# Azure Private Link
Azure Private Link (opens new window) connections provide secure access to OPA-capable connectors and Workato's API platform by ensuring that network traffic to your environments remains isolated from the public internet.
Use this guide to configure a private connection between the Workato multi-tenant cloud and an Azure Virtual Network (VNet) using Azure Private Link.
FEATURE AVAILABILITY
Azure Private Link connectivity is available to direct customers and embed partners on specific pricing plans. Refer to your pricing plan and contract to learn more.
# Connection structure
Azure Private Link connections to Workato use a three-tier architecture:
A consumer VNet connects through either a Private Link APIM gateway (
apim.workatopc.com) or an on-prem agent that creates websocket tunnels using private SG3/SG4 gateways.The Transit VNet uses a site-to-site VPN that spans multiple Availability Zones to connect to the Workato Transit Virtual Private Cloud (VPC).
The Transit VPC connects to the Workato Platform VPC using Private Link endpoints.
The following diagram shows the connection structure of the consumer VNet to Workato VPC Private Link setup:
# Connect a consumer VNet to the Workato VPC
Connecting a consumer VNet to the Workato VPC using Azure Private Link consists of the following steps:
# Enable Private Link in Workato
Contact your Customer Success Manager with your Azure subscription ID to enable Private Link. Refer to the Microsoft Get subscription and tenant IDs in the Azure portal (opens new window) guide to retrieve your subscription ID.
Save the Resource IDs and DNS names provided by Workato. For example:
# Create Azure Private Link endpoints
Complete the following steps to create each of the required Azure Private Link endpoints:
Open the Microsoft Azure portal and go to Network foundation > Private Link > Private endpoints.
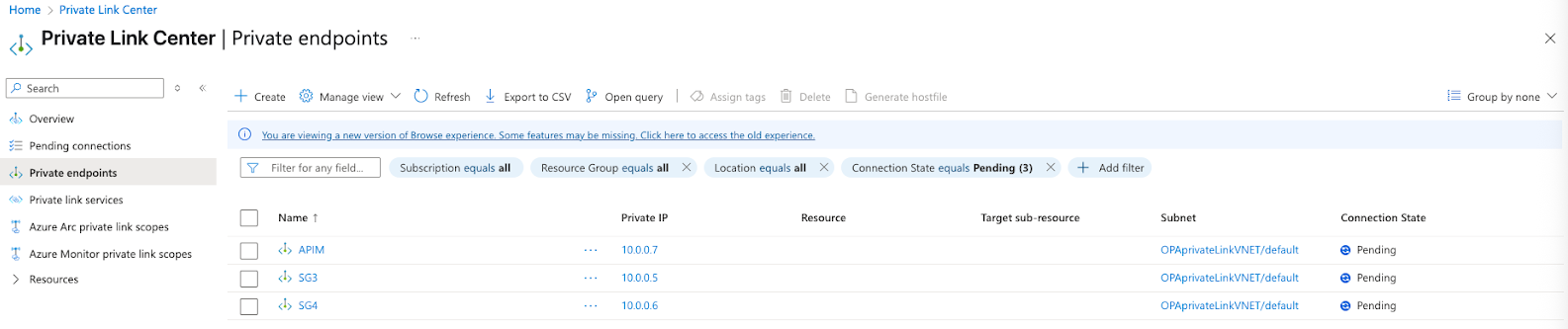 Azure Private endpoints page
Azure Private endpoints page
Create an endpoint
Click + Create.
Select a Subscription and Resource group.
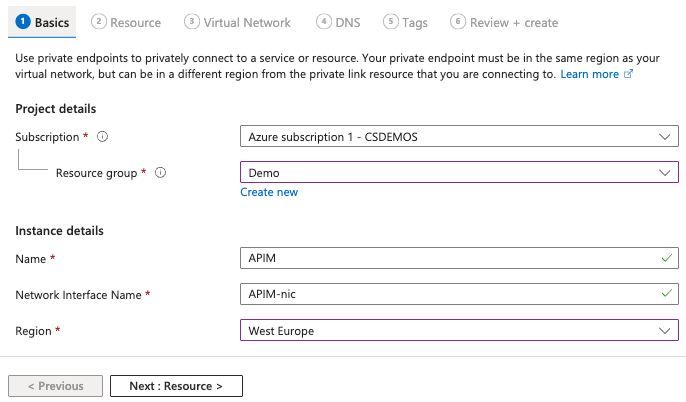 Basics page configuration
Basics page configuration
Enter a Name for the endpoint, such as APIM, SG3, or SG4. The Network Interface Name field is filled in automatically.
Optional. Edit the Network Interface Name. This field is generated automatically based on the provided Name.
Select the Region for your Azure VNet.
Click Next: Resource.
Set the Connection method to Connect to an Azure resource by resource ID or alias.
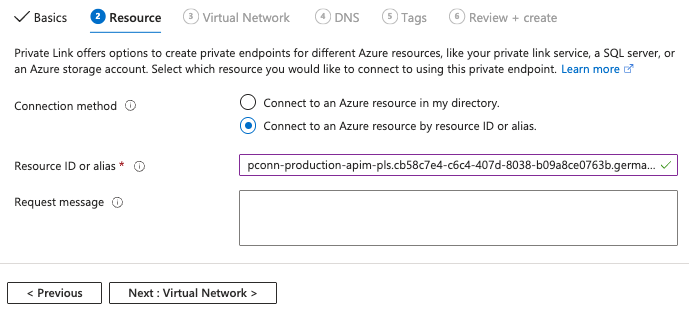 Resource page configuration
Resource page configuration
Enter the Resource ID provided by Workato.
Click Next: Virtual Network, then select the Virtual network that you plan to use.
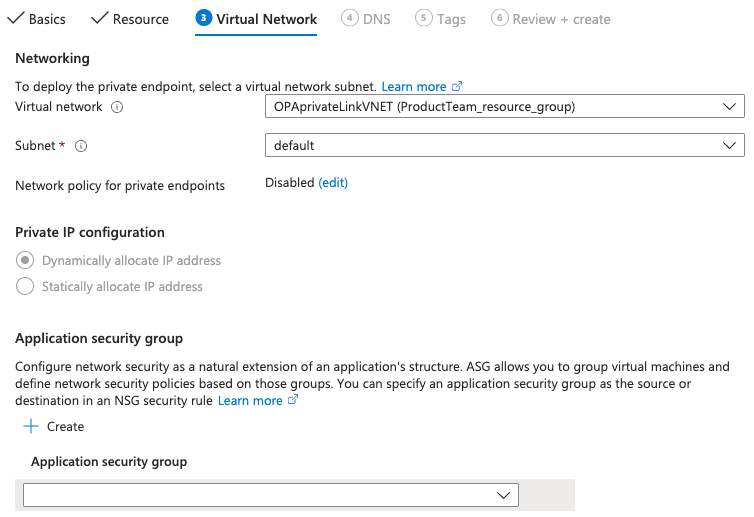 Virtual Network page configuration
Virtual Network page configuration
Click Next: DNS, then set Integrate with private DNS zone to No.
Go to the Review + create tab and ensure the information displayed is correct.
Click Create to create the endpoint.
Create a private DNS zone
Go to Network foundation > DNS > Private DNS zones 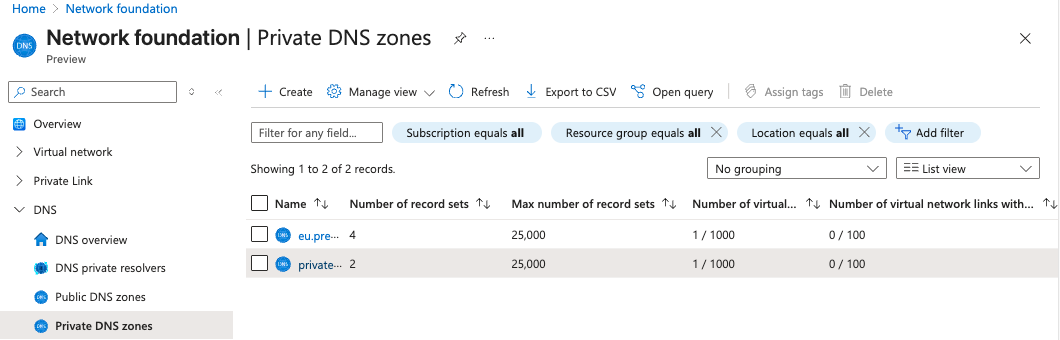 The Private DNS zones page
The Private DNS zones page
Click + Create.
Select a Subscription and Resource group.
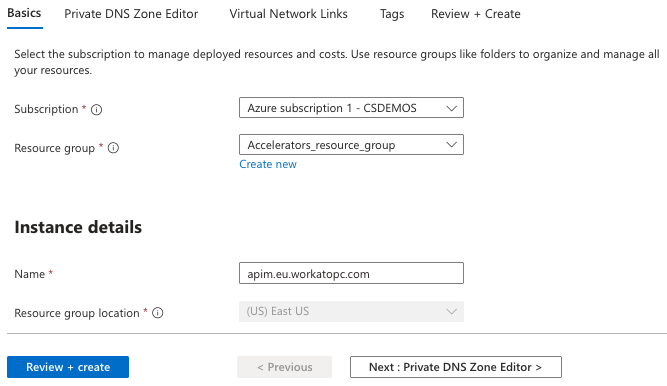 Basics page configuration
Basics page configuration
Enter the DNS name provided by Workato in the Name field. For example apim.workatopc.com.
Go to the Virtual Network Links tab.
Click + Add Virtual Network Link.
Provide the Link name, Subscription, and Virtual Network for the zone.
Click Create.
Go to the Review + create tab and ensure the information displayed is correct.
Click Create to create the zone.
Create a recordset
Select the newly created zone.
 Select the newly created zone.
Select the newly created zone.
Go to DNS Management > Recordsets.
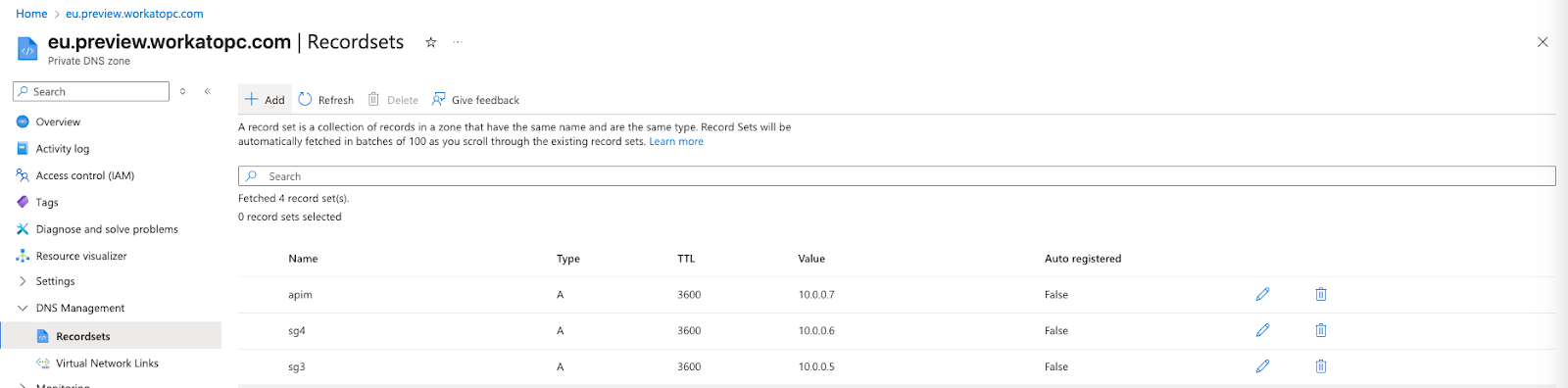 Go to DNS Management > Recordsets.
Go to DNS Management > Recordsets.
Click + Add.
Enter a Name for the recordset and enter the endpoint's Private IP in the IP address field. You can retrieve an endpoint's Private IP on the Network foundation > Private Link > Private endpoints page.
Click Add.
Wait for Workato to accept the endpoints and set them to Active. You can view an endpoint's status on the Network foundation > Private Link > Private endpoints page.
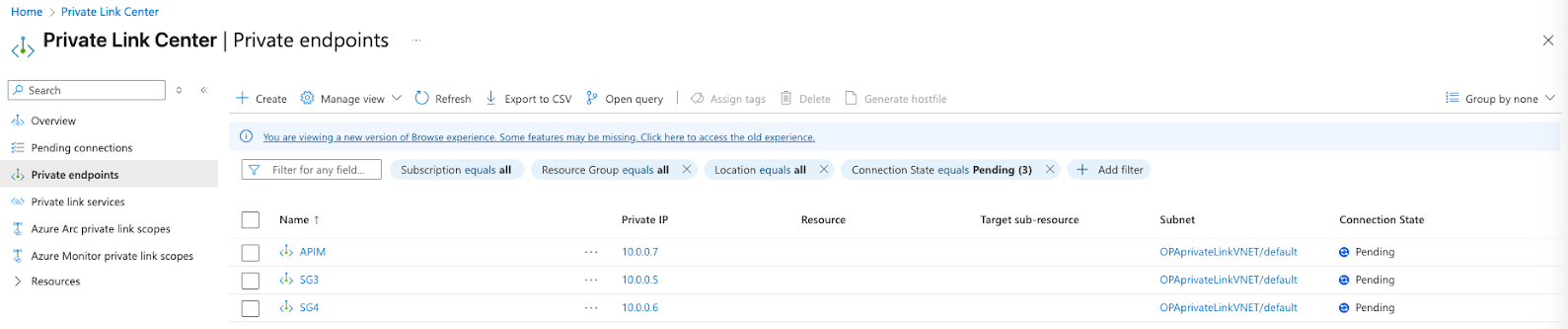 Pending endpoints
Pending endpoints
# Configure an OPA connection
Workato uses OPA to create websocket tunnels from the consumer VNet to the Workato Transit VNet using the SG3 and SG4 gateways. Refer to the Connection structure section for more information.
Complete the following steps to configure OPA for Azure Private Link:
Install an on-prem agent on a machine within the consumer VNet. Refer to the Add an agent to an on-prem group guide to install an OPA.
Ensure the machine running the OPA can reach the private SG3 and SG4 gateways over port 443. Firewalls or proxies that block outbound HTTPS can prevent the agent from connecting. Refer to the Set up proxy access for your on-prem agent guide for more information about OPA proxy settings.
Complete the following OS-specific steps to configure the OPA's activation parameters:
Activate the on-prem agent. The agent automatically connects to the SG3 and SG4 private link gateways. Refer to the Run an on-prem agent guide for information about how to activate OPA for your operating system.
# Configure an API platform connection
Use the Private Link DNS for your data center to access API endpoints using Private Link. For example, use the apim.workatopc.com DNS instead of the standard Workato apim.workato.com DNS. Ensure the machine making the request can reach the private APIM gateway. Firewalls or proxies that block outbound HTTPS can cause the request to fail.
Last updated: 1/20/2026, 8:31:14 PM