# Amazon SNS
Amazon Simple Notification Service (SNS) (opens new window) is a fully managed messaging service for both application-to-application and application-to-person communication. It uses a simplified Pub/Sub paradigm to connect distributed systems, microservices, and node applications.
# API version
The Amazon SNS connector uses the Amazon SNS API (opens new window).
# How to connect to Amazon SNS on Workato
Choose one of the following authentication methods to connect to Amazon SNS:
USE THE AWS IAM ROLE
We recommend using the AWS IAM role.
The AWS IAM role uses temporary credentials making this method secure and not requiring additional management compared to the AWS IAM user which uses permanent credentials that can be leaked and that have to be rotated by the user.
# Connect using an access key authentication
Complete the following steps to create a connection using an IAM user's access key:
Select the project where you plan to store the Amazon SNS connection.
Click Create > Connection.
Search for and select the Amazon SNS connector.
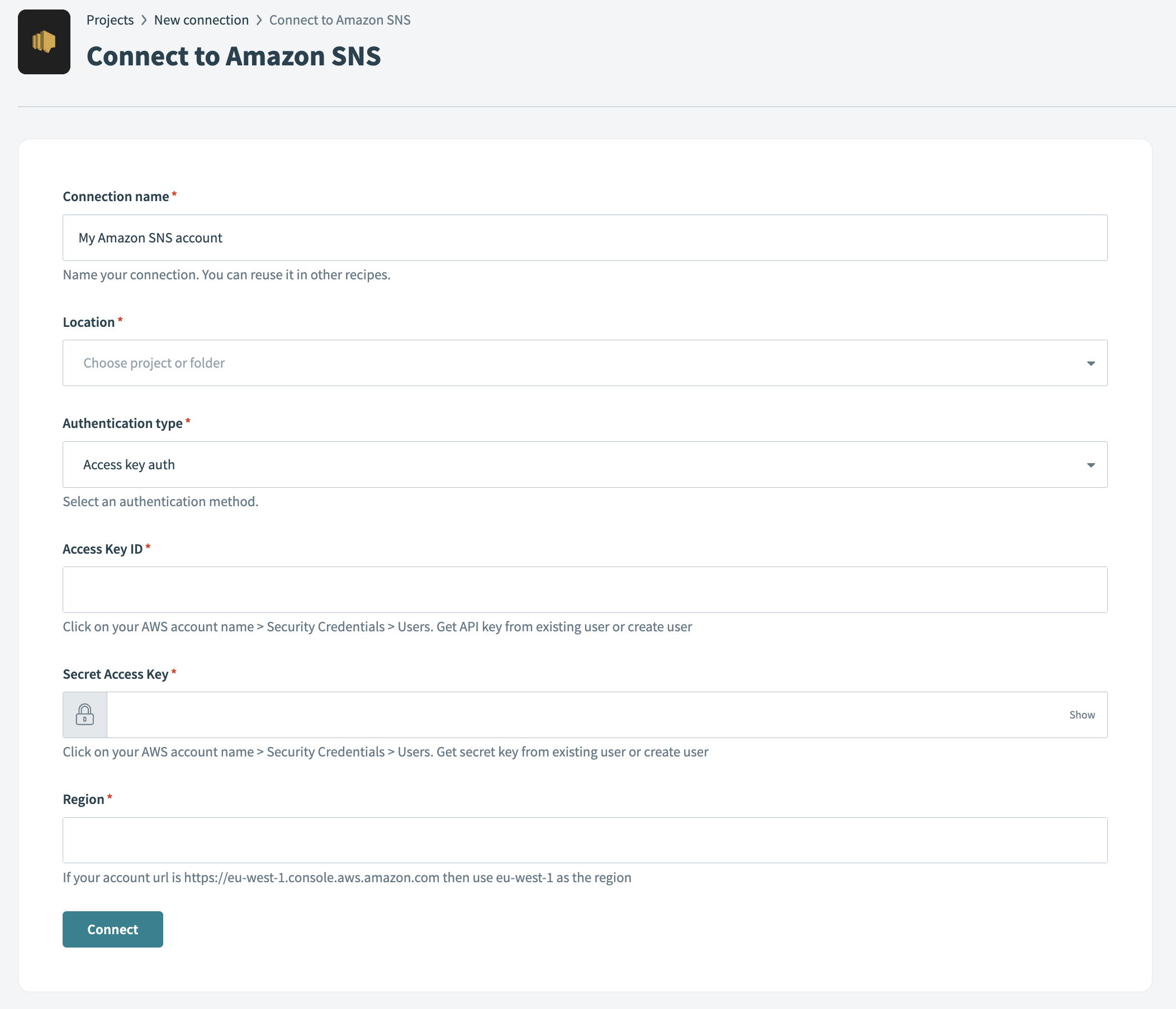
Enter a name for your connection in the Connection name field.
 Amazon SNS connection setup
Amazon SNS connection setup
Use the Location drop-down menu to select the project or folder where you plan to store the connection.
Use the Authentication type drop-down menu to choose Access key auth.
Enter the Access key ID. Go to AWS account name > Security Credentials > Users to retrieve this value. This is the IAM user's access key ID.
Enter the Secret Access Key from the same page.
Enter the Region of the SNS account. For example, if your SNS URL is https://eu-west-1.console.aws.amazon.com, use us-east-1 as the Region.
Click Connect.
# Connect using IAM role authentication
Complete the following steps to create a connection using an AWS IAM role:
Select the project where you plan to store the Amazon SNS connection.
Click Create > Connection.
Search for and select the Amazon SNS connector.
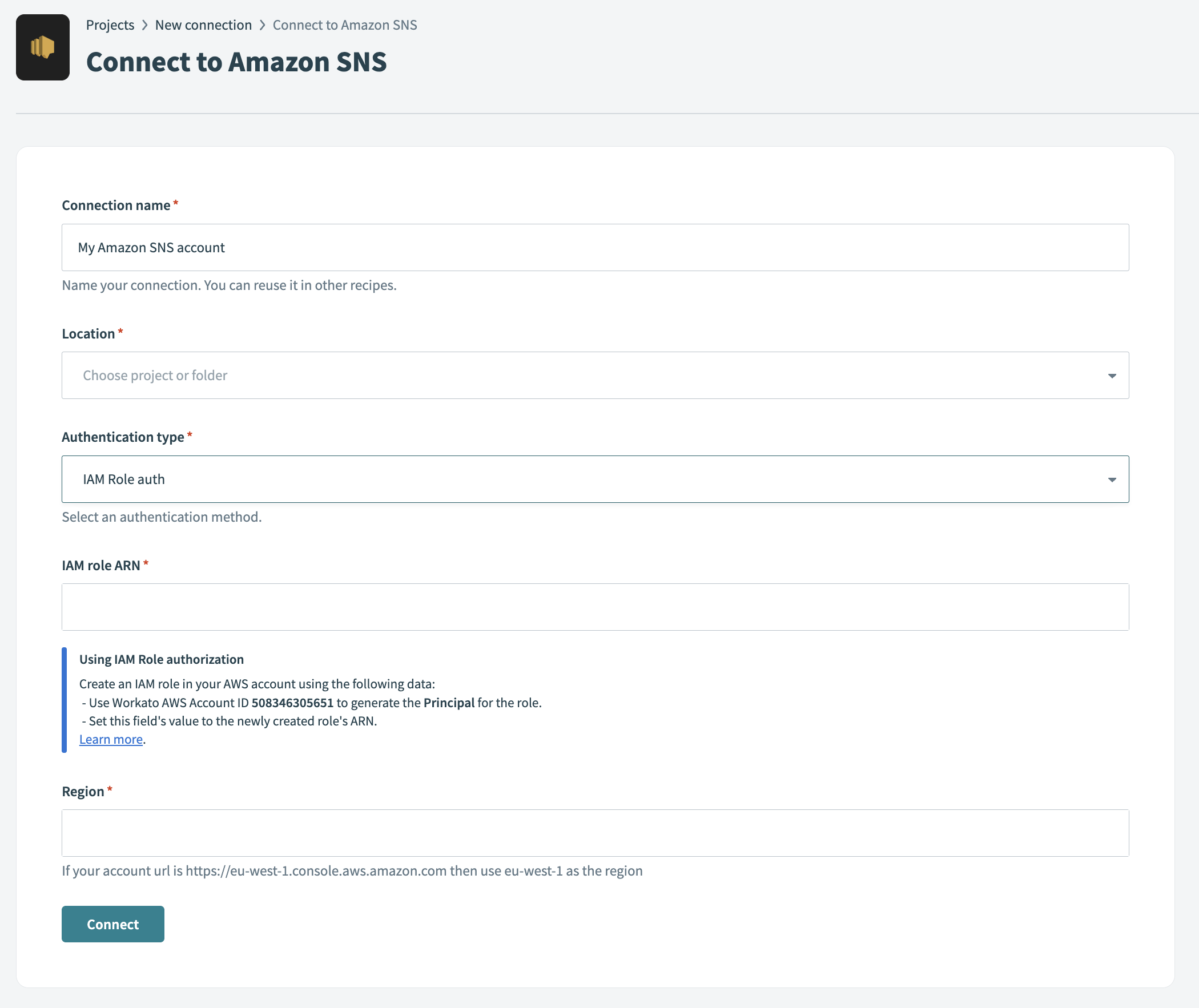
Enter a name for your connection in the Connection name field.
 Amazon SNS connection setup
Amazon SNS connection setup
Use the Location drop-down menu to select the project or folder where you plan to store the connection.
Use the Authentication type drop-down menu to select IAM Role auth.
Enter the IAM role ARN associated with your IAM role. For example, arn:aws:iam::account_id:role/role-name-with-path.
Refer to the IAM Role-based Authentication for AWS Services page for instructions on how to create an IAM role for Workato and retrieve your Amazon resource name (ARN).
Enter the Region associated with your SNS account. For example, if your account URL is https://eu-west-1.console.aws.amazon.com, use us-east-1 as the Region.
Click Connect.
# How to create an integration system role
Create an integration system role to apply consistent permissions and log all operations under a single account. Refer to the Create a role to delegate permissions to an AWS service (opens new window) documentation for more information.
You can also create an integration system user to control permissions independently of the integration system role.
# How to create an integration system user
Complete the following steps to create an integration system user (ISU) and generate access credentials to connect to Workato.
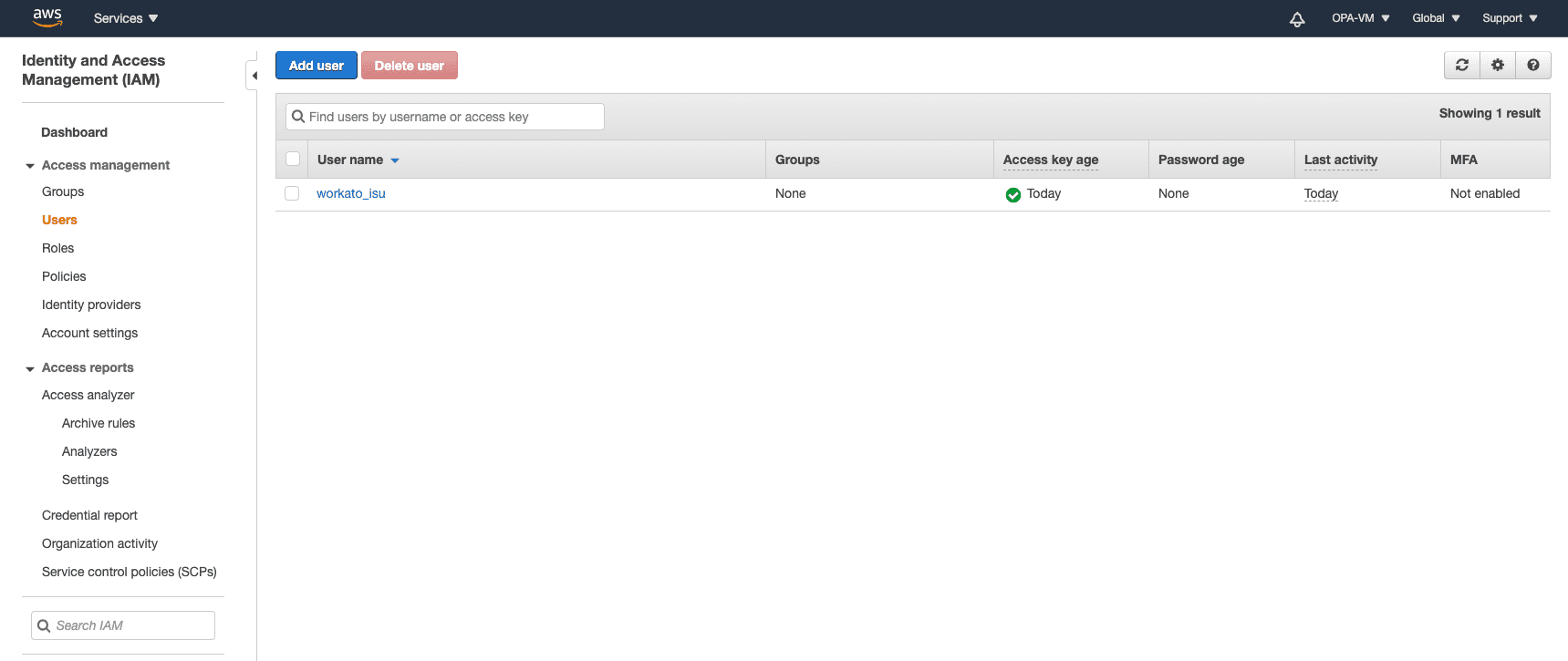
Go to Identity and Access Management (IAM) in your AWS console.
Select Users from the left panel.
Click Add user.
 Create IAM user
Create IAM user
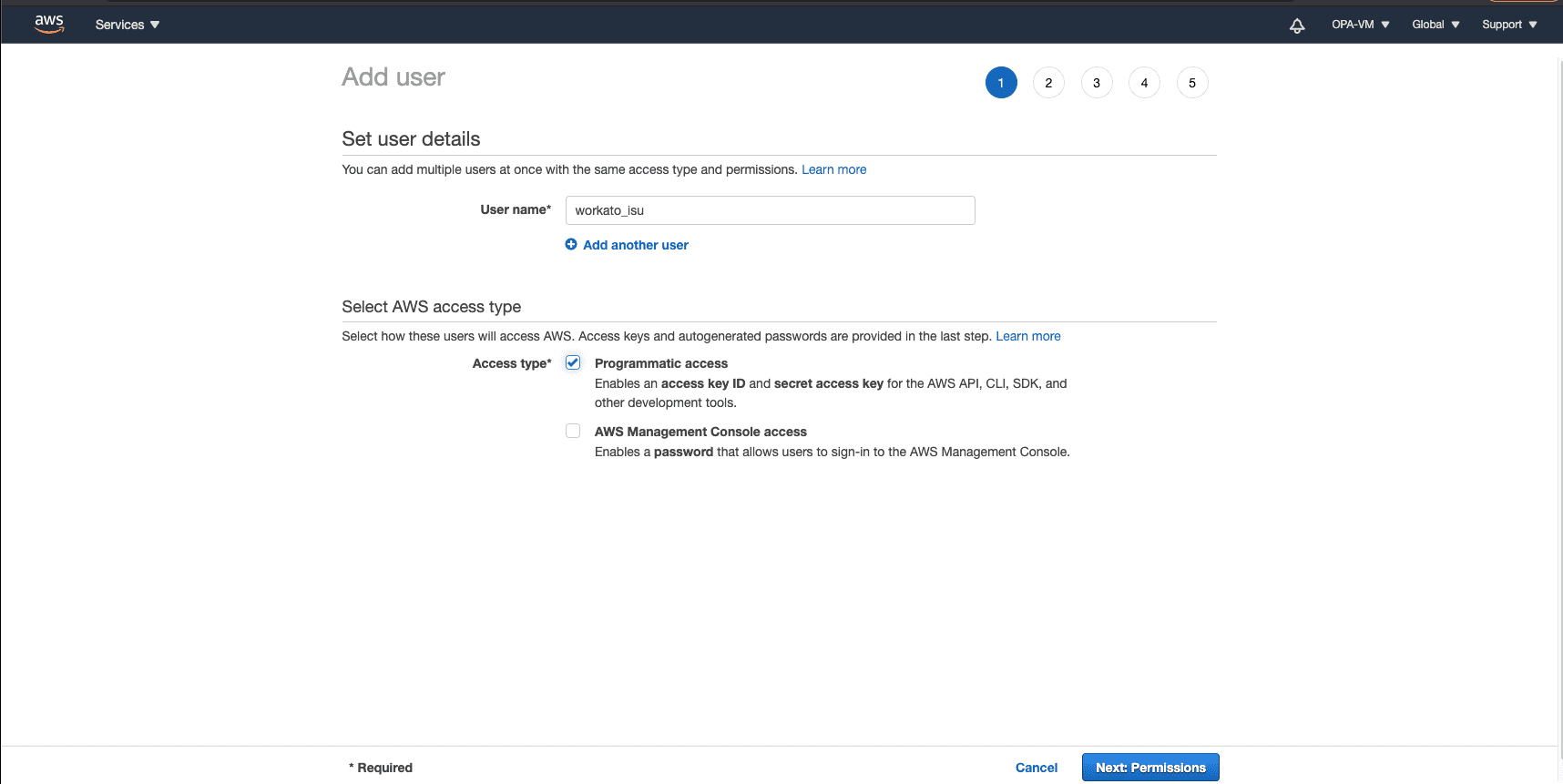
Set the username. Ensure that Programmatic access is selected.
 Set username
Set username
Skip selecting policies in the Add permissions view. You configure permissions and polices in a later step.
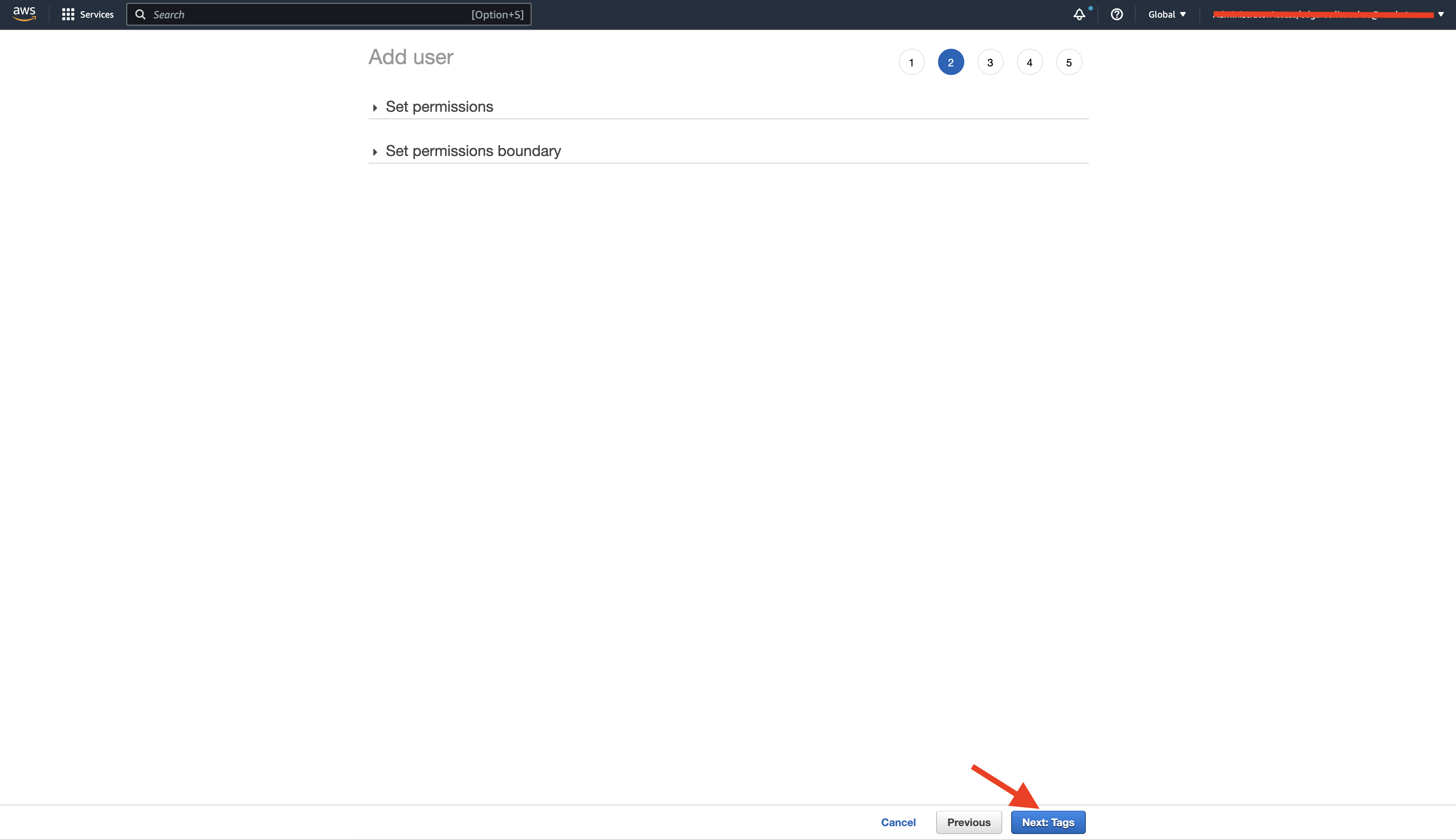 Skip setting permissions
Skip setting permissions
Click Next.
Add Tags. Review the IAM user configuration.
USER HAS NO PERMISSION
You may see a warning that this user has no permissions. This is expected. You will assign permissions in a later step.
Download or copy the Access key ID and Secret access key. Use these credentials to connect to Workato.
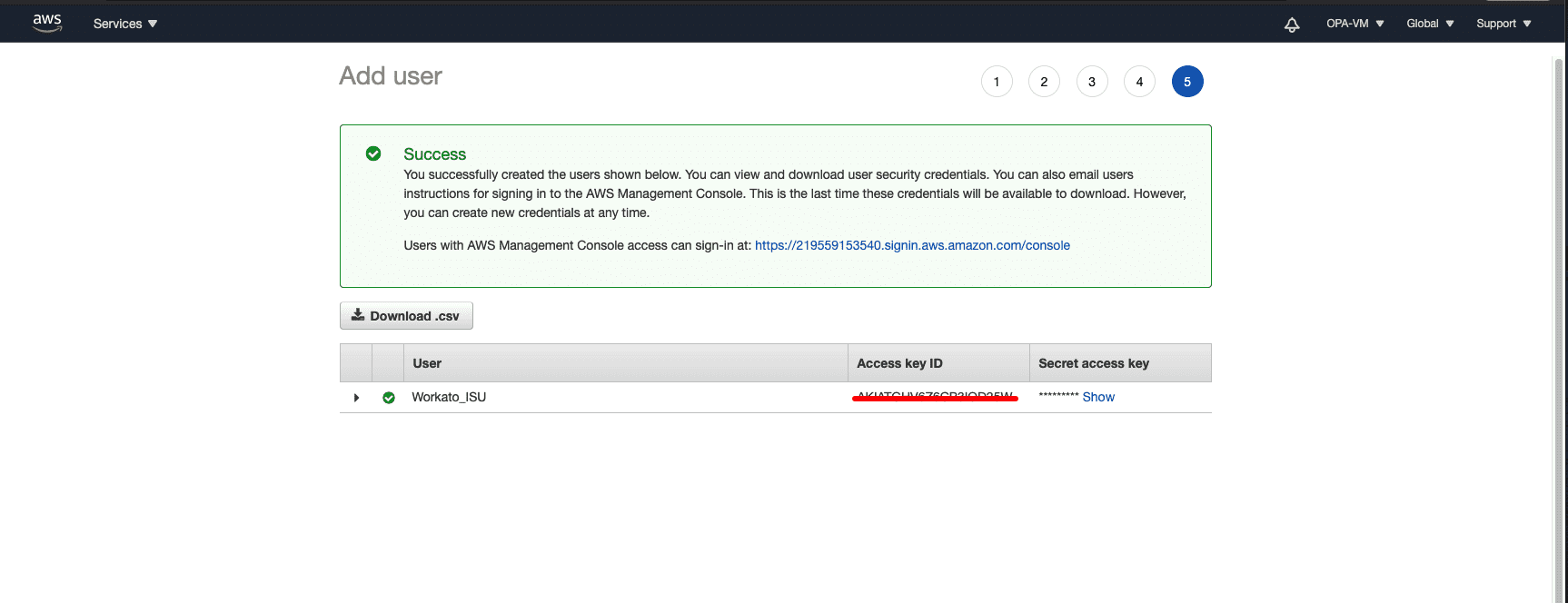 Save access key credentials
Save access key credentials
Return to Identity and Access Management (IAM) in your AWS console.
Select Users from the left panel and select the user that you created.
Click Add inline policy.
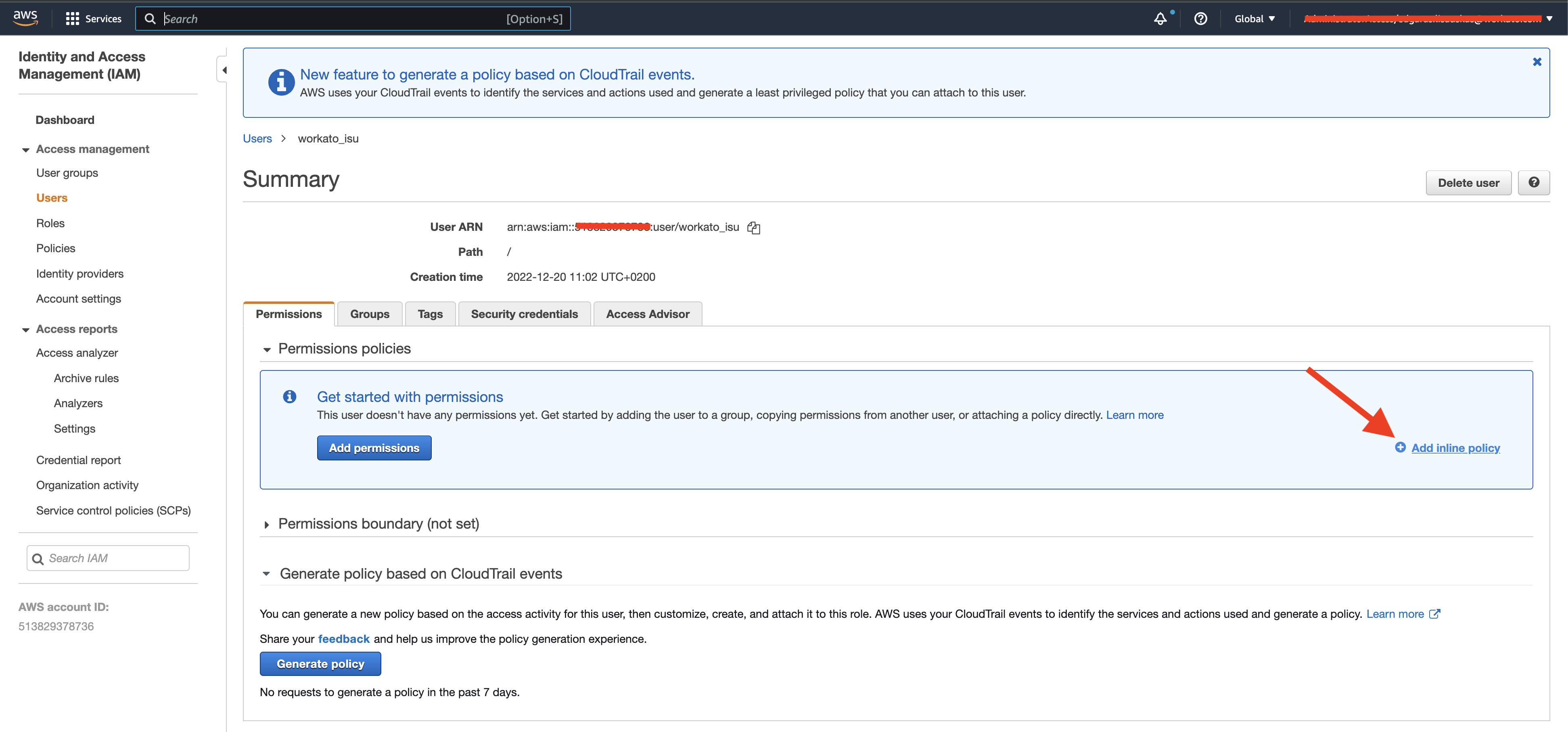 Update IAM user policy
Update IAM user policy
Adding permission for ISU
Select the JSON tab in the Create policy view. Enter the following IAM policy template:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Action": [
"iam:GetUser",
"sns:ListTopics",
"sns:Subscribe",
"sns:Unsubscribe",
"sns:SetSubscriptionAttributes",
"sns:Publish"
],
"Resource": "*"
}
]
}
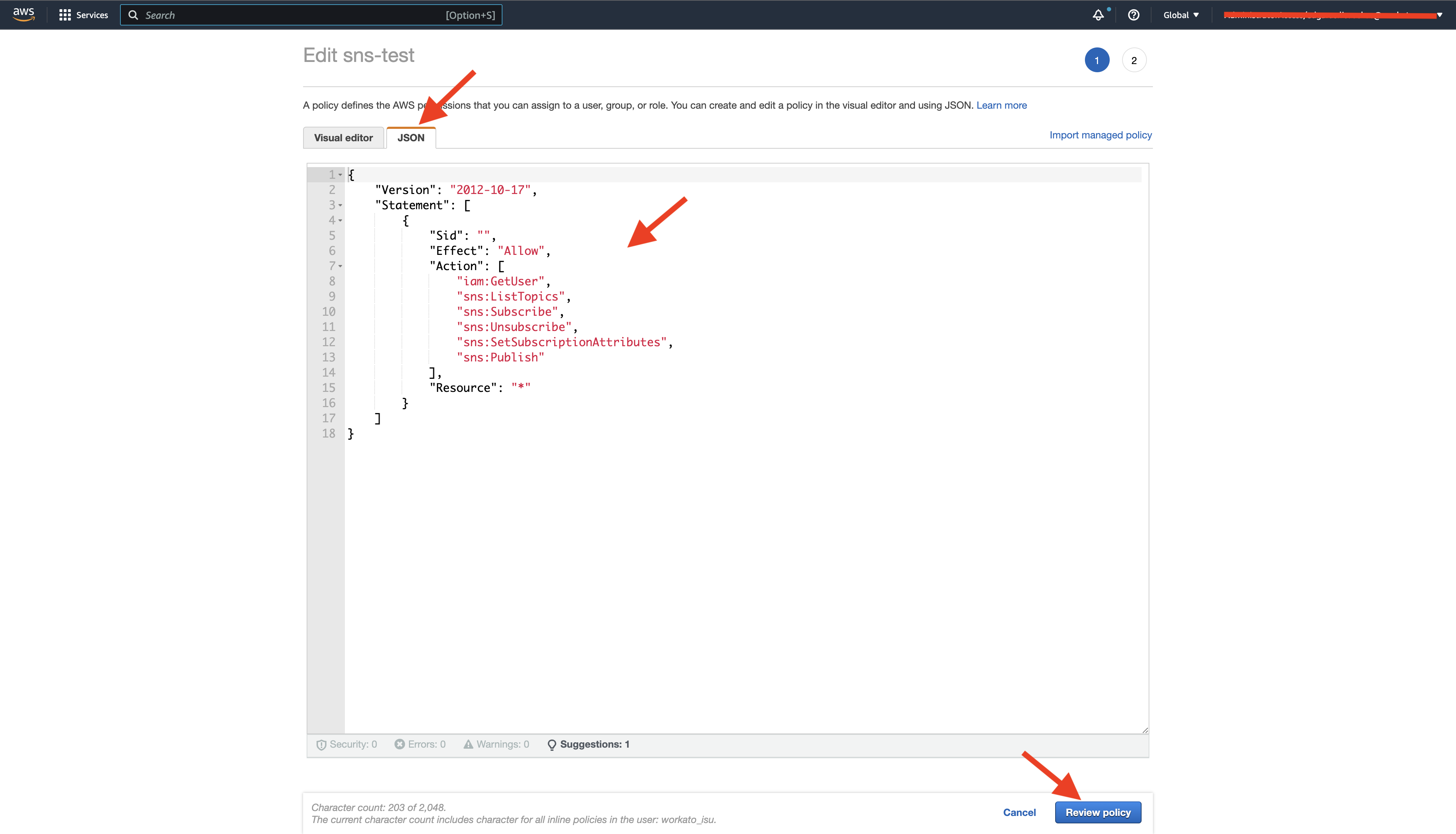 Review IAM user policy
Review IAM user policy
Click Review policy.
Enter a name for the policy in the Review policy view. For example, workato_isu-sns_connector.
Click Create policy. Use the access key credentials you saved earlier to connect to Workato.
 Create policy
Create policy
Last updated: 5/21/2025, 5:22:32 AM