# HTTP SSL certificate verify failed
The Certificate verify failed error occurs when you attempt to connect to the HTTP connector in Workato without a valid certificate.
Workato::Adapters::OnException::Exception: SSL_connect returned=1 errno=0 state=error: certificate verify failed
This error may occur for the following reasons:
- Certificate is self-signed: The certificate wasn't issued by a trusted certificate authority.
- Certificate chain is incomplete: The target server doesn't return all intermediate certificates required for validation.
- Certificate is invalid or mismatched: The certificate is expired or doesn't match the expected domain.
# How the HTTP connector handles certificate errors
The HTTP connector returns a certificate verification error when it can't validate the server's SSL certificate. This occurs when the certificate is self-signed, expired, or missing a complete trust chain.
Most SSL clients, including browsers, Postman, and Workato, reject self-signed or incomplete certificates by default. You must upload the full certificate chain during connection setup to establish trust.
The connector accepts a self-signed certificate only if the full certificate chain is uploaded. If the certificate is expired or doesn't match the server domain, the connector still rejects the connection. You must replace the certificate in these cases to restore secure communication.
# How to troubleshoot
You can download the certificate chain from the target server and upload it to the HTTP connection configuration to establish trust with a self-signed certificate. This lets Workato validate the SSL handshake even when the certificate isn't signed by a public authority.
# Download the certificate chain
Complete the following steps to export the certificate chain from the target server:
Open a browser like Firefox and go to a secure page that uses a self-signed SSL certificate. For example: https://self-signed.badssl.com/.
Click Advanced… > View Certificate to display the certificate details.
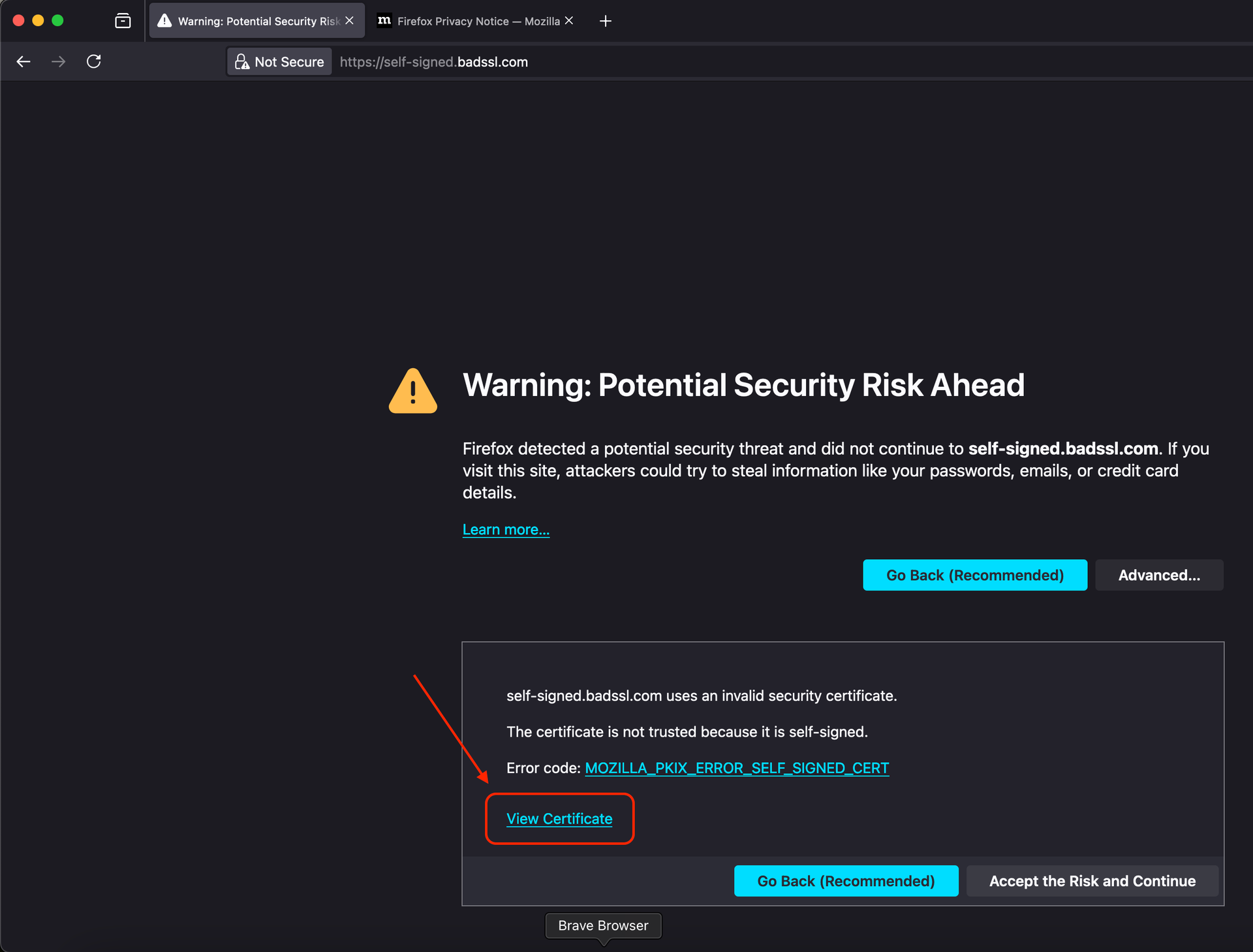 Obtain the certificates
Obtain the certificates
Click PEM (chain) to download the full certificate chain as a .pem file.
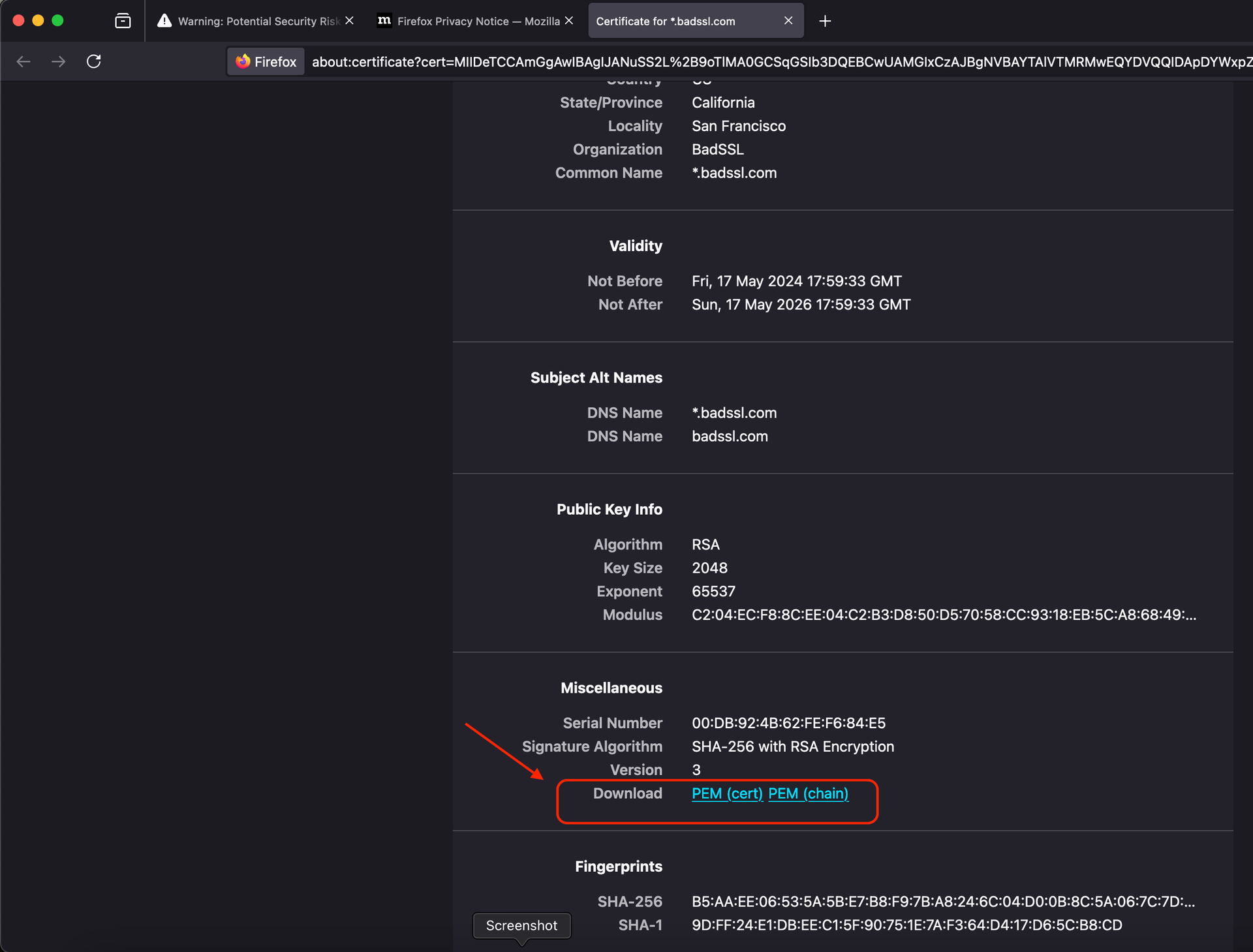 Download the certificate chain
Download the certificate chain
WHY THE FULL CERTIFICATE CHAIN MATTERS
A certificate chain contains multiple certificates, such as the server certificate, intermediate certificates, and the root certificate. Each certificate must validate the preceding one to establish trust.
Workato can't verify the target server without the complete chain. You must include all certificates to avoid connection errors.
Open the downloaded file in a text editor. Confirm that it includes one or more certificates, each wrapped in
-----BEGIN CERTIFICATE----- and -----END CERTIFICATE-----.
 Open the downloaded certificate using a text editor
Open the downloaded certificate using a text editor
Copy the full certificate content, including all BEGIN/END blocks.
After you copy the certificate chain, you can configure the HTTP connection in Workato to complete the setup.
# Configure the HTTP connection
Complete the following steps to configure the HTTP connection:
Click Create > Connection.
Search for and select HTTP on the New connection page.
Provide a name for your connection in the Connection name field.
Complete the required fields. Refer to the HTTP connection setup documentation for more information.
Set the Use custom TLS/SSL certificate settings field to Yes.
Paste the downloaded certificate chain in the TLS server custom CA certificate field.
SEPARATE MULTIPLE CERTIFICATES
Separate each certificate with a blank line if the chain includes more than one.
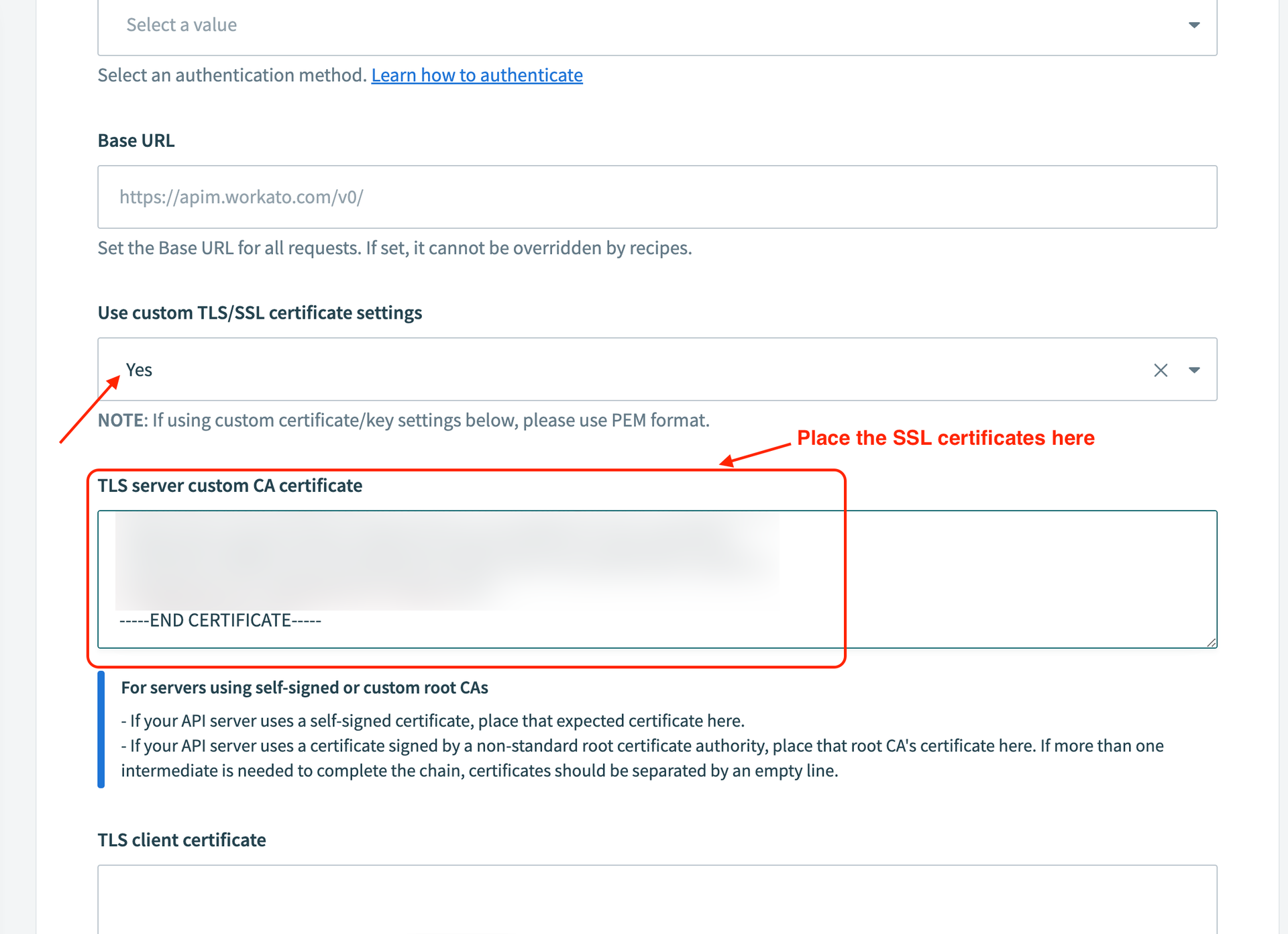 Paste the downloaded certificate contents
Paste the downloaded certificate contents
Click Connect.
The connector should succeed if the certificate chain is valid and complete.
# Troubleshoot certificate errors
The HTTP connector may return the following error when the certificate chain is incomplete:
SSL_connect returned=1 errno=0 state=error: certificate verify failed (unable to get issuer certificate)
The error usually indicates a missing or misconfigured certificate in the chain when the connection already uses custom CA certificates.
Complete the following steps to resolve this error:
Ensure that you provide the full certificate chain in the TLS server custom CA certificate field. Include the following in order, and separate each certificate with a blank line:
- The server certificate
- Any intermediate certificates
- The root certificate
Verify the certificate chain configuration. A complete and correctly ordered chain should work with the connector and with external tools such as Postman or cURL.
Check the certificate chain with a tool such as KeyCDN SSL Checker (opens new window) to confirm that the target server returns a valid and complete chain.
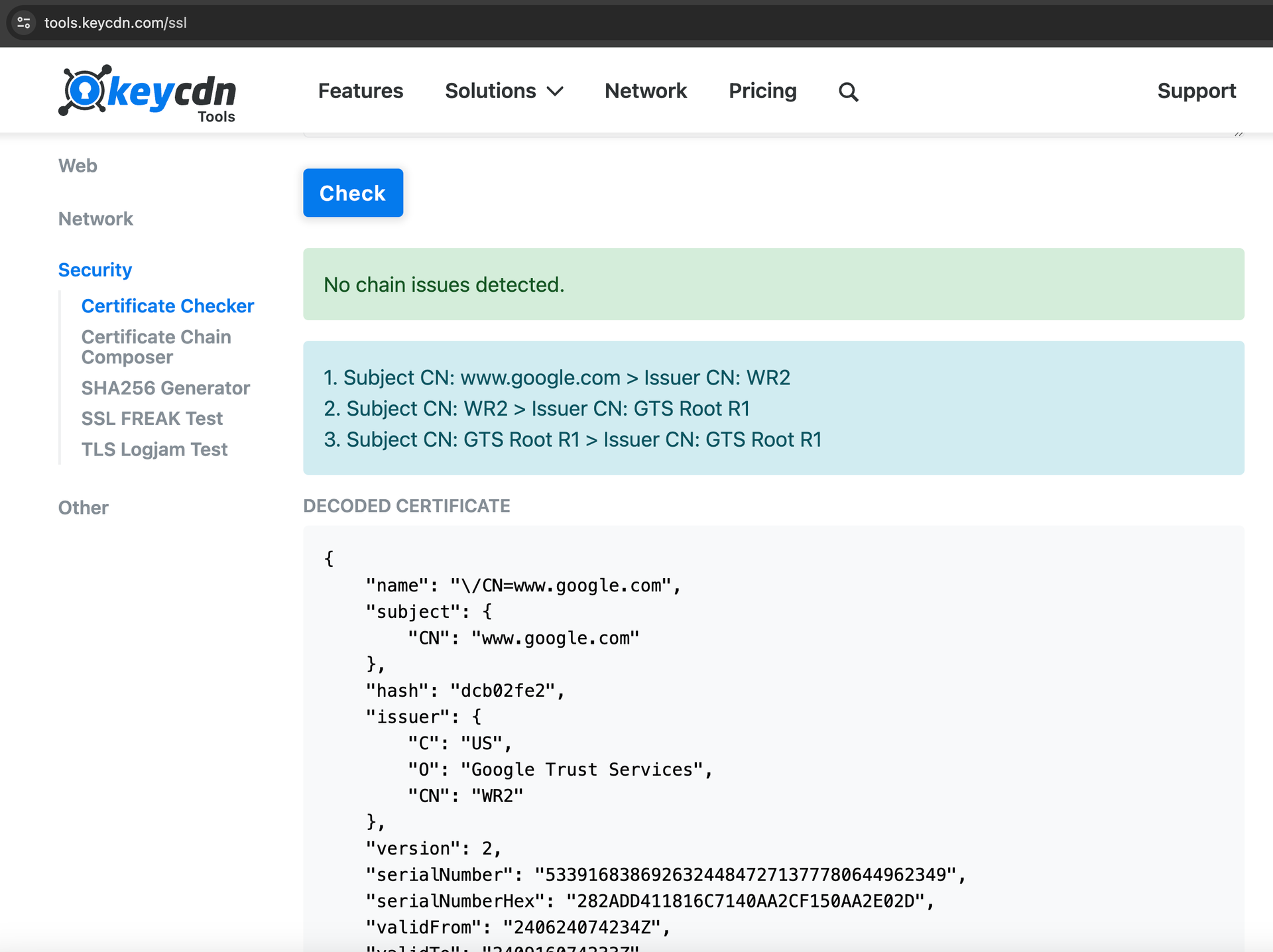 Example of a certificate chain check for
Example of a certificate chain check for https://www.google.com
Last updated: 5/26/2025, 3:37:00 AM