# GitHub secret scanning
Starting from mid-May 2023, Workato Developer API client tokens are now integrated with GitHub Secret Scanning (opens new window), allowing us to provide additional layers of security when your API tokens are found in plain text on public GitHub repositories.
When these tokens are found, Workato will perform the following steps:
- Revoke your Developer API token to ensure no bad actors can have unauthorized access to your Workato workspace
- Send an email to the workspace admins about the leaked token, including information about where it was found and how to recover from the leaked token
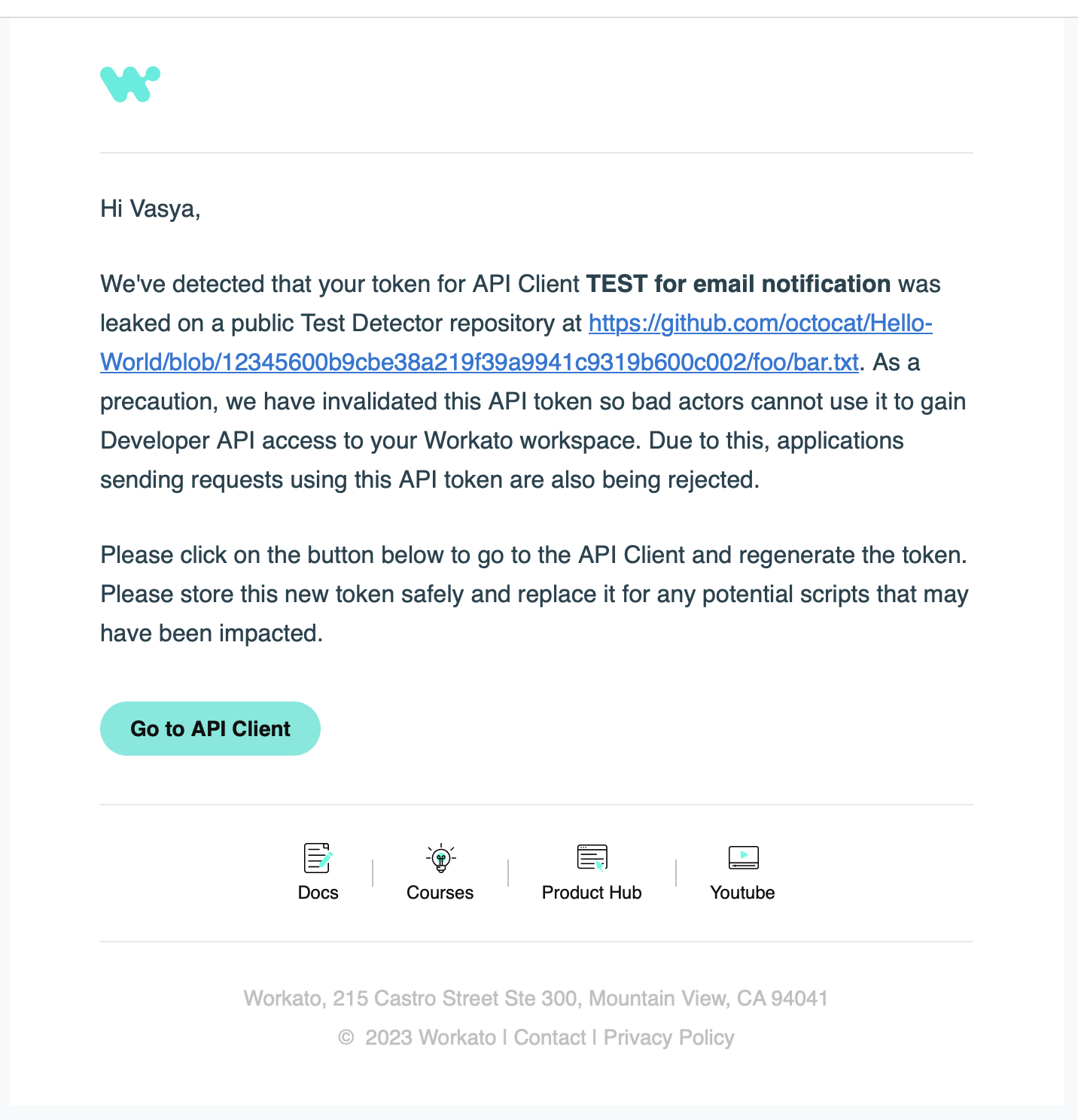 Leaked token email
Leaked token email
TIP
Remember to add your Workspace admins to your email notification lists to ensure that relevant individuals are informed if tokens are leaked. This can be done by going to your Workspace settings (opens new window) when logged in as the workspace admin.
- Mark the API Client as leaked on the Workato UI
- Add an audit log event indicating that the API token was leaked
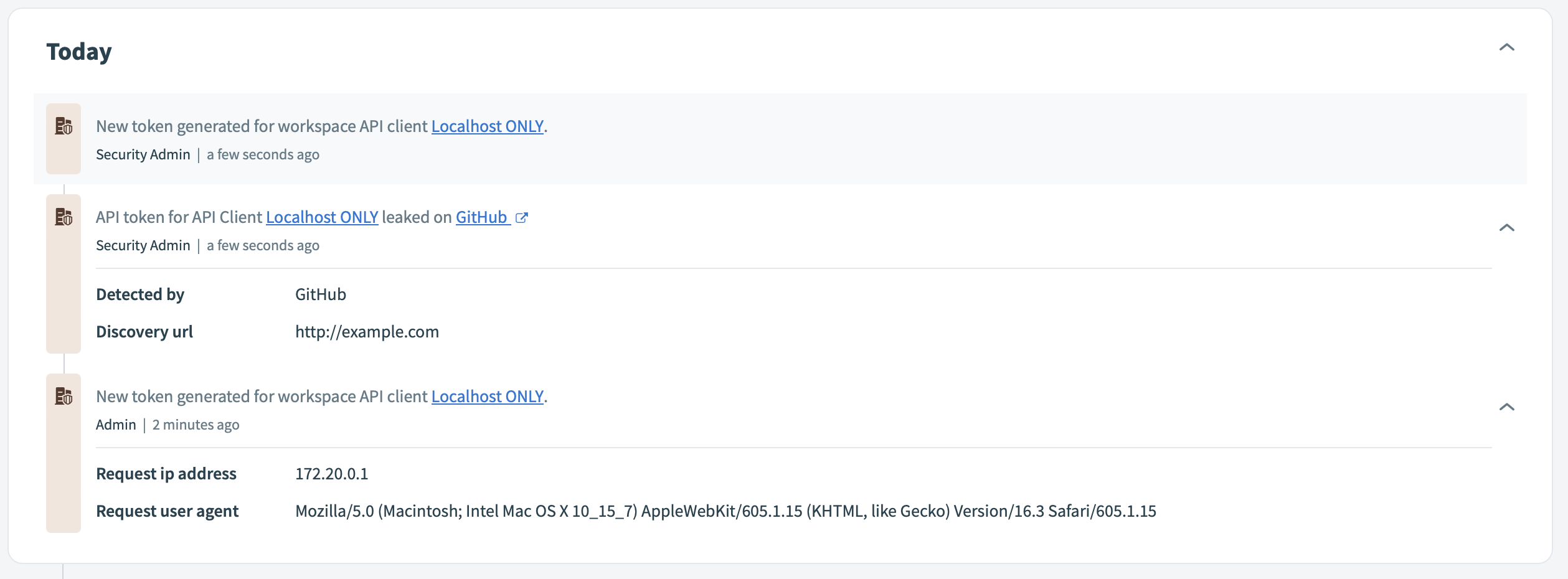 Leaked token audit event
Leaked token audit event
# Why do we revoke tokens immediately?
Human error is one of the most common ways that malicious actors can access your account. We have found that many bad actors use crawlers on GitHub public repositories to find leaked tokens which makes it important that we are able to secure your Workato workspace.
This process is also aligned with many best practices proposed by tools like GitLab (opens new window), Okta (opens new window) and more!
Last updated: 1/14/2026, 4:13:41 PM