# Azure Monitor
Azure Monitor (opens new window) is a comprehensive monitoring and observability platform for Azure resources. The Azure Monitor connector can send custom logs from your Workato recipes to Azure Monitor Logs for centralized monitoring, troubleshooting, and compliance tracking.
The connector also supports streaming Workato audit logs to Azure Monitor for enhanced visibility into platform activity.
# API version
The Azure Monitor connector uses one of the following APIs, depending on the authentication method:
- Logs Ingestion API (opens new window): Used with client credentials authentication. This is the recommended API for all new integrations.
- HTTP Data Collector API (opens new window): Used with shared key authentication. This API is deprecated and will no longer be functional as of September 2026.
MIGRATION REQUIRED
Microsoft has deprecated the HTTP Data Collector API, which is used by the Send custom log action with shared key authentication. Both the action and authentication method will be deprecated on December 8, 2025. Subsequently, the API will stop working in September 2026.
We recommend that you migrate to the new Inject custom logs action with client credentials authentication. This action uses the Logs Ingestion API.
# Prerequisites
Ensure you have the following before connecting to Azure Monitor:
- An active Azure subscription
- A Log Analytics workspace (opens new window)
- Appropriate permissions to create app registrations in the Azure portal
# How to connect to Azure Monitor
MICROSOFT MFA ENFORCEMENT
Microsoft is rolling out mandatory multi-factor authentication (MFA) (opens new window) gradually to different applications and accounts in phases. This enforcement will continue throughout 2025 and beyond.
We strongly recommend enabling MFA now for all Microsoft accounts used with Workato to avoid service disruptions from short-notice enforcement changes.
Complete the following steps to maintain uninterrupted service:
Enable MFA for your Microsoft organization following Microsoft's MFA setup guide (opens new window).
Reconnect your Microsoft connection in Workato.
Complete the OAuth flow with MFA when prompted.
Test your recipes to ensure they work with the updated connection.
The Azure Monitor connector supports the following authentication methods:
# Client credentials
This method uses the Azure Monitor Logs Ingestion API (opens new window) and requires the following:
- Tenant ID
- Client ID
- Client secret
- Data collection endpoint
# Register the Workato app in the Azure Portal
Complete the following steps to register the Workato app and obtain a tenant ID, client ID, and client secret for client credentials grant connections.
Register the Workato app in the Azure Portal
Sign in to the Azure portal (opens new window).
Select App registrations > + New registration, under Azure services.
Enter a unique name for the application and select a Supported account type.
Select Web from the Select a platform drop-down menu.
Enter https://www.workato.com/oauth/callback as the Redirect URI and select Register.
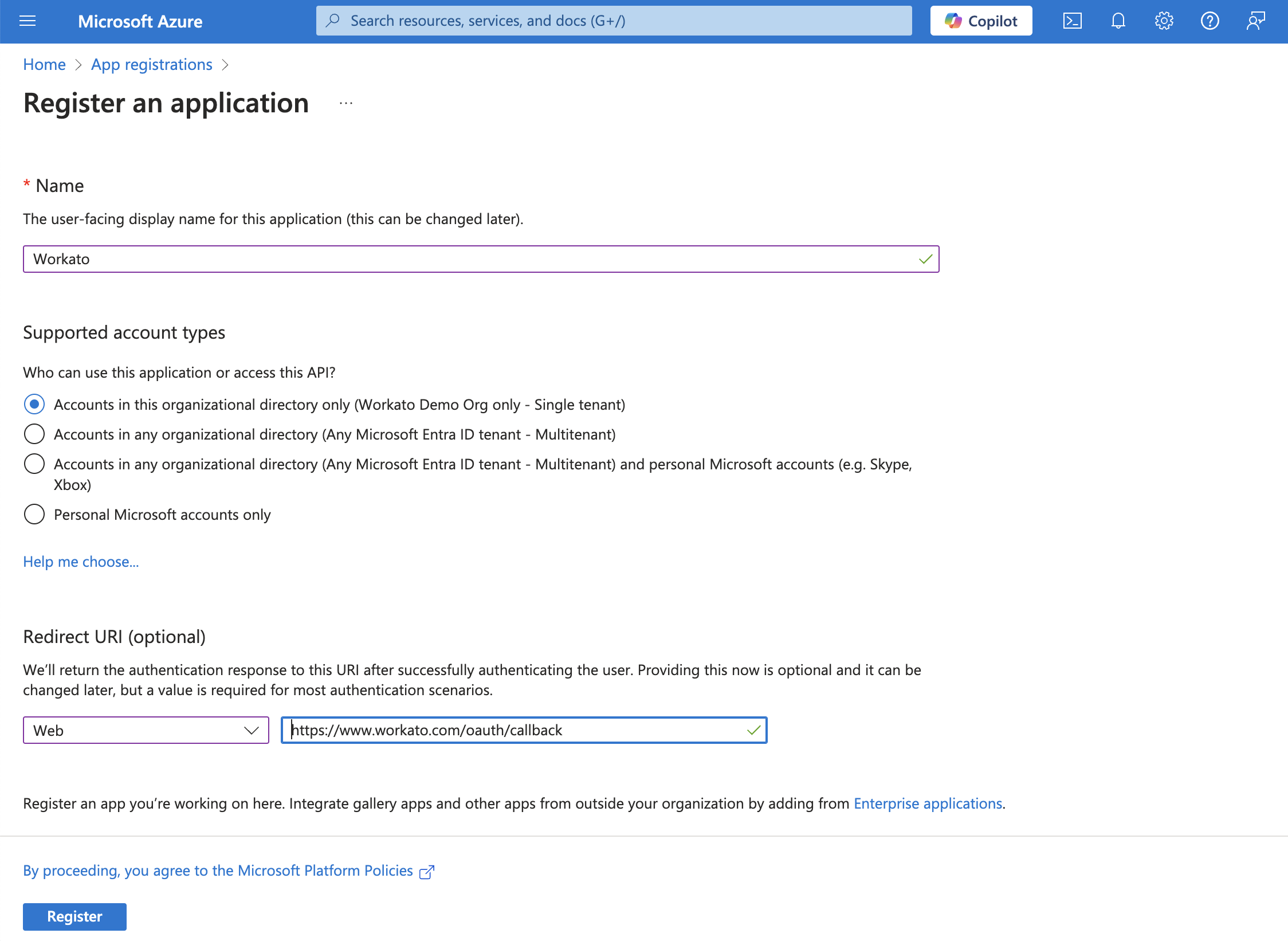 Register an app
Register an app
Generate a client secret
Go to Manage > Certificates & Secrets > Client secrets.
Click + New client secret.
Provide a Description for the client secret and specify an expiry date.
Click Add.
Copy and save the client secret Value—not the Secret ID—for use in Workato.
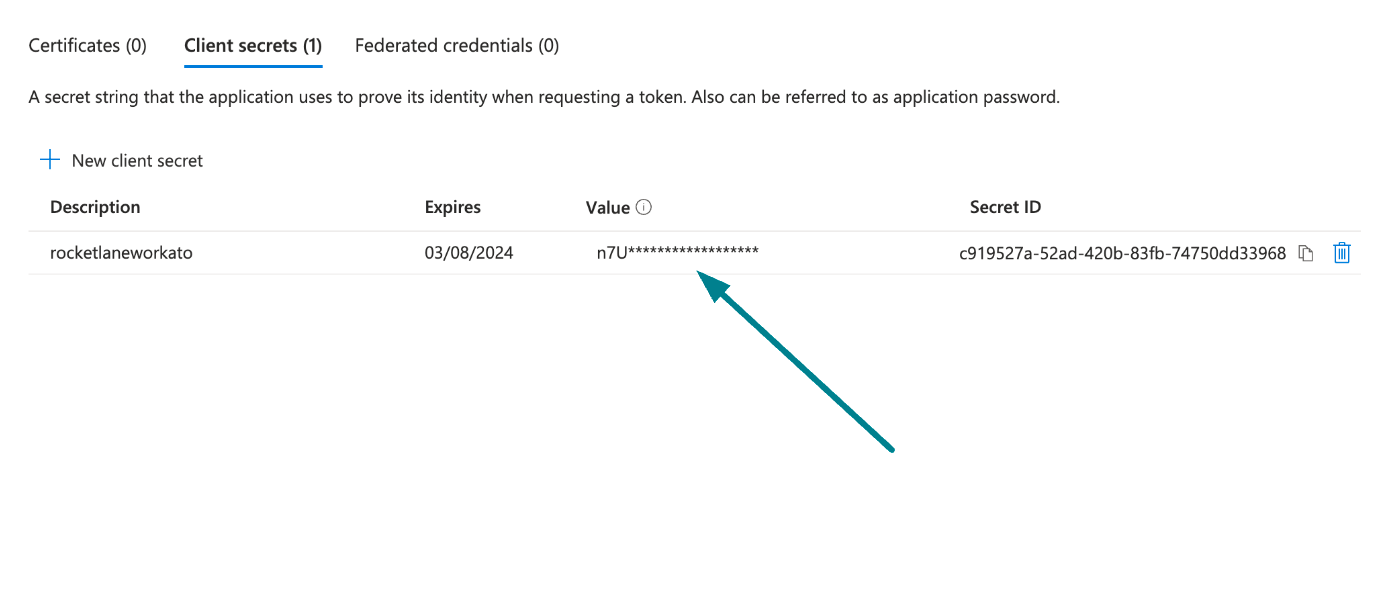 Copy and save the client secret value
Copy and save the client secret value
Obtain the Application (client) ID and Directory (tenant) ID from the Azure Portal
Go to the Overview > Essentials section.
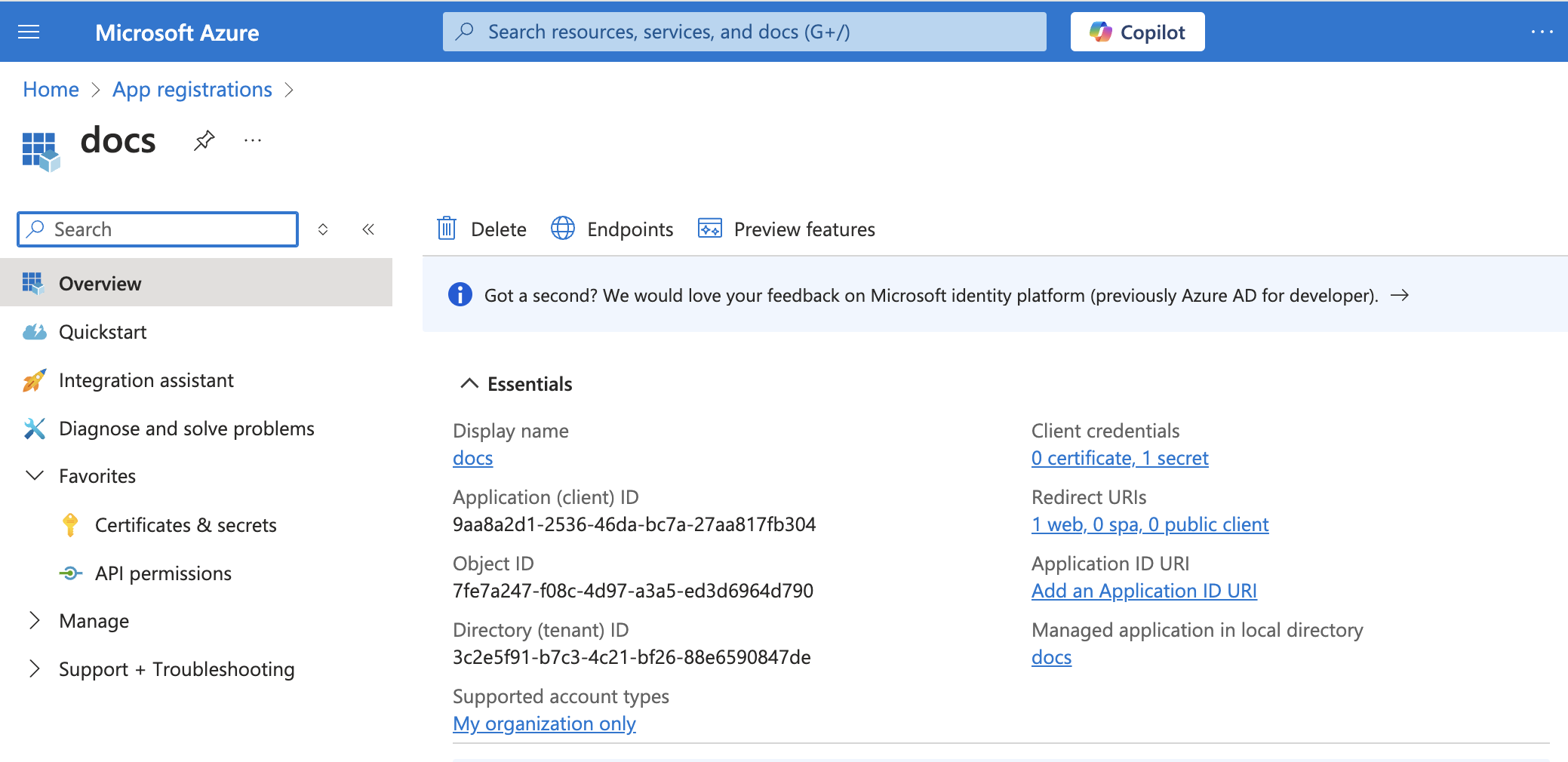 App details
App details
Copy the Application (client) ID and the Directory (tenant) ID for use in Workato.
Create a data collection endpoint and obtain the Logs Ingestion URL
Go to Monitor and select Data Collection Endpoints from the Settings section.
Click Create to create a new data collection endpoint.
Enter a Name for the data collection endpoint.
Select the Subscription and Resource group from the drop-down menus.
Select the Region. Choose a region that matches your Log Analytics workspace location for optimal performance.
Click Review + create.
Review the settings and click Create.
After the deployment completes, open the data collection endpoint you created.
Copy the Logs Ingestion URL for use in Workato.
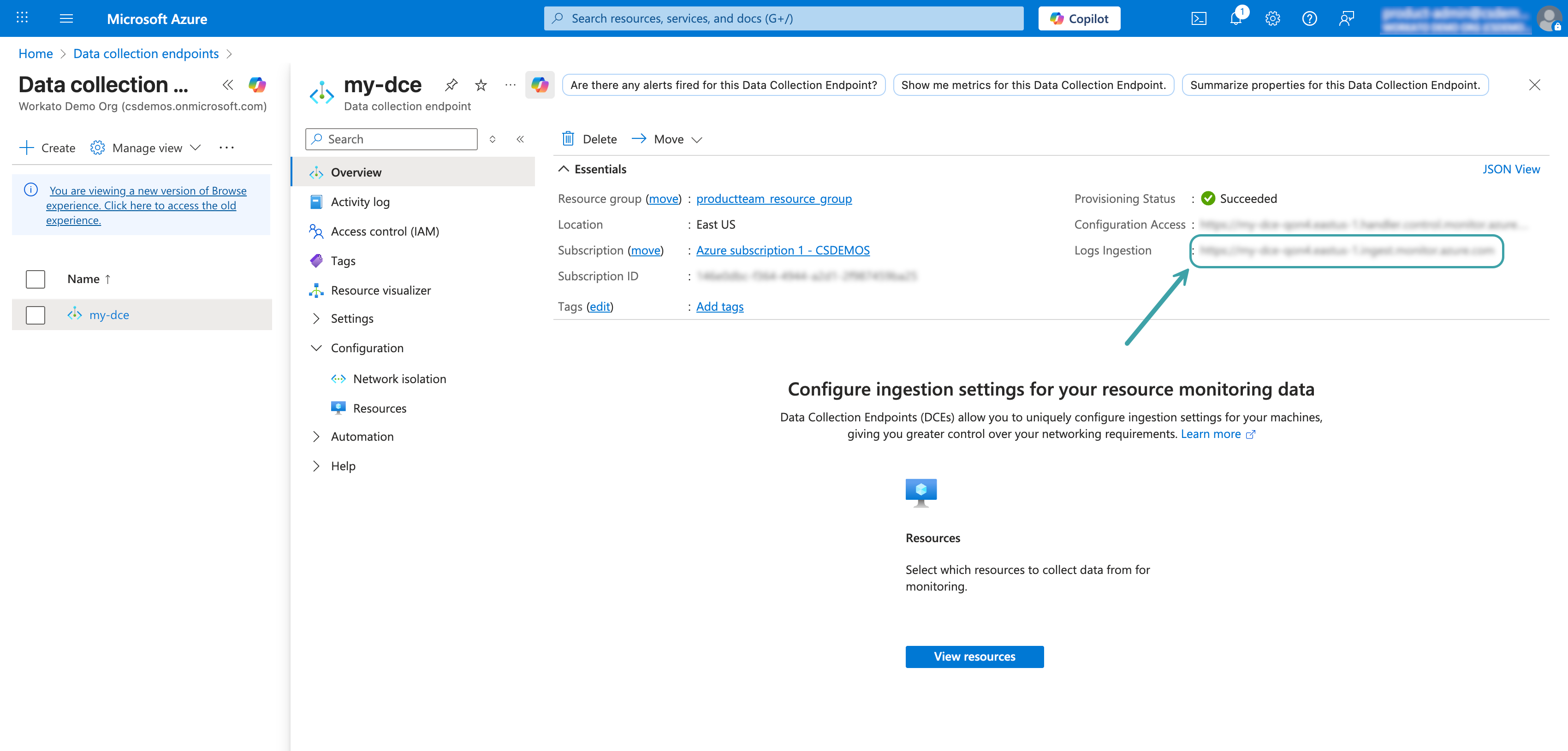 Copy the Logs Ingestion URL
Copy the Logs Ingestion URL
Refer to the Microsoft Data collection endpoints documentation (opens new window) for more information.
Create a data collection rule and assign permissions
A data collection rule defines how data is collected and where it is sent. These steps outline how to create a custom table, configure the data collection rule, and grant your app registration the required permissions.
Go to your Log Analytics workspace in the Azure portal.
Select Tables from the Settings section.
Click Create > New custom log (DCR-based).
Enter a Table name for your custom table. Note that Azure automatically appends _CL (custom log) to your table name. For example, if you enter WorkatoLogs, the full table name is WorkatoLogs_CL.
Click Create a new data collection rule.
Enter a Data collection rule name.
Select the Subscription and Resource group from the drop-down menus.
Select the data collection endpoint you created in the previous step from the Data collection endpoint drop-down menu.
Click Next to define the schema for your custom table.
Define the schema by adding columns for your log data. Refer to the Microsoft custom tables documentation (opens new window) for more information.
Click Next and review your settings.
Click Create to create the custom table and data collection rule.
Go to Monitor and select Settings > Data Collection Rules.
Select the data collection rule you created.
Copy the Immutable Id (also called DCR ID) for use in Workato. This value is required to configure the Inject custom logs action.
Click Configuration > Data sources in the left menu and note the Data source name (for example, Custom-WorkatoLogs_CL). This is the stream name, and is required for the Inject custom logs action in Workato.
Assign permissions to your app registration. In the data collection rule, click Access control (IAM) in the left menu.
Click Add > Add role assignment.
Select Monitoring Metrics Publisher role and click Next.
Click Select members and search for the app registration you created earlier.
Select your app registration and click Select.
Click Review + assign to complete the role assignment.
Refer to the Microsoft Data collection rules documentation (opens new window) for more information.
Return to Workato to complete the connection setup.
# Complete setup in Workato
Complete the following steps to establish an Azure Monitor connection using client credentials authentication:
Click Create > Connection.
Search for and select Azure Monitor on the New connection page.
Enter a name for your connection in the Connection name field.
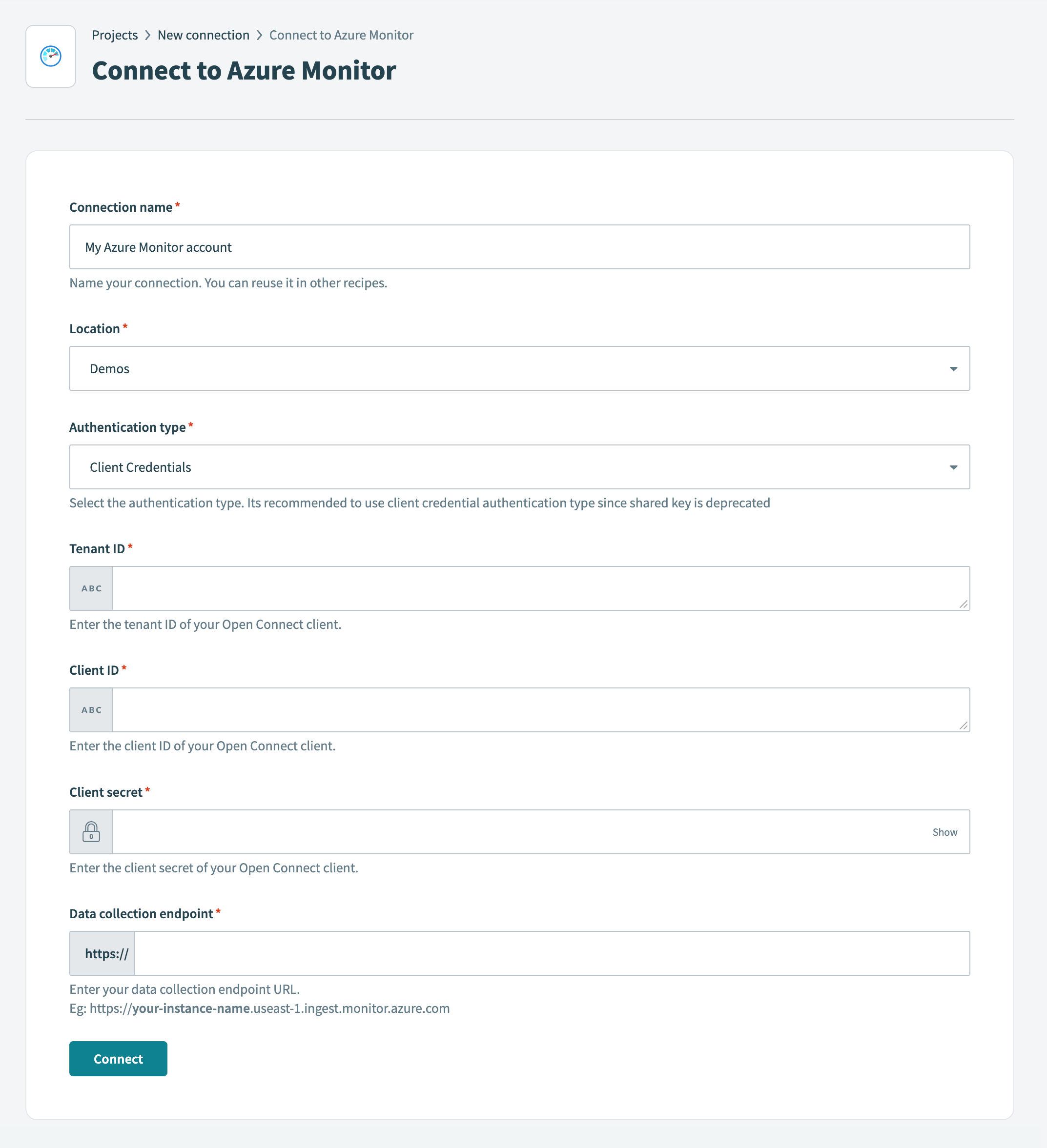 Connect to Azure Monitor
Connect to Azure Monitor
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Authentication type drop-down menu to select Client Credentials.
Enter the tenant ID from your Azure app registration in the Tenant ID field.
Enter the client ID from your Azure app registration in the Client ID field.
Enter the client secret from your Azure app registration in the Client secret field.
Enter your data collection endpoint URL in the Data collection endpoint field. For example, https://YOUR-INSTANCE-NAME.eastus-1.ingest.monitor.azure.com. This is labeled as the Logs Ingestion value in the Azure portal.
Click Connect.
# Shared key
DEPRECATED - MIGRATION REQUIRED
This authentication method uses the legacy HTTP Data Collector API (opens new window), which is deprecated and will stop working in September 2026. Migrate to client credentials authentication instead.
This method requires the following values:
- Workspace ID
- Shared key
# Retrieve your workspace ID and shared key
Complete the following steps to retrieve your workspace ID and shared key:
Go to the log analytics workspace where you plan to send logs.
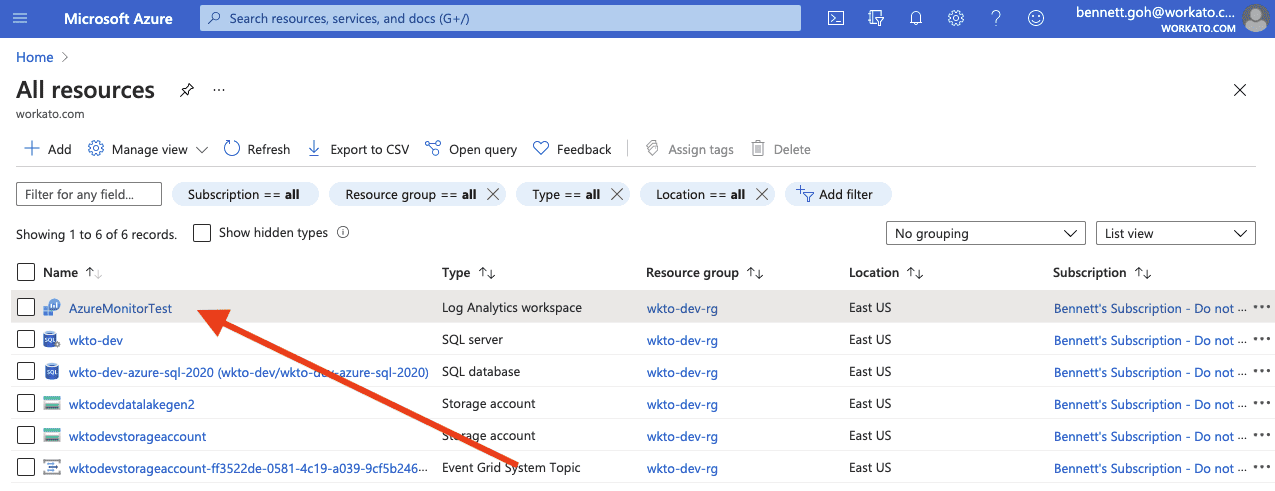
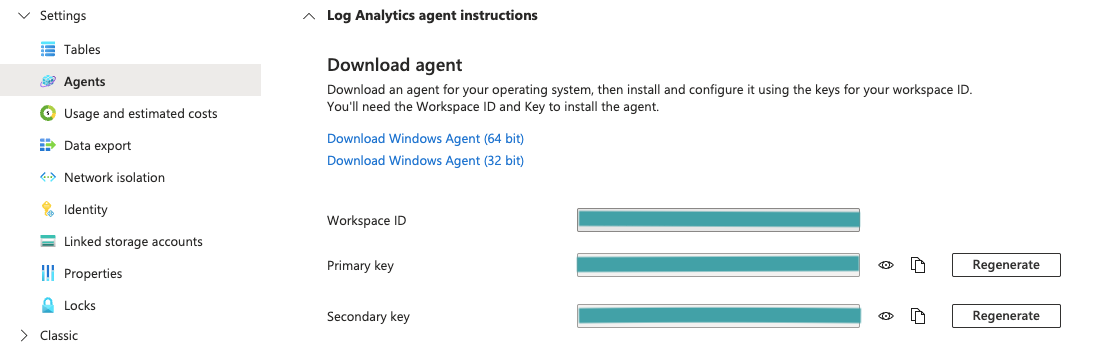
Click Settings > Agents.
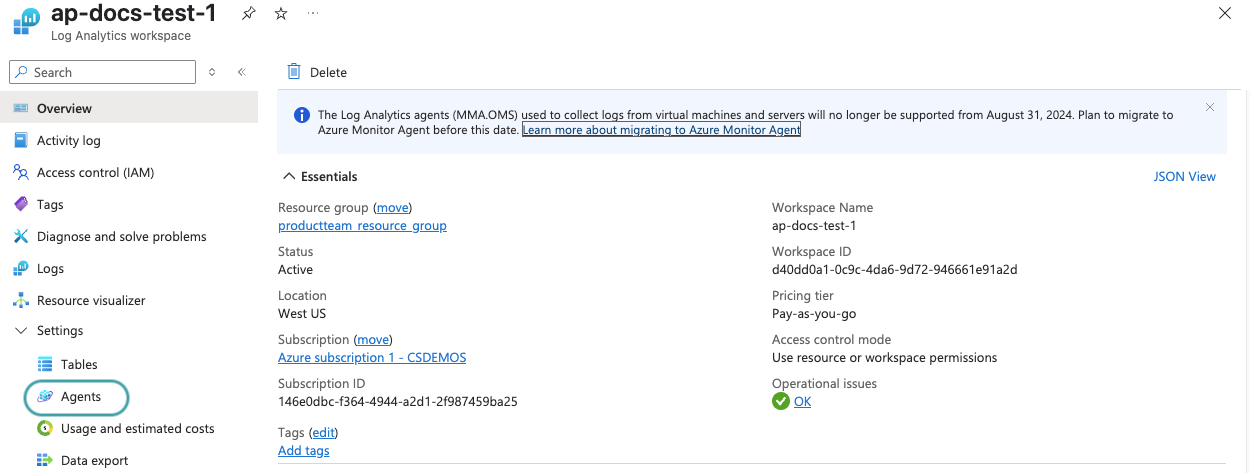
Expand the Log Analytics agent instructions section.
Locate your workspace ID under Log Analytics agent instructions. The workspace ID is the ID of your log analytics workspace.
Locate your shared key under Log Analytics agent instructions. You may use your primary or secondary key as your shared key.
# Complete setup in Workato
Complete the following steps to establish an Azure Monitor connection using shared key authentication:
Click Create > Connection.
Search for and select Azure Monitor on the New connection page.
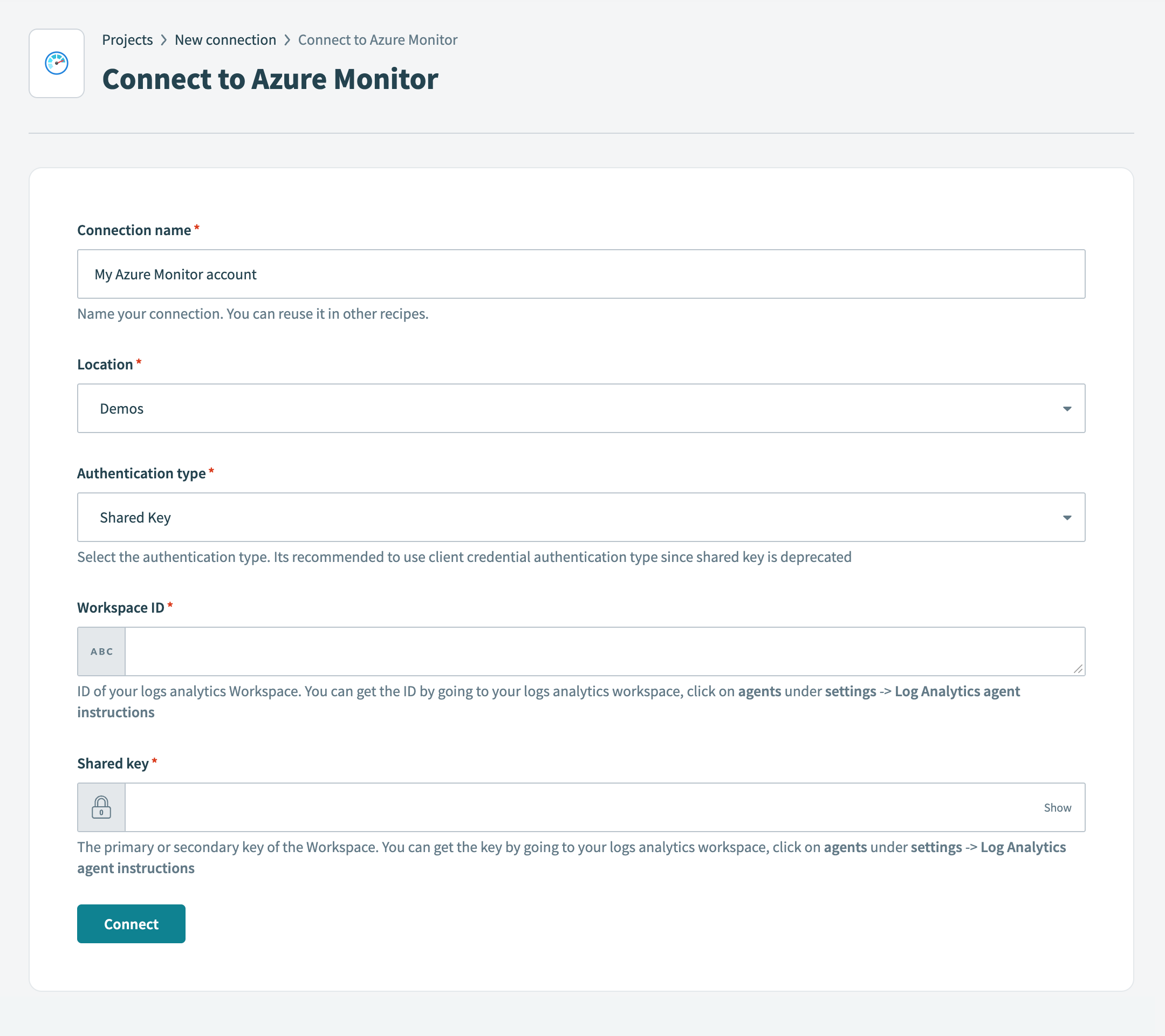
Enter a name for your connection in the Connection name field.
 Connect to Azure Monitor
Connect to Azure Monitor
Use the Location drop-down menu to select the project where you plan to store the connection.
Use the Authentication type drop-down menu to select Shared Key.
Enter the Workspace ID.
Enter the Shared key.
Click Connect.
Last updated: 10/17/2025, 3:04:55 PM