# System for Cross-domain Identity Management (SCIM 2.0)
Workato supports the System for Cross-domain Identity Management (SCIM 2.0) in accordance with the IETF SCIM specification (opens new window), to manage user identity information. The implementation of the SCIM 2.0 protocol ensures that we securely automate the exchange of user identity data between your organization's identity provider and Workato. This enables automatic enterprise-level provisioning and deprovisioning of accounts and user profile management from your identity provider, such as Okta or OneLogin.
FEATURE AVAILABILITY
SCIM 2.0 is included in specific pricing plans for direct customers and is available by default for Embedded partners and their end customers. Refer to your pricing plan and contract to learn more.
SUMMARY
- Workato supports SCIM 2.0 for automated user identity data exchange with identity providers like Okta, OneLogin, and Microsoft Entra ID.
- SCIM 2.0 offers automatic user provisioning, deprovisioning, and updates to user attributes through your identity provider.
- SCIM 2.0 usage requires its enablement in Workato and SAML SSO activation in your identity provider.
- Using SCIM involves configuring it in Workato and your identity provider, managing users, and disabling SCIM when not needed.
SCIM 2.0 provides the following benefits to your organization:
- Automatically provisions users with Workato through your identity provider
- Updates custom user attributes, such as
workato_role, directly from the identity provider - Automatically de-provisions users from Workato through your identity provider
- Assigns users to collaborator groups through the
workato_user_groupsattribute
NOTE
SCIM support is an additional feature in Workato.
# Prerequisites
- Enablement in Workato: SCIM 2.0 is part of the Data Monitoring/Advanced Security & Compliance capability. Contact your account executive to learn more about using SCIM 2.0 in your organization.
- Enablement in your identity provider: SAML SSO Enabled on your identity provider
# Using SCIM
To use SCIM, follow these general steps:
In the Okta identity provider:
- Configure SCIM in Okta
- Configure Workato roles
- Provision users
- Convert user assignments to group
- Update users
- Deprovision users
In the OneLogin identity provider:
- Configure for generic SAML applications
- Configure SCIM in OneLogin
- Provision users
- Update users
- Deprovision users
In the Microsoft Entra ID identity provider:
Disable SCIM in Workato, in Okta, in OneLogin, or in Microsoft Entra ID
# FAQ
- What happens when SCIM is enabled and roles are updated manually on Workato?
- What happens when SCIM is enabled and collaborators are removed manually from Workato?
- How can I turn off SCIM provisioning?
- How is deprovisioning handled on Workato with SCIM?
- Why is my profile name unexpectedly long?
# What happens when SCIM is enabled and roles are updated manually on Workato?
Temporary role changes are overwritten from user profile data stored on Workato, the sync can happen in either scenarios:
- User logs in through SAML SSO: role changed by 'saml_auto_sync'
- User’s profile is updated from IdP: role change by 'scim_auto_sync'
# What happens when SCIM is enabled and collaborators are removed manually from Workato?
The user is re-provisioned back into the workspace on the next login, provided that the SCIM connection is valid and the user is not deprovisioned on the organization's identity provider.
# How can I turn off SCIM provisioning?
There are two approaches for turning off SCIM Provisioning:
- Recommended: In your identity provider, disable the SCIM configuration from your provisioning settings. Refer to individual identity provider steps for more detailed information: in Okta, in OneLogin, and in Microsoft Entra ID.
- In Workato, refresh your SCIM token value. This invalidates your existing provisioning token and subsequent SCIM calls fail. Refer to Workato.
# How is deprovisioning handled on Workato with SCIM?
Workato handles deprovisioning in the same manner for users who are deactivated or temporarily suspended from the identity provider, or if their Workato app access is removed. All scenarios trigger a deprovisioning event on Workato, and the user is no longer able to access Workato workspaces. All of their recipes and connections remain accessible to other collaborators.
# Why is my profile name unexpectedly long?
When a user is provisioned in Workato through SCIM or Just-in-Time (JIT) provisioning, their account is created using the userName value provided by your identity provider. Workato then assigns a profile name using additional identity attributes.
If certain attributes are missing during provisioning, Workato may use displayName or userName as a fallback. These fields can include additional context such as job title or department, which may lead to unusually long profile names:
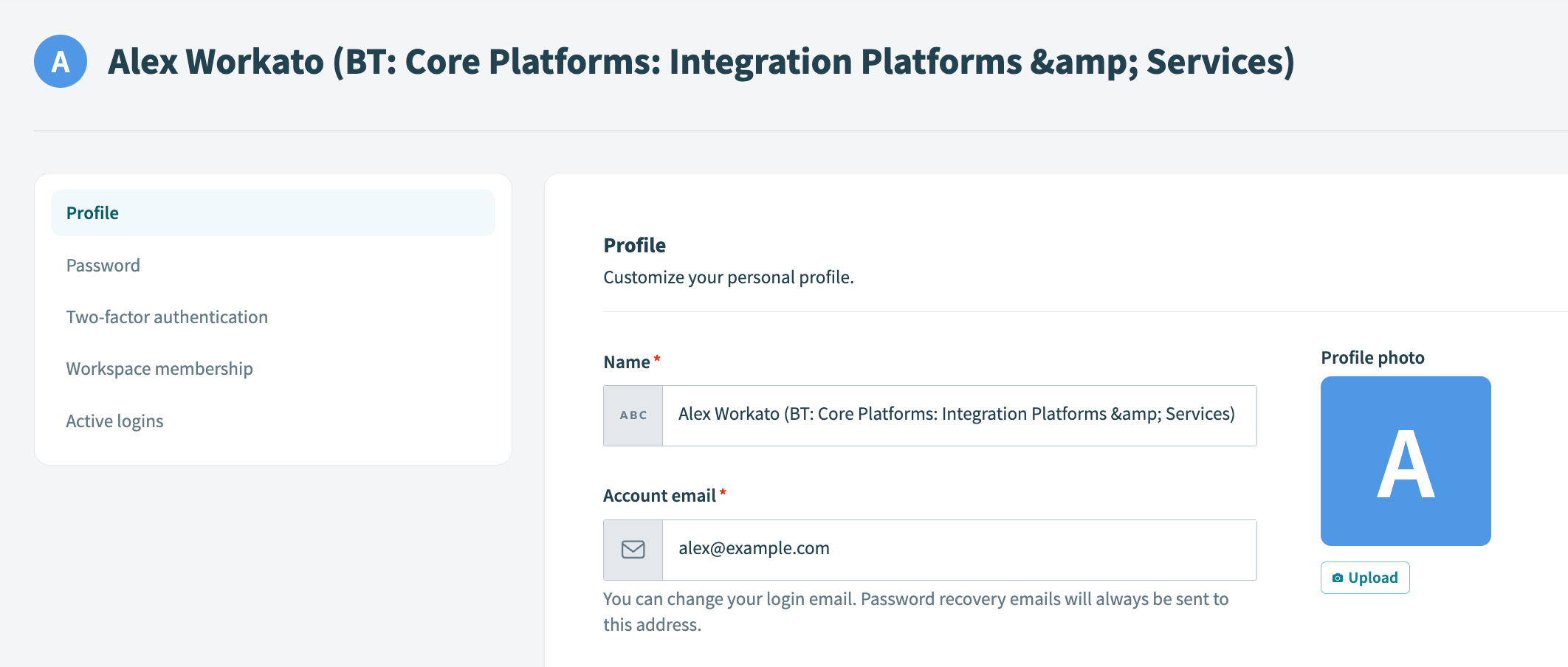 SCIM long profile names
SCIM long profile names
# Why this matters
- A long profile name can cause issues when accessing features like Workato Academy, which enforce limits on name length.
- Profile names aren't updated automatically after initial provisioning, even if SCIM mappings change.
# How to resolve this
- Update your profile name manually in Profile settings in Workato.
- Check how your identity provider is sending name attributes during SCIM provisioning. Using broad fields like
displayNamecan result in long names that may cause issues in the future. - If needed, adjust your attribute mappings to send more concise values when users are provisioned.
Last updated: 10/14/2025, 4:38:57 PM