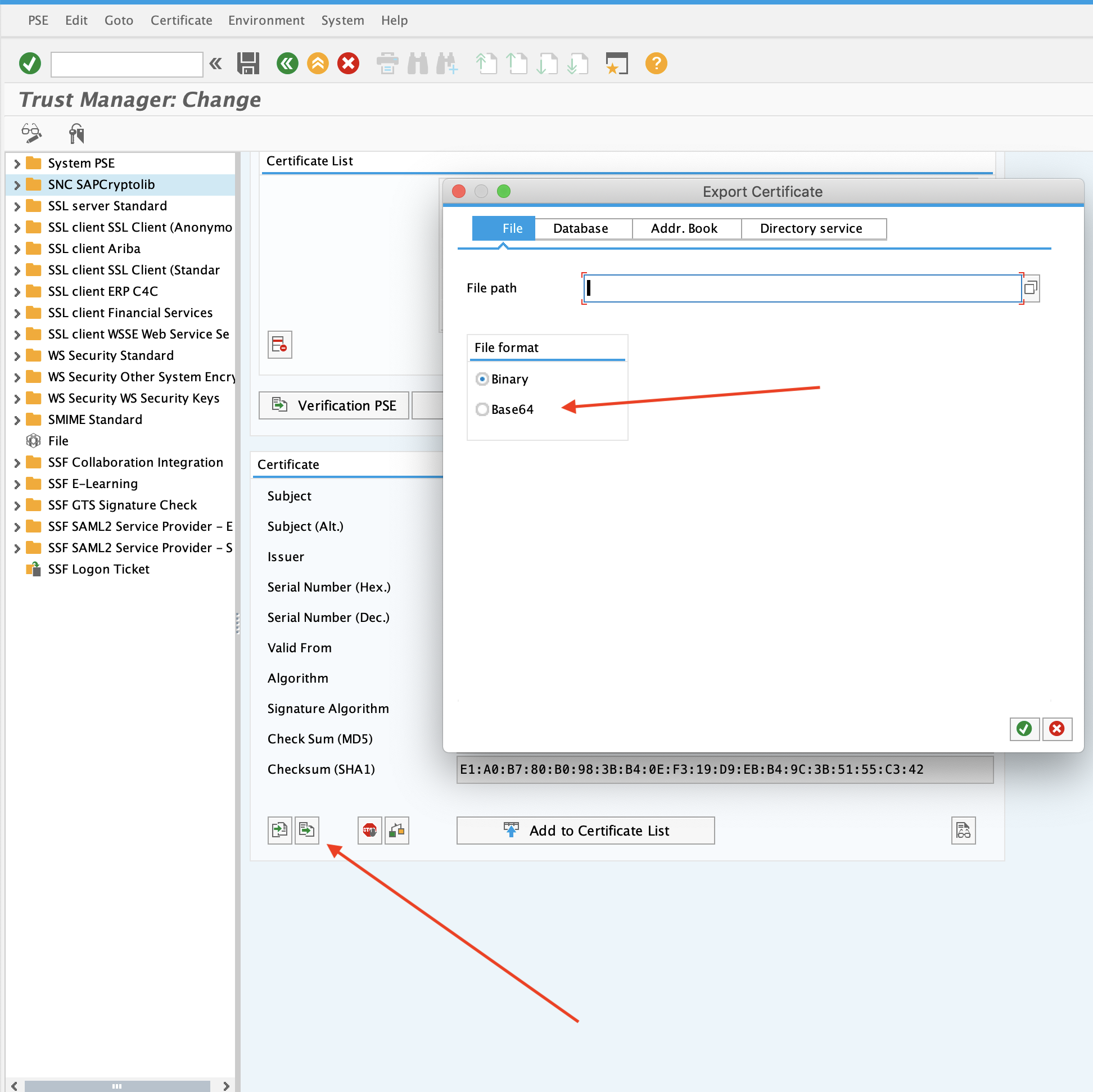
# 2. Import the client certificate
This section outlines the steps required to import the client certificate generated on the OPA side into SAP.
Go to the transaction code STRUST and select the node SNC SAPCrytolib.
Ensure that you are in edit mode and click the certificate import icon, located next to the certificate export icon as shown in the figure in the previous section.
Import the client certificate workato.crt which was generated on the OPA side.
Click Add to certificate list and save.
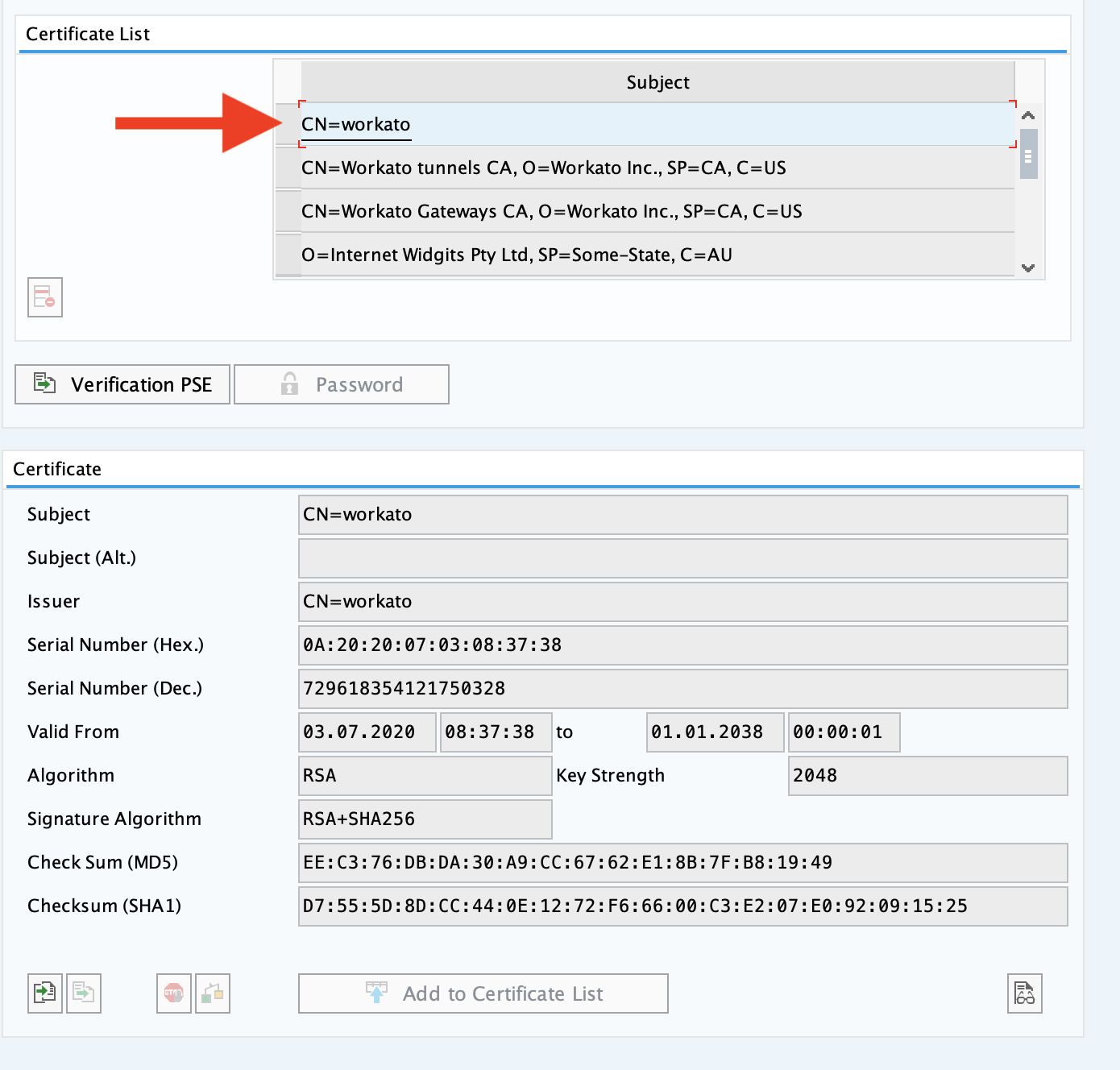
# 3. Mapping client certificate to an integration user in SAP
This section demonstrates how to map the client certificate to an integration user which is used to communicate with Workato.
Go to transaction code SU01, enter the name of the integration user which is being used to communicate with Workato.
Go to SNC tab, enter in the SNC name and click save. The value would be the distinguished name which we defined while generating the client certificate with p: prepended (technically referred as canonical name). In this example, it means the SNC name is p:CN=workato.
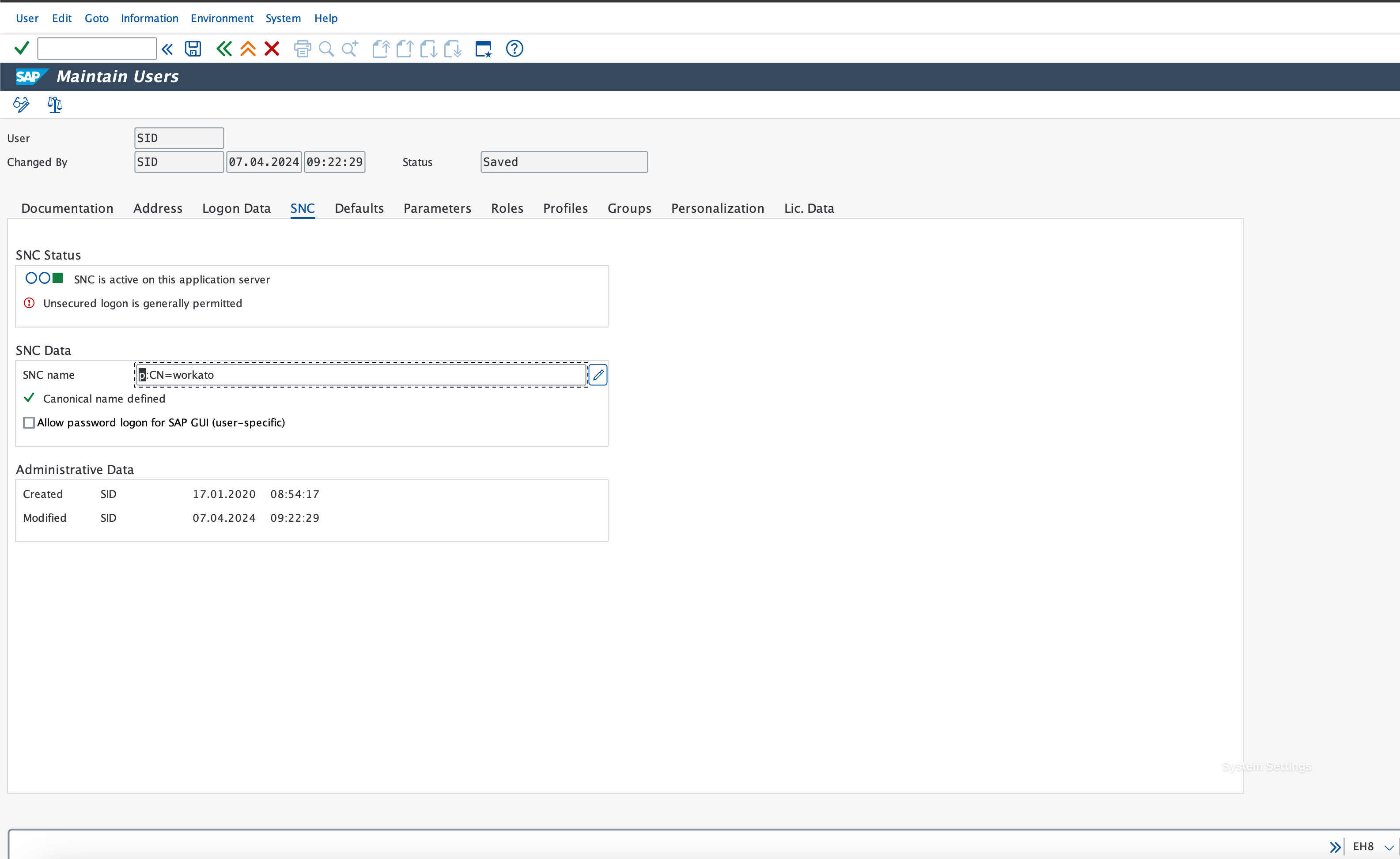
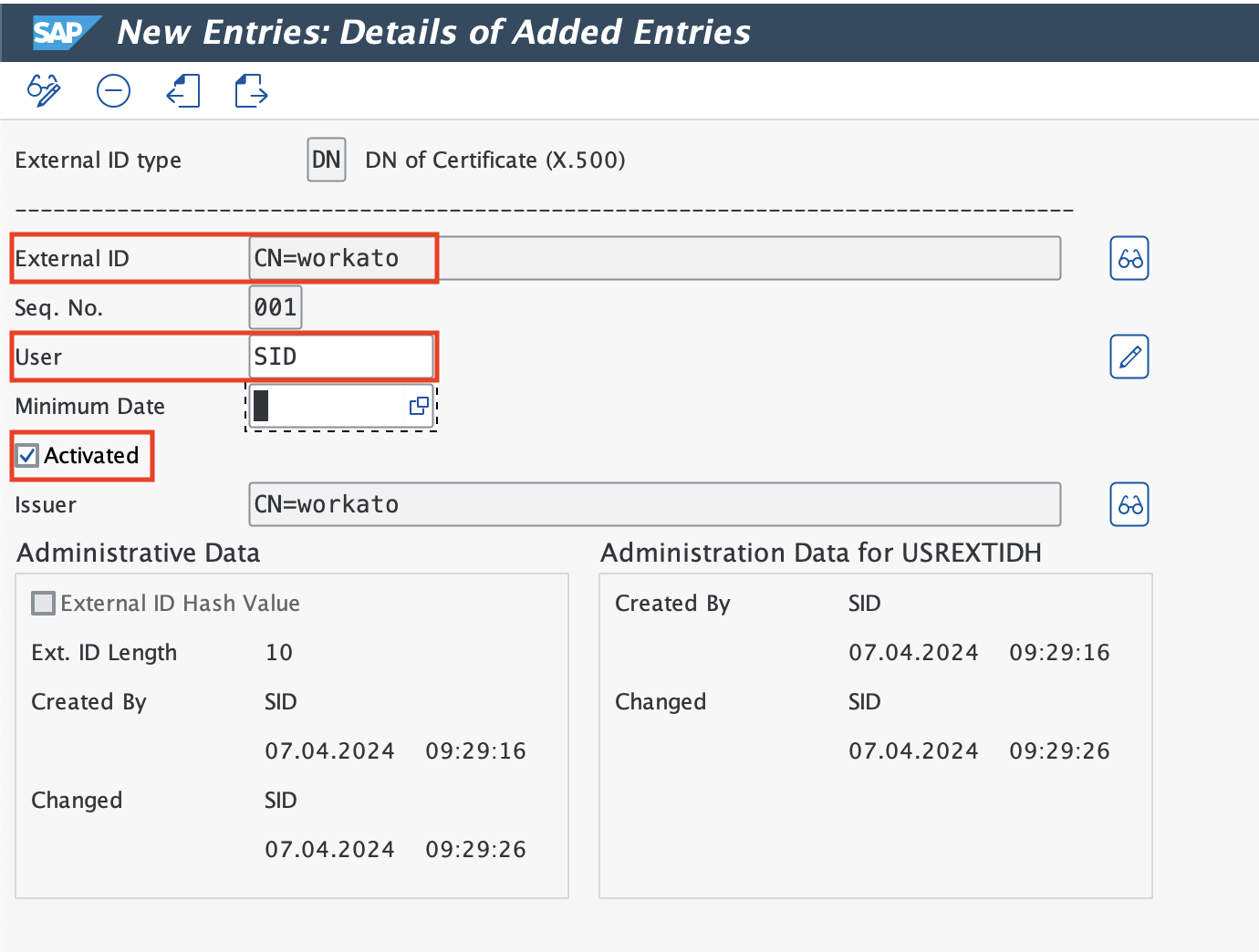
Go to transaction code SM30, enter the table name VUSREXTID.
Maintain the External ID type DN and X where External ID would be the distinguished name of the client certificate with the name of the integration user in the User field.
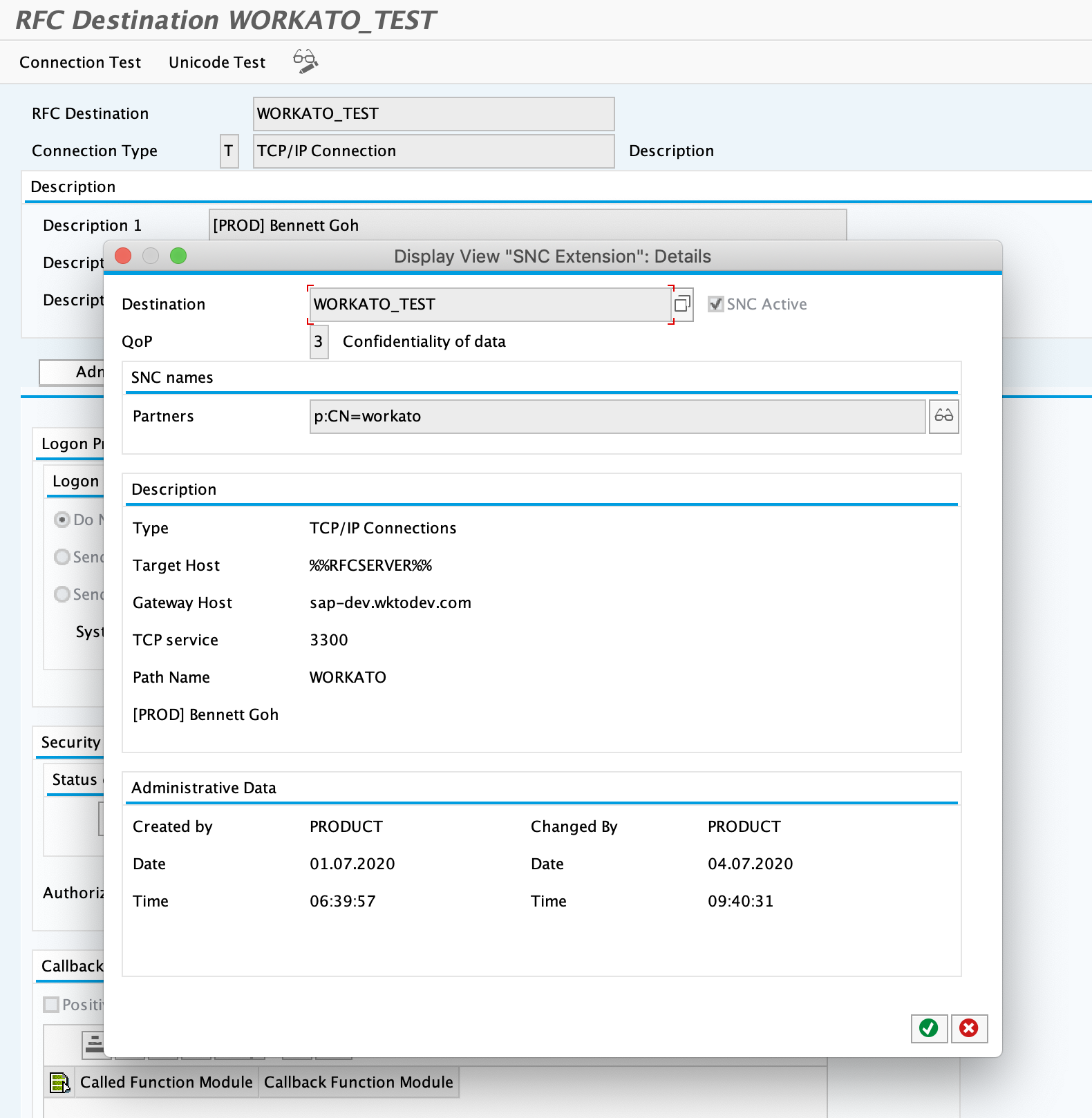
# 4. Alter your RFC destination (if you use the new IDoc trigger)
To use the New IDoc trigger through secured communication, you must enable SNC for the RFC destination dedicated to Workato.
Go to transaction code SM59.
Navigate to the RFC destination dedicated to Workato.
Under the Logon & Security tab, select the SNC button under the Security Options section.
Enter in the quality of protection. In our example, this is set to 3.
Enter the canonical name of the client certificate and click save. In our example, this is p:CN=workato.
# Connection fields
To establish the connection in Workato, configure the SAP profile to reflect the SNC properties. The following important properties are additionally required on the Workato connection page to establish a secured connection:
- Quality of protection: Enables secured network communication.
- Sapcrypto library path: Provide the filesystem path to
libsapcrypto.so(Linux),libsapcrypto.dylib(Mac),sapcrypto.dll(Windows). - SNC partner name: Canonical name of the SAP own certificate extracted in step 1 of this section.
- SNC name: Canonical name of the client certificate.
# Summary
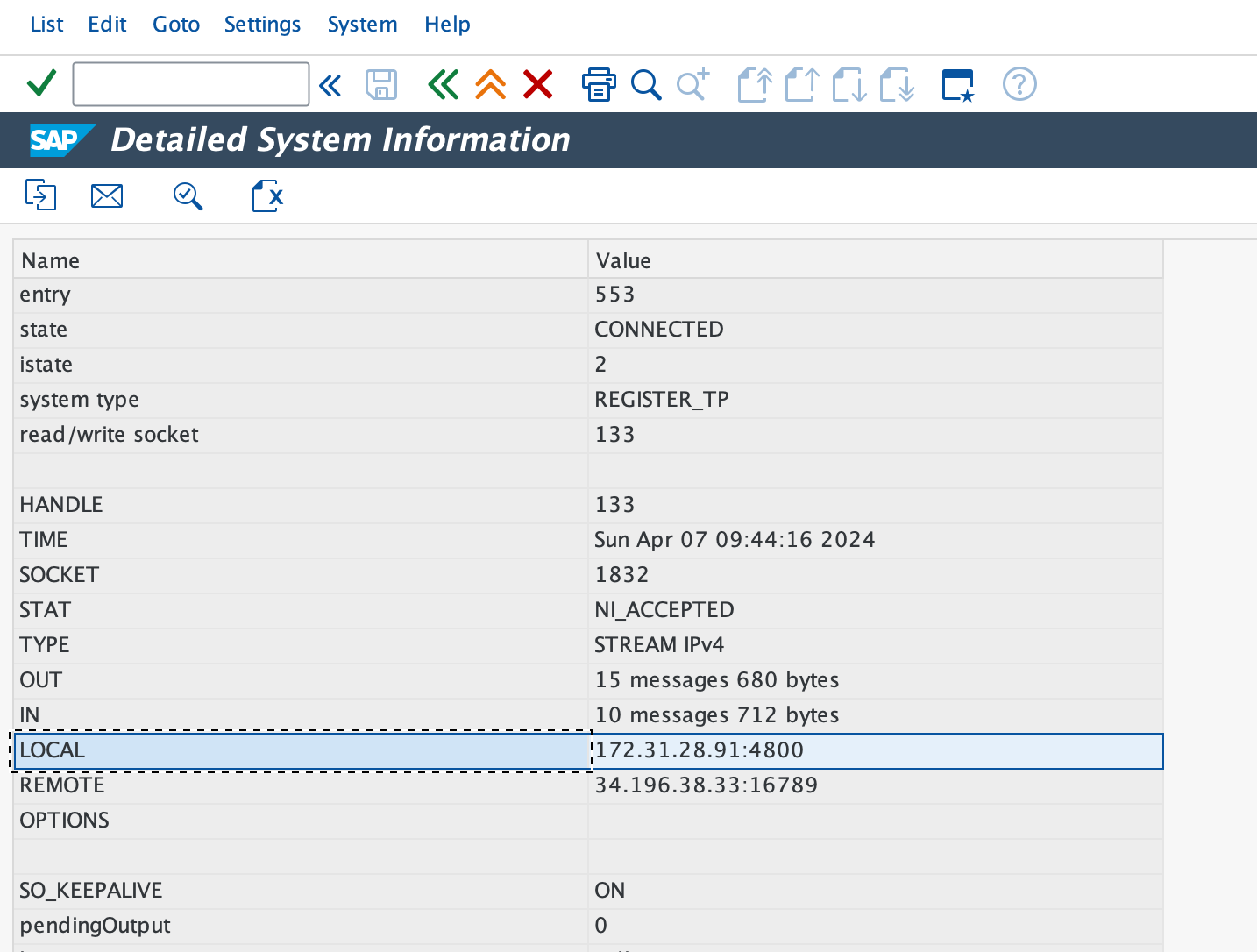
Congratulations! You have set up encrypted connections between your OPA and your SAP system. This enables end-to-end encryption for all communication between SAP and Workato. This can be verified in transaction code SMGW. In the toolbar, navigate to Goto and click Logged on Clients where on double clicking across your connection with the program ID used for the SNC connection, verify the property LOCAL across which you should see port 48XX reflecting secure communication. Refer to the official SAP documentation on ports for validating the secure SNC port range (opens new window).
# Troubleshooting
- When connecting to SAP, you see the following error:
SncPDLInit()==SNCERR_INIT
Unable to load GSS-API Shared Library
named "~/sec/libsapcrypto.so"
Check your config profile in your OPA. Be sure the sapcrypto_library_path parameter has the full path to your libsapcrypto library.
- When connecting to SAP, you see the following error in your OPA logs:
A2200210 Peer certificate verification failed
Check your trust manager configurations under Tcode STRUST. Be sure that your OPA's certificate has been imported and saved in your certificate list.
- When connecting to SAP, you see the following error in your OPA logs:
Could not find a suitable SAP user for the SNC name of the caller
Check that your SECUDIR environment variable has been set. This can be done via echo $SECUDIR. If this is the case, check the SNC name of your user in SAP under Tcode SU01.
Last updated: 5/21/2025, 5:22:32 AM