# MCP authentication
MCP supports API token–based authentication and OAuth2 integration with Workato Identity. Token–based authentication is set by default, but you can switch between authentication methods.
SWITCHING ACCESS METHODS
The MCP token is revoked when you switch from token-based access to Workato Identity. This means that users can no longer access the MCP server with token authentication.
# OAuth2 authentication with Workato Identity
OAuth2 authentication enables you to govern access within Workato Identity. This enables you to control MCP server access centrally without managing separate tokens. OAuth2 authentication with Workato Identity provides your end users with a single sign-on (SSO) experience across MCP clients like Claude, Cursor, and Windsurf.
MCP and Workato Identity integration ensures enterprise-grade security centralized access management.
ALL USERS MUST BE ADDED TO A USER GROUP
You must have admin privileges to grant end-user access to an MCP server. Workspace owners, admins, and collaborators don't automatically have MCP server access. You must add all users, including yourself, to an end-user group to grant MCP access. Refer to Workato Identity end-user groups for more information.
# Use Workato Identity for authentication
Complete the following steps to use Workato Identity for MCP server authentication:
Sign in to your Workato account.
Go to AI Hub and click the MCP Servers tab. A list of your existing MCP servers displays.
Click the MCP server card where you plan to use Workato Identity.
Click User access.
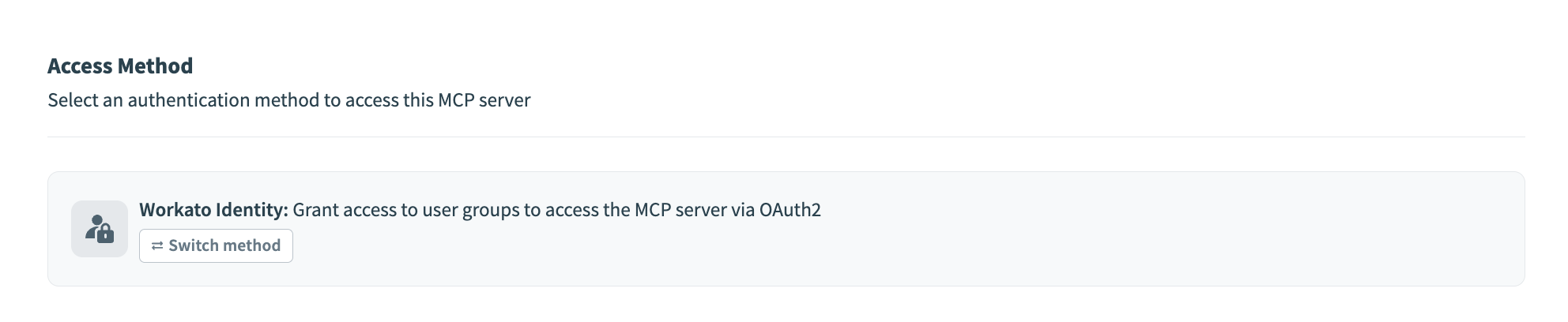
Go to the Access Method section and click the switch method toggle to open the Switch User Access Method modal.
 Access Method section
Access Method section
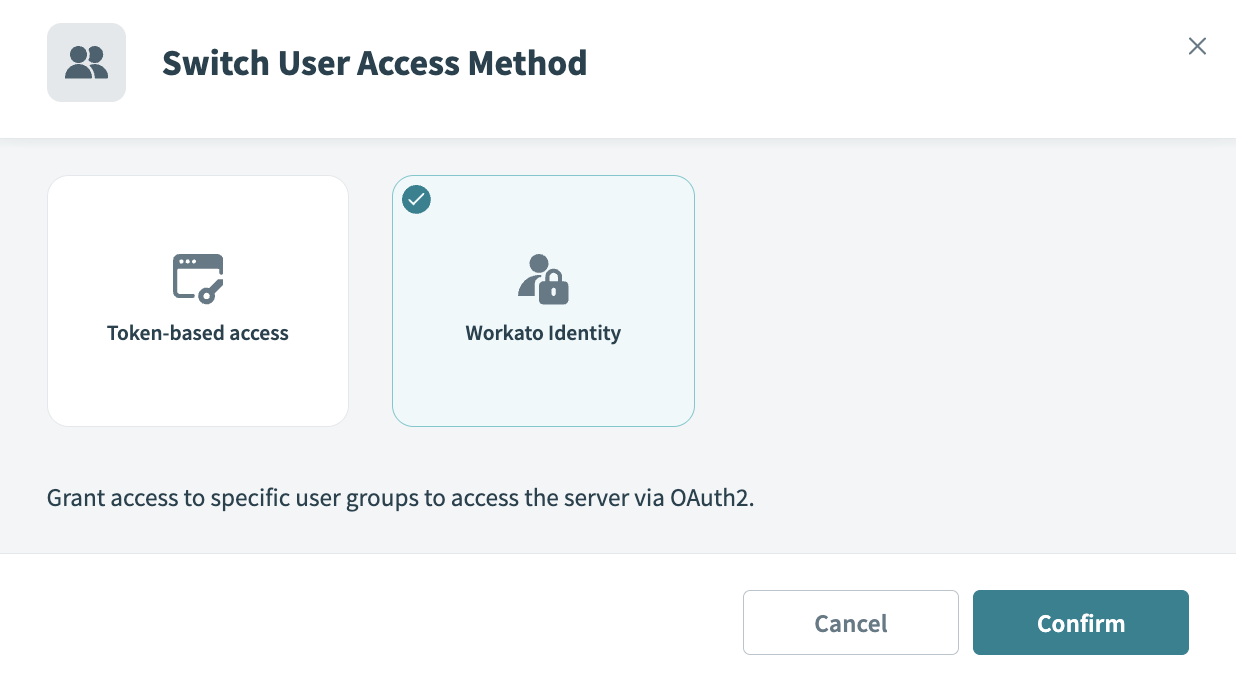
Click Workato Identity.
 Access Method
Access Method
Click Confirm.
# User groups
Use Workato Identity to manage your user groups.
ALL USERS MUST BE ADDED TO A USER GROUP
You must have admin privileges to grant end-user access to an MCP server. Workspace owners, admins, and collaborators don't automatically have MCP server access. You must add all users, including yourself, to an end-user group to grant MCP access.
# User group MCP server access
You can provide access to specific MCP servers after you create a user group with Workato Identity.
Complete the following steps to grant a user group access to an MCP server:
Sign in to your Workato account.
Go to AI Hub > MCP servers and select the MCP server where you plan to add a user group.
Click the User access tab.
Ensure that the access method is set to Workato Identity.
Click Add user groups.
Click Add user groups
Use the User groups drop-down menu to select the user groups you plan to provide with access to the MCP server.
# API token authentication
API token authentication enables you develop and test without SSO configuration. Admins can manage tokens in the MCP server User access page. Token-based access is assigned to MCP servers by default. Tokens are generated automatically when you create a new MCP server with token-based access selected.
# Use token authentication
Complete the following steps to use token authentication:
Sign in to your Workato account.
Go to AI Hub and click the MCP Servers tab. A list of your existing MCP servers displays.
Click the MCP server card where you plan to token authentication.
Click User access.
Ensure that the access method is set to Token-based access.
Go to Developer MCP Token section.
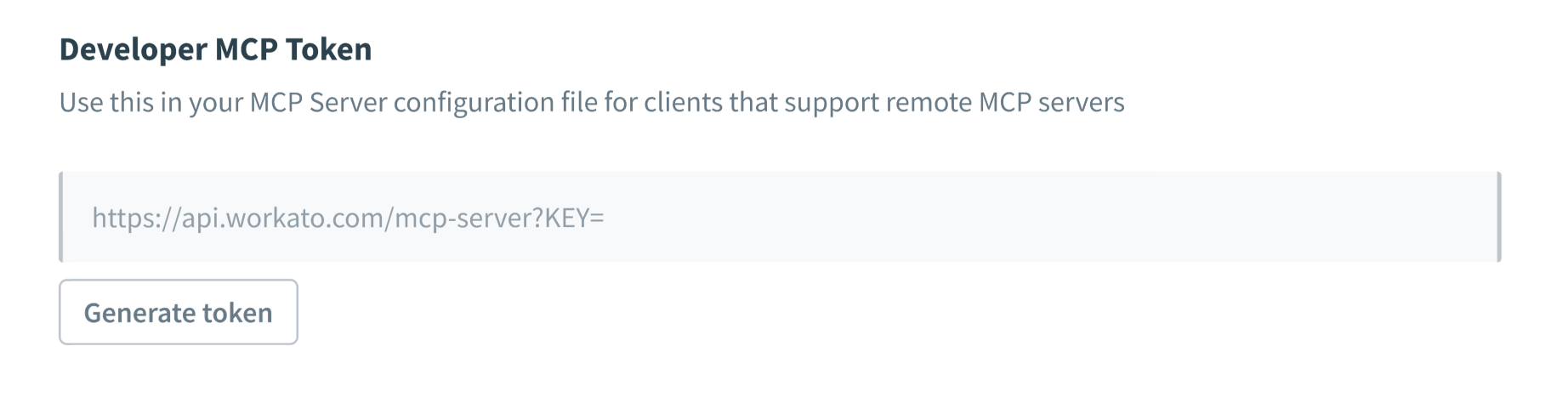 Click Generate token
Click Generate token
Click Copy to copy the generated token.
# Generate and revoke a token
Your existing token is automatically revoked when you generate a new token.
Complete the following steps to generate a new token and revoke an existing token:
Sign in to your Workato account.
Go to AI Hub and click the MCP Servers tab. A list of your existing MCP local servers displays.
Click the MCP server card where you plan to generate and revoke a token.
Click User access.
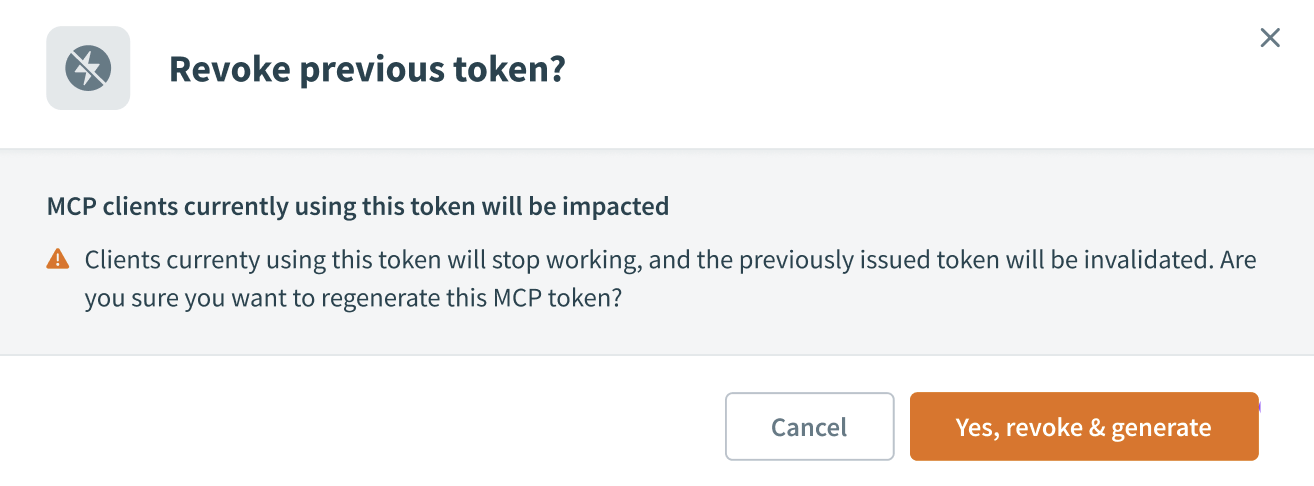
Go to Developer MCP Token and click Re-generate token. The Revoke previous token? modal displays.
Click Yes, revoke & generate. This revokes the existing token and generates a new token.
MCP CLIENT IMPACT
A token becomes invalid when you revoke it. MCP clients using the token lose access to the server and stop working.
 Click Yes, revoke & generate
Click Yes, revoke & generate
Last updated: 8/21/2025, 5:09:19 PM