# SAML-based single sign-on authentication
Enforcing SAML-based single sign-on (SSO) authentication for your Workflow apps portal enhances security and user experience.
With SAML SSO, a trusted identity provider (IdP) manages authentication, implementing robust security measures and reducing the risk of password-related breaches. Your organization can enforce SAML-based authentication to comply with internal security policies and regulatory requirements, ensuring only authorized users access sensitive Workflow apps.
SAML-based SSO also streamlines the user experience by allowing users to sign in once and access multiple applications without separate logins. Additionally, it allows centralized management of user identities and access controls through the IdP, ensuring consistent application of access policies.
 Sign in to the Workflow apps portal through SAML-based SSO
Sign in to the Workflow apps portal through SAML-based SSO
# Key features of SAML-based SSO for Workflow apps
SAML-based SSO for Workflow apps offers the following key features:
Just-in-Time (JIT) Provisioning
When SAML-based SSO is enforced, you can enable JIT provisioning to automatically create user accounts in the Workflow apps portal when they first sign in through SSO. This eliminates the need for administrators to manually create accounts, which saves time and ensures that user information is always current.
Customizable attributes
SAML-based SSO supports the inclusion of custom attributes, such as group memberships and timeout duration, to tailor user experiences and access levels in your Workflow apps portal.
Selective enforcement
Your organization can choose to enforce SAML-based authentication for all users or only for specified domains. This flexibility allows for compliance with organizational policies while accommodating external users who may not have accounts with the identity provider.
# Compatible identity providers
Workflow apps supports SAML-based SSO with various identity providers (IdPs), including but not limited to:
- Google Workspace
- Microsoft Entra ID
- CyberArk Identity
- Okta
- OneLogin
# How it works
To enable SAML-based SSO authentication, your IdP and the Workflow apps portal must exchange SAML metadata. This involves setting up a SAML application in your IdP with specific values, such as the single sign-on URL and metadata URL. User group syncing does not take effect immediately upon configuration in Workato. Group syncing is enforced each time a user signs into the portal through their IdP.
The process of enabling SSO can vary based on your specific IdP. Refer to the Enforce SAML-based SSO authentication for Okta guide to learn how to enable this capability for Okta. This guide includes instructions for enabling user groups sync, which allows you to sync group assignments between the Workflow apps portal and your IdP.
# Set up SAML-based authentication
VIRTUAL PRIVATE WORKATO (VPW) CUSTOMERS
This feature requires configuration steps that are specific to your Virtual Private Workato (VPW) instance. If you are a VPW customer, refer to your VPW private documentation for the configuration details for your instances.
Sign in to your Workato account.
Go to Platform > Workflow apps portal > Settings > Security.
In the Authentication method field, select SAML based SSO.
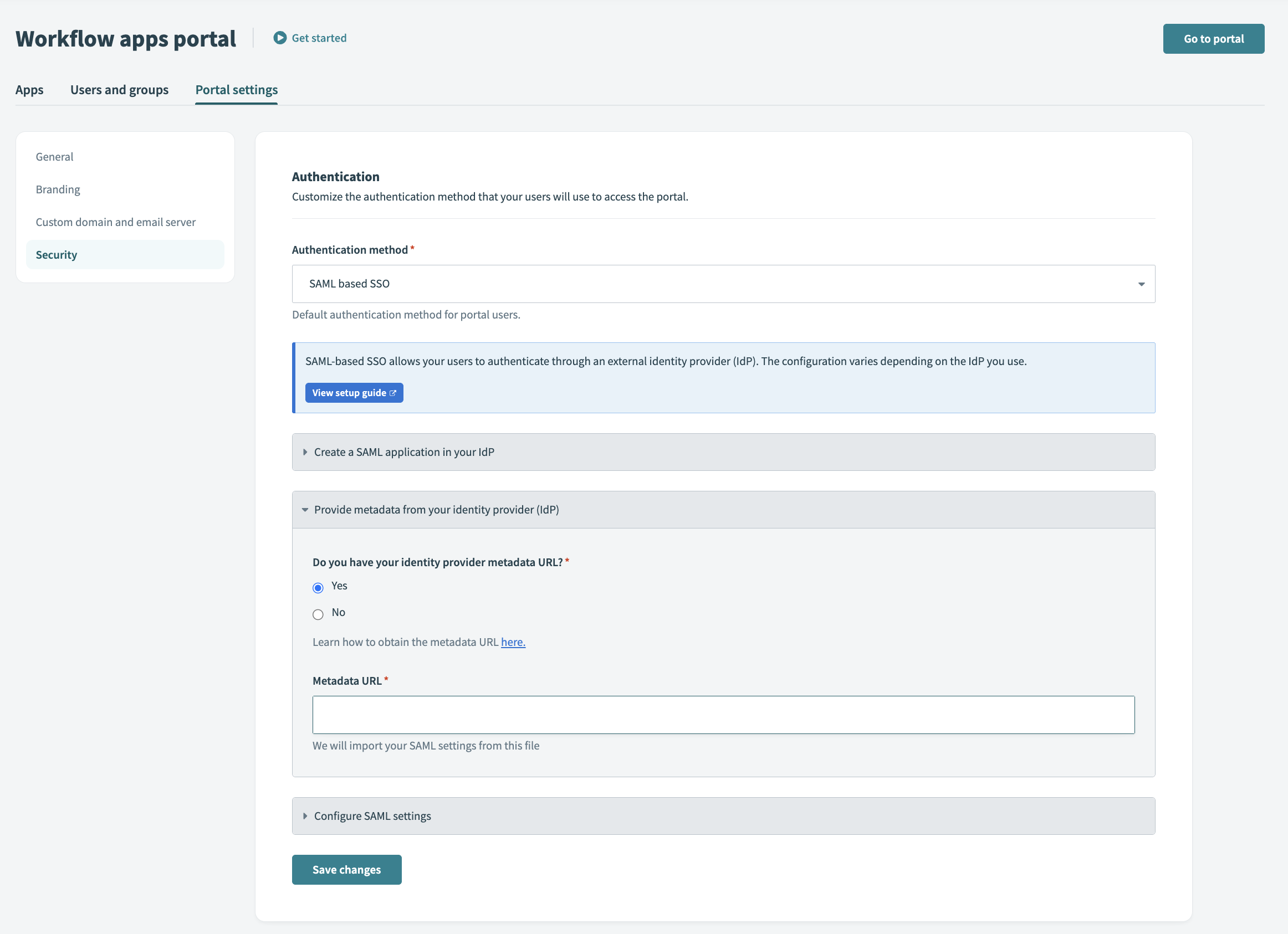 Workato SAML setup
Workato SAML setup
After you select SAML based SSO, the portal settings display the Single Sign-On URL and Audience URI (SP Entity ID). Use these values to set up a SAML application in your IdP.
The Single Sign-On URL and Audience URI (SP Entity ID) formats vary and are unique to your Workflow apps portal subdomain/domain and the data center in which your account is located.
Provide metadata from your IdP. In the Do you have your identity provider metadata URL field, select Yes or No.
In the Enforce SAML authentication for field, decide whether to enforce SAML authentication for all Workflow apps users or only specific domains.
Users outside those domains can sign in using password authentication. This approach is useful for complying with organizational SSO policies while allowing external users without an identity provider account to access Workflow apps.
Optionally, click Enable JIT (Just-In-Time) provisioning to automatically add users to the portal after identity provider authentication.
When JIT is enabled, any user signing in to Workato through SSO for the first time is automatically added to the portal.
Optionally, click Enable user groups syncing to sync user groups from your IdP. This step is mandatory if you plan to manage user groups through your IdP.
User group syncing does not take effect immediately. Group syncing is enforced each time a user signs into the portal through their IdP.
If you plan to enable user groups syncing
Specify the following SAML attributes in your identity provider:
| Name | Value | |
|---|---|---|
| Attribute 1 | workato_app_user_name | user.displayName |
| Attribute 2 | workato_app_user_groups | appuser.workato_app_user_groups |
Optionally, customize the session duration for the Workflow apps portal by modifying the SessionNotOnOrAfter parameter in your identity provider. Otherwise, the default session timeout is seven days if you haven't enabled group syncing through your IdP. When group syncing is enabled through your IdP, the default session timeout is one day if you don't customize this parameter.
Refer to your IdP's documentation to learn how to enable this capability for your app integration.
Click Save changes.
Last updated: 1/23/2026, 5:45:35 PM